10 Security Flaws Most Businesses Overlook and How to Fix Them, A Flagship Security Audit and Remediation Guide
When Simulation Meets Reality: The Crisis That Exposed Security Blind Spots
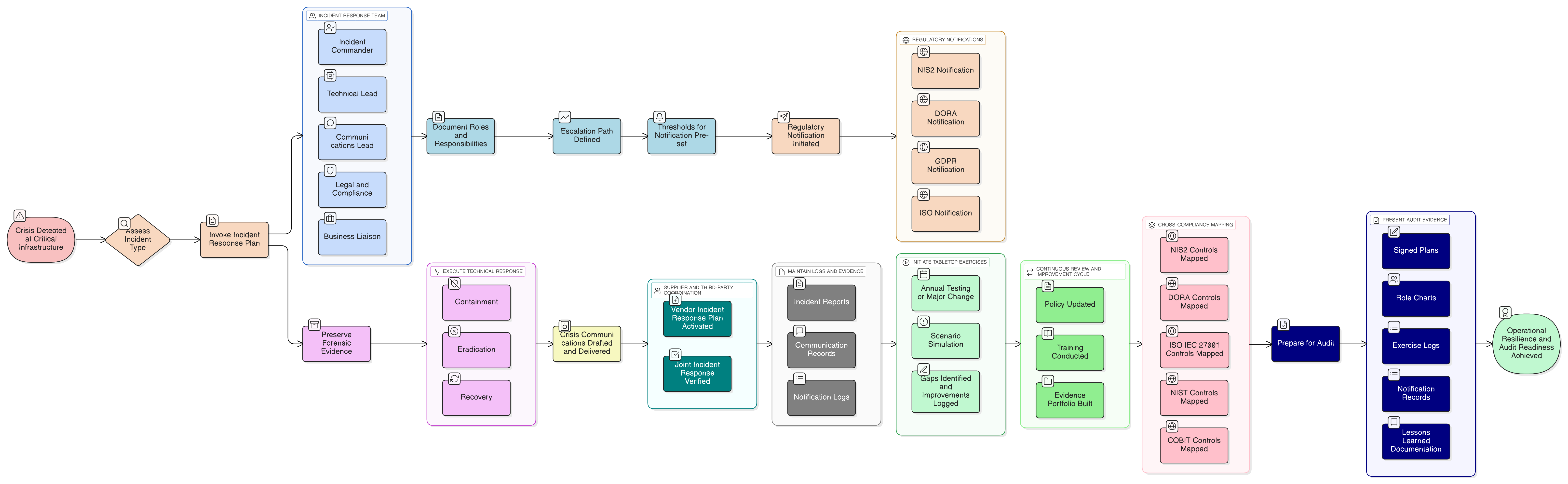
It was 2:00 PM on a Tuesday when Alex, the CISO at a fast-growing FinTech firm, was forced to stop their ransomware simulation. Sparks were flying on Slack, the board watched with growing alarm, and the DORA compliance deadline hovered menacingly. The simulation, intended to be routine, had snowballed into a showcase of vulnerabilities: entry points went undetected, critical assets weren’t prioritized, the communication plan failed, and supplier risk was murky at best.
Not far away, a mid-sized supply chain CISO faced a real-life breach. Phished credentials had let attackers siphon sensitive deal data from cloud apps. The insurance carrier hounded for answers, clients demanded audit trails, and the board wanted quick reassurance. But outdated risk logs, unclear asset ownership, patchwork incident response, and legacy access controls turned the day into an unmitigated disaster.
In both scenarios, the root cause wasn’t malicious insiders or exotic zero-days, it was the same ten evergreen flaws that every auditor, regulator, and attacker knows how to find. Whether you’re gaming out a ransomware hit or living through one, your real exposure isn’t technical, it’s systemic. These are the critical gaps most businesses still harbor, often hidden by policies, checklists, or busywork.
This flagship guide will synthesize the best practical and technical solutions from Clarysec’s expert toolkit. We’ll map every weakness to global frameworks, ISO/IEC 27001:2022, NIS2, GDPR, DORA, NIST, COBIT 19, and show you step-by-step how to remediate not just for compliance, but for real resilience.
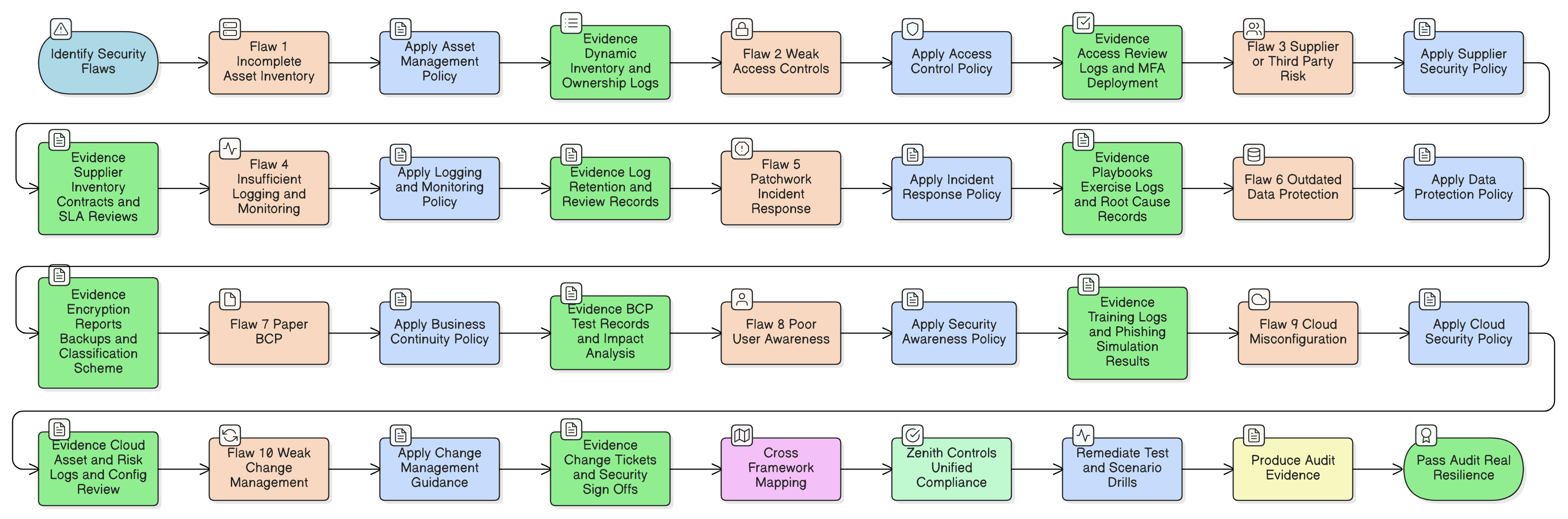
Flaw #1: Incomplete, Outdated Asset Inventory (“Known Unknowns”)
What Happens in the Wild
In a breach or simulation, the first question is: “What was compromised?” Most teams can’t answer. Servers, databases, cloud buckets, microservices, shadow IT, if any are missing from inventory, risk management and response implode.
How Auditors Find It
Auditors demand not just a list of assets, but proof of dynamic updates as business changes, ownership assignments, and cloud resources. They’ll examine onboarding/offboarding, ask how “temporary” services are tracked, and probe for blind spots.
Clarysec’s Fix: Asset Management Policy Asset Management Policy
“All information assets, including cloud resources, must have an assigned owner, detailed classification, and regular verification.” (Section 4.2)
Policy Mapping
- ISO/IEC 27002:2022: Controls 5.9 (Inventory of Assets), 5.10 (Acceptable Use)
- NIST CSF: ID.AM (Asset Management)
- COBIT 19: BAI09.01 (Asset Records)
- DORA: Article 9 (ICT asset mapping)
- GDPR: Data mapping
Zenith Controls Zenith Controls offers dynamic asset tracking workflows mapped to all major regulatory expectations.
| Auditor Perspective | Evidence Required | Pitfalls |
|---|---|---|
| ISO/IEC 27001:2022 | Updated inventory with ownership, review logs | Spreadsheet-only lists |
| NIST | CM-8 artifacts, automated asset scanning | Shadow IT, cloud drift |
| DORA/NIS2 | ICT maps, critical asset documentation | “Temporary” assets missed |
Flaw #2: Broken Access Controls, The Unlocked Digital Front Door
Root Problems
- Privilege Creep: Roles change, permissions never get revoked.
- Weak Authentication: Password policies aren’t enforced; MFA is missing for privileged accounts.
- Zombie Accounts: Contractors, temp staff, and apps retain access long after they should.
What the Best Policies Do
Clarysec’s Access Control Policy Access Control Policy
“Access rights to information and systems must be defined by role, regularly reviewed, promptly revoked for changes. MFA required for privileged access.” (Section 5.1)
Mapping to Controls
- ISO/IEC 27002:2022: 5.16 (Access Rights), 8.2 (Privileged Access), 5.18 (Access Review), 8.5 (Secure Authentication)
- NIST: AC-2 (Account Management)
- COBIT 19: DSS05.04 (Manage Access Rights)
- DORA: Identity and Access Management pillar
Audit Red Flags:
Auditors look for missing reviews, “temporary” admin access lingering, lack of MFA, and fuzzy records of offboarding.
| Flaw | Audit Evidence | Common Pitfall | Remediation Example |
|---|---|---|---|
| Privilege creep | Quarterly access reviews | Dormant accounts | Privileged access tracking, Access Control Policy |
Flaw #3: Unmanaged Supplier & Third-Party Risk
The Modern Breach
Supplier accounts, SaaS tools, vendors, contractors, trusted for years, but never re-reviewed, become vectors for breach and untrackable data flows.
Clarysec’s Third-Party and Supplier Security Policy Third-party and supplier security policy
“All suppliers must be risk-assessed, security terms embedded in contracts, and security performance periodically reviewed.” (Section 7.1)
Compliance Mapping
- ISO/IEC 27002:2022: 5.19 (Supplier Relationships), 5.20 (Procurement)
- ISO/IEC 27036, ISO 22301
- DORA: Supplier and outsourcing, extended subcontractor mappings
- NIS2: Supply chain mandates
Audit Table
| Framework | Auditor’s Focus | Required Evidence |
|---|---|---|
| ISO 27001:2022 | Due diligence, contracts | Supplier inventory, SLA reviews |
| DORA/NIS2 | Security clauses | Ongoing supply chain assessment |
| COBIT/NIST | Vendor risk log | Contracts & monitoring reports |
Flaw #4: Insufficient Logging and Security Monitoring (“Silent Alarms”)
Real-World Impact
When teams try to trace a breach, lack of logs or unstructured data makes forensics impossible, and ongoing attacks go undetected.
Clarysec’s Logging and Monitoring Policy Logging and Monitoring Policy
“All security-relevant events must be logged, protected, retained according to compliance requirements, and reviewed regularly.” (Section 4.4)
Controls Crosswalk
- ISO/IEC 27002:2022: 8.15 (Logging), 8.16 (Monitoring)
- NIST: AU-2 (Event Logging), Detect (DE) function
- DORA/DORA: log retention, anomaly detection
- COBIT 19: DSS05, BAI10
Audit Evidence: Auditors require log retention records, regular review evidence, and proof logs can’t be tampered.
Flaw #5: Patchwork, Unpracticed Incident Response
Scenario
During a breach or a simulation, incident plans exist on paper, but are untested, or only involve IT, not legal, risk, PR, or suppliers.
Clarysec’s Incident Response Policy Incident Response Policy
“Incidents must be managed with multidisciplinary playbooks, exercised regularly, and logged with root cause and response improvement.” (Section 8.3)
Mapping
- ISO/IEC 27002:2022: 6.4 (Incident Management), incident logs
- ISO/IEC 27035, ISO/IEC 22301 (BCM), DORA (incident reporting), GDPR (breach notification, Article 33)
Key Audit Points
| Focus | Evidence Required | Pitfalls |
|---|---|---|
| Plan exists & tested | Exercise logs, logs | No scenario drills |
| Stakeholder roles | Clear escalation chart | “Owned” by IT only |
Flaw #6: Outdated Data Protection, Weak Encryption, Backups, and Classification
Real Impact
Companies still use outdated encryption, weak backup processes, and have spotty data classification. When a breach happens, the inability to identify and protect sensitive data compounds harm.
Clarysec’s Data Protection Policy Data Protection Policy
“Sensitive data must be protected by risk-aligned controls, strong encryption, current backups, and regular review against regulatory requirements.” (Section 3.2)
Policy Mapping
- ISO/IEC 27002:2022: 8.24 (Encryption), 8.25 (Data Masking), 5.12 (Classification)
- GDPR: Article 32
- NIST: SC-13, Privacy Framework
- COBIT: DSS05.08
- ISO/IEC 27701 & 27018 (privacy, cloud specific)
Classification Scheme Example
Public , Internal , Confidential , Restricted
Flaw #7: Business Continuity as a Paper Exercise
What Fails in Practice
BCPs exist, but aren’t tied to real business impact scenarios, aren’t exercised, and never connect to supplier dependencies. When a major outage occurs, confusion reigns.
Clarysec’s Business Continuity Policy Business Continuity Policy
“BC processes must be exercised, mapped to impact analyses, and integrated with supplier plans for operational resilience.” (Section 2.1)
Control Mapping
- ISO/IEC 27002:2022: 5.29 (Business Continuity)
- ISO 22301, NIS2, DORA (Operational Resilience)
Audit Questions:
Evidence of recent BCP test, documented impact analyses, supplier risk reviews.
Flaw #8: Weak User Awareness and Security Training
Common Pitfalls
Security training is seen as a tick-box exercise, not tailored or continuous. Human error stays the top breach driver.
Clarysec’s Security Awareness Policy Security Awareness Policy
“Regular, role-based security training, phishing simulations, and measurement of program effectiveness are mandatory.” (Section 5.6)
Mapping
- ISO/IEC 27002:2022: 6.3 (Awareness, Education, Training)
- GDPR: Article 32
- NIST, COBIT: awareness modules, BAI08.03
Audit Lens:
Proof of training schedules, evidence of targeted refreshers and testing.
Flaw #9: Cloud Security Gaps and Misconfigurations
Modern Risks
Cloud adoption outpaces asset, access, and supplier controls. Misconfigurations, missing asset mapping, and lack of monitoring enable costly breaches.
Clarysec’s Cloud Security Policy Cloud Security Policy
“Cloud resources must be risk-assessed, asset-owned, access-controlled, and monitored with compliance requirements.” (Section 4.7)
Mapping
- ISO/IEC 27002:2022: 8.13 (Cloud Services), 5.9 (Asset Inventory)
- ISO/IEC 27017/27018 (Cloud Security/Privacy)
- DORA: Outsourcing/cloud mandates
Audit Table:
Auditors will review cloud onboarding, supplier risk, access permissions, and monitoring.
Flaw #10: Immature Change Management (“Ready, Fire, Aim” Deployments)
What Goes Wrong
Servers rushed to production bypass security reviews; default credentials, open ports, missing baselines remain. Change tickets lack risk assessment or rollback plans.
Clarysec’s Change Management Guidance:
- Control 8.32 (Change Management)
- Security review required for every major change
- Backout/test plans, stakeholder approval
Mapping
- ISO/IEC 27002:2022: 8.9, 8.32
- NIST, COBIT: CAB and change records, BAI06
- DORA: Major ICT changes mapped to risk and resilience
Audit Evidence:
Sample change tickets, security sign-off, test logs.
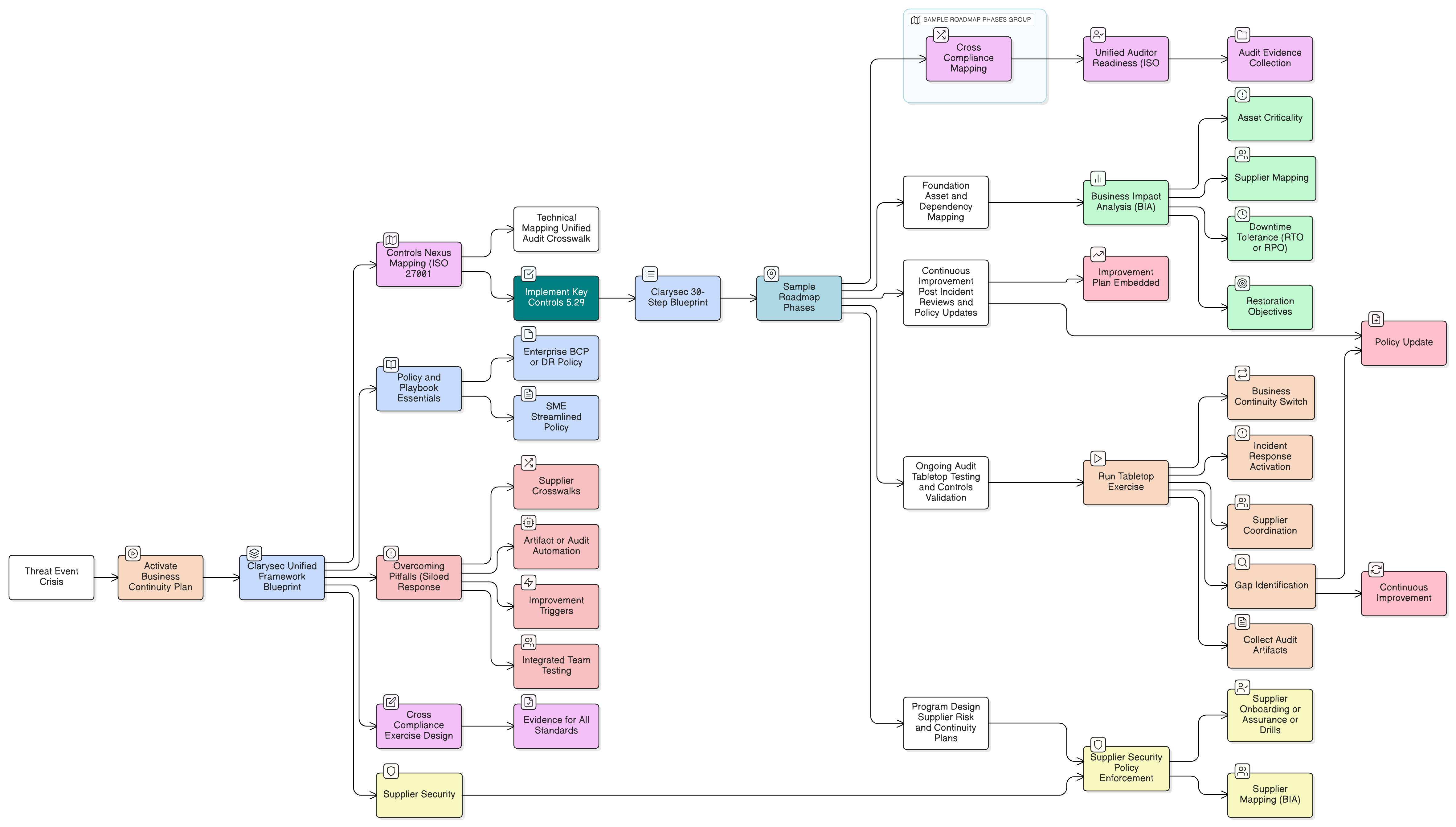
How Clarysec’s Toolkit Accelerates Remediation: From Flaw Discovery to Audit Success
Real resilience begins with a systematic approach favored by auditors and demanded by regulators.
Practical Example: Securing a New Supplier for Cloud-Based Invoicing
- Asset Identification: Use Clarysec’s mapping tools to assign ownership, classify “confidential” data per the Asset Management Policy.
- Supplier Risk Assessment: Score the supplier via Zenith Controls risk template; align with business continuity and data protection policies.
- Access Provisioning: Grant “least privilege” using formal approvals; schedule quarterly reviews.
- Contract Controls: Embed security terms referencing ISO/IEC 27001:2022 and NIS2, as Zenith Controls recommends.
- Logging & Monitoring: Activate log retention and weekly review, documented per Logging and Monitoring Policy.
- Incident Response Integration: Train supplier in scenario-driven incident playbooks.
Each step delivers remediated evidence mapped to every relevant framework, making audits straightforward and passing every lens: technical, operational, and regulatory.
Cross-Framework Mapping: Why Comprehensive Policy and Controls Matter
Auditors don’t just check ISO or DORA in isolation. They want proof of cross-framework evidence:
- ISO/IEC 27001:2022: Risk linkage, asset ownership, updated records.
- NIS2/DORA: Supply chain resilience, incident response, operational continuity.
- GDPR: Data protection, privacy mapping, breach notification.
- NIST/COBIT: Policy alignment, process rigor, change management.
Zenith Controls acts as a crosswalk, mapping each control to its counterparts and audit evidence across all major regimes Zenith Controls.
From Flaws to Fortification: Structured Remediation Flow
A successful security transformation leverages a phased, evidence-driven approach:
| Phase | Action | Evidence Produced |
|---|---|---|
| Discovery | Targeted risk/asset assessment | Inventory, risk logs |
| Policy Foundation | Adopt mapped policies from Clarysec | Signed, implemented policy docs |
| Remediate & Test | Map gaps to controls, run scenario drills | Test logs, audit-ready evidence |
| Cross-Compliance Review | Use Zenith Controls for mapping | Unified control matrix/records |
Zenith Blueprint: An Auditor’s 30-Step Roadmap Zenith Blueprint outlines every step, producing the logs, records, evidence, and role assignments auditors expect.
Common Flaws, Pitfalls, and Clarysec Solutions, Quick Reference Table
| Flaw | Common Pitfall | Clarysec Solution/Policy | Audit Evidence |
|---|---|---|---|
| Incomplete assets | Shadow IT, static list | Asset Management Policy | Dynamic inventory, ownership |
| Weak access controls | Dormant “admin” accounts | Access Control Policy | Review logs, MFA deployment |
| Supplier risk | Contract gaps | Supplier Policy + Zenith Controls | Supplier inventory, audit logs |
| Poor incident plan | Uncoordinated response | Incident Response Policy | Playbook, exercises logged |
| No logging/monitoring | Unnoticed attacks | Logging & Monitoring Policy | Log retention, reviews |
| Weak encryption/data | Outdated controls | Data Protection Policy | Encryption reports, backups |
| BCP on paper only | Untested plans | Business Continuity Policy | Test/exercise records |
| Generic training | Human error persists | Security Awareness Policy | Training logs, phishing tests |
| Cloud misconfig | Permissions drift | Cloud Security Policy | Cloud risk logs, config review |
| Weak change mgmt | Server misconfig, no rollback | Change Management Guidance | Change tickets, sign-offs |
Clarysec’s Strategic Advantage: Why Zenith Controls and Policies Win Audits
- Cross-compliance by design: Controls and policies mapped to ISO, NIS2, DORA, GDPR, NIST, COBIT, no surprises for auditors.
- Modular, enterprise/SME-ready policies: Rapid deployment, real business alignment, proven audit records.
- Evidence kits built-in: Every control generates auditable logs, signatures, and test evidence for every regime.
- Proactive audit preparation: Pass audits for all frameworks, avoid costly gaps and remediation cycles.
Your Next Step: Build Real Resilience, Not Just Pass Audits
Don’t wait for disaster or regulatory knock, take control of your security fundamentals today.
Get started:
- Download the Zenith Controls: The Cross-Compliance Guide Zenith Controls
- Use the Zenith Blueprint: An Auditor’s 30-Step Roadmap Zenith Blueprint
- Request a Clarysec assessment to map your 10 flaws and build a tailored improvement plan.
Your weakest control is your greatest risk, let’s remediate, audit, and secure it, together.
Related Reads:
- How To Design an Audit-Ready ISMS in 30 Steps
- Cross-Compliance Policy Mapping: Why Regulators Love Zenith Controls
Ready to fortify your business and pass every audit?
Contact Clarysec for a strategic ISMS assessment, demo our toolkits, or tailor your enterprise policies, before the next breach or audit rush.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council