Beyond the Firewall: Why Audit-Ready Compliance Demands a Real Management System, ISO 27001, NIS2, and DORA Mapped
The Audit Catastrophe: Why Firewalls Can’t Save Your Compliance
The pre-audit report lands hard, whether in Fortune 500 finance or a fintech disruptor, the pain is universal. Sarah, CISO at FinCorp Innovations, stared at a mountain of red ink despite a seven-figure investment in cybersecurity: next-gen firewalls, top-tier endpoint security, and ironclad MFA rolled out across all users. The tech was flawless. Yet, as her ISO/IEC 27001:2022 auditor delivered the verdict, it became clear, technology alone wasn’t enough.
Major nonconformities cited:
- No demonstrable top management commitment.
- Ad hoc risk assessment, disconnected from business context.
- Supplier security managed via informal emails, no risk evaluation or contract review.
Sarah’s “secure fortress” failed the audit not because it lacked technology, but because it lacked evidence of a holistic, strategic management system. The same nightmare plays out across regulated industries under NIS2 and DORA. It’s not a technical failing, but a business-wide governance breakdown. Firewalls don’t map to strategic guidance, supplier risk management, or lessons learned. Compliance frameworks demand more.
Why IT-Driven Compliance Fails: Untangling the Business Risk
Many organizations fall into the false comfort of treating compliance as an IT project, software deployed, users trained, logs shipped off to SIEM. Yet, ISO/IEC 27001:2022, NIS2, and DORA demand evidence of management system thinking:
- Board and executive involvement in security decisions.
- Documented, business-aligned risk assessments.
- Systematic supplier governance, contract management, and due diligence.
- Structured, continual improvement cycles with lessons learned across the org.
Clarysec’s years of audit experience confirm it: compliance is not a firewall. Passing an audit is about enterprise-wide ownership, documented process, cross-functional engagement, and continuous improvement.
“Management’s commitment and the integration of information security into organizational processes are central to compliance. A documented management system approach, supported by evidence of implementation and continual improvement, distinguishes mature organizations from checkbox compliance efforts.”
(Zenith Controls: Cross-Compliance Guide, ISMS Clause 5 context)
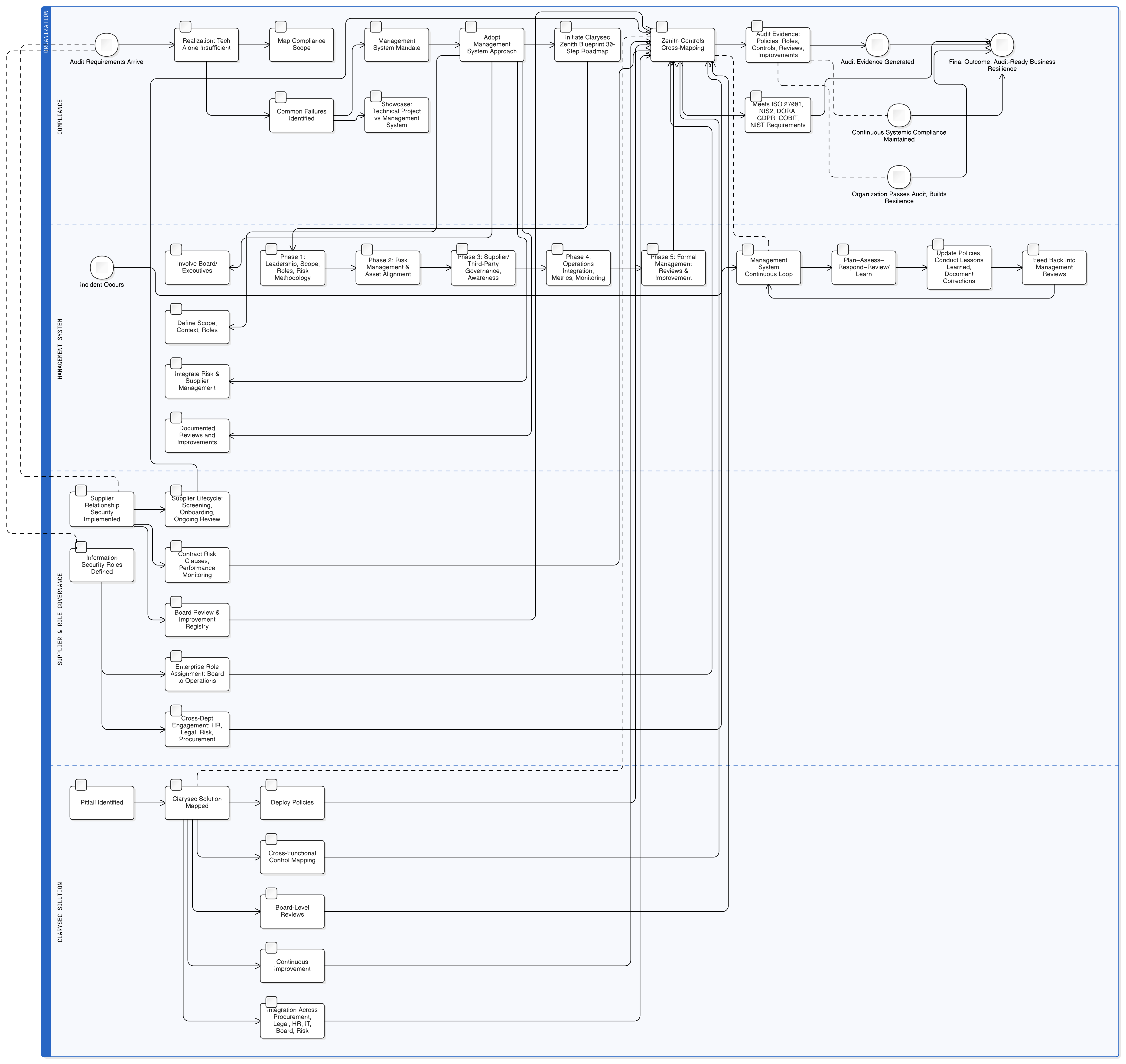
Management System vs. Technical Project
An ISMS (Information Security Management System) is not a project, it’s a continuous, cyclical discipline tied to strategy, risk, and improvement. It starts with governance, scoping, and leadership alignment, not in the server room.
- IT Project: One-and-done checklist (deploy firewall, update software).
- ISMS: Boardroom-driven system (define context, set objectives, assign roles, review and improve).
Auditors seek not just technical controls, but the “why” behind every process, leadership commitment, integration with business strategy, and documented, evolving systems.
Failure Stories: Real-World Audit Breakdowns
Let’s walk through what audit failure actually looks like.
The FinCorp Innovations Case Study
| Audit Finding | Why It Failed |
|---|---|
| No documented ISMS reviews by top management | Auditors expect executive/board engagement; IT-only scope is insufficient |
| Risk assessments limited to vulnerabilities | Must include suppliers, HR, process, legal risks, not just technical |
| Supplier contracts lacked security diligence | Supplier security is an enterprise responsibility per ISO/IEC 27036 |
| No evidence of corrective-action tracking | ISO/IEC 27001 Clause 10 requires demonstrable improvement |
| No ISMS effectiveness measurement | Audit expects ongoing review, not a static project |
Despite technical excellence, the absence of business-driven management system elements, ownership, governance, improvement, put certification out of reach.
Unpacking the “Beyond IT” Mandate: How Modern Standards Expand Scope
NIS2, DORA, and ISO 27001 are not technical checklists. They enforce operating models for digital resilience that stretch across business lines:
- Executive commitment: Integration with strategic objectives and board oversight.
- Risk management: Formalized methodologies for business, supplier, legal, and compliance risk.
- Supplier governance: Systematic onboarding, due diligence, and contract security clauses.
- Continuous improvement: Active lessons learned, corrective actions, post-incident review.
Clarysec’s Zenith Controls unify this scope, cross-mapping to ISO/IEC 27014 (governance), ISO/IEC 27005 (risk), and ISO/IEC 27036 (supplier management), ensuring the business-wide discipline auditors demand.
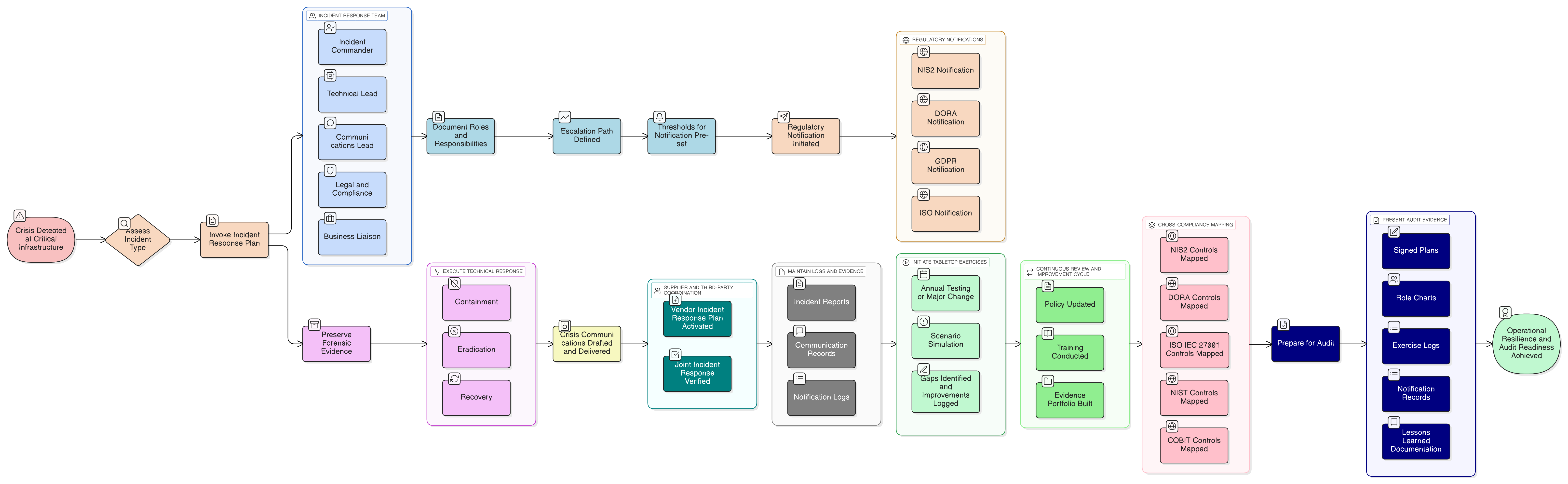
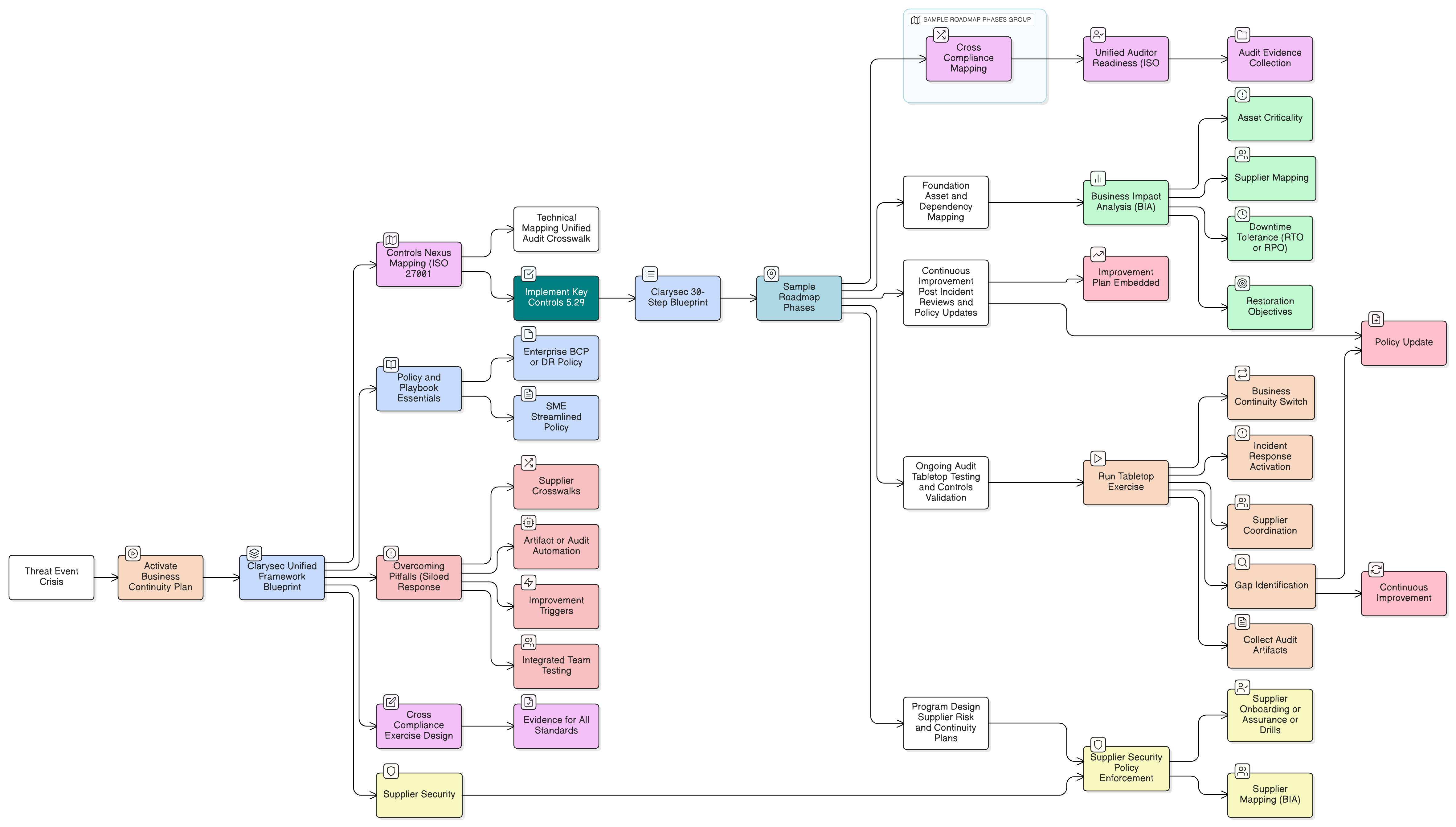
From Project to System: The Zenith Blueprint 30-Step Roadmap
Clarysec’s “Zenith Blueprint: An Auditor’s 30-Step ISMS Roadmap” closes the management gap, offering a sequenced, practical workflow for organizations ready to move beyond tech silos.
Roadmap Highlights
Starts at the Top:
- Executive sponsorship and strategic alignment.
- Scope and context definition.
- Clear role assignment beyond IT.
Full Enterprise Integration:
- Supplier, HR, procurement, legal, risk management embedded.
- Cross-department collaboration.
Process and Improvement:
- Scheduled reviews, documented corrective actions, continual improvement cycles.
Key Phases
| Phase | Steps | Focus |
|---|---|---|
| 1 | 1-5 | Top management support, ISMS scope, context, roles, risk methodology |
| 2 | 6-10 | Risk management, asset identification, risk analysis, treatment, and alignment |
| 3 | 11-20 | Supplier/third-party assessment, business-wide awareness, contract security |
| 4 | 21-26 | Operations integration, ongoing monitoring, performance metrics |
| 5 | 27-30 | Formal management reviews, lessons learned, organizational improvement |
Auditor outcome: Not just evidence of IT process, but system-wide ownership, accountability, documented improvement, and traceability to business value.
Management System in Action: Controls that Break the IT Silo
Auditors focus on how individual controls integrate into the broader system. Two critical controls demonstrate the difference.
1. Information Security Roles & Responsibilities (ISO/IEC 27002:2022 Control 5.1)
Control Mandate:
Clear security roles and responsibilities assigned organization-wide, from board to operational staff.
Context and Audit Expectation:
- Spans HR, legal, risk, procurement, not just IT.
- Requires documentation (role descriptions, periodic reviews, RACI charts).
- Aligns with governing frameworks: ISO/IEC 27014, COBIT 19, NIS2, DORA.
Typical Auditor Checkpoints:
- Documented leadership roles.
- Evidence of cross-functional integration.
- Traceability between board directives and operational execution.
2. Supplier Relationship Security (ISO/IEC 27002:2022 Control 5.19)
Control Mandate:
Govern supplier/third-party access, onboarding, contracts, and ongoing monitoring.
Cross-Compliance Mapping:
- ISO/IEC 27036: Supplier lifecycle management (screening, onboarding, termination).
- NIS2: Supply chain risk built into governance.
- DORA: Outsourcing and ICT risk as operational resilience priority.
- GDPR: Processor contracts with defined information security and breach notification clauses.
| Framework | Auditor Perspective |
|---|---|
| ISO/IEC 27001 | Evaluate supplier due diligence, contract terms, monitoring processes |
| NIS2 | Risk management for supply chain impacts, not just technical integrations |
| DORA | Third-party/outsourcing risk, board-level review |
| COBIT 19 | Control monitoring and supplier performance |
| GDPR | Data processing agreements, breach notification workflow |
These controls require active ownership and business leadership. A checklist won’t cut it, auditors seek systemic engagement.
Cross-Compliant Controls: The Clarysec Compass for Multi-Framework Alignment
Clarysec’s Zenith Controls let you map controls across standards, exposing the business-wide discipline that powers reliable compliance.
“Supplier security is an organizational management activity involving risk identification, due diligence, contract structuring, and ongoing assurance; mapped across ISO/IEC 27001:2022 (cl.8), ISO/IEC 27036, NIS2 Art. 21, DORA Art. 28, COBIT 19 DSS02, and NIST SP 800-161.”
(Zenith Controls: Supplier & Third-Party Security section)
Crosswalk Table: Supplier Security Across Frameworks
| ISO/IEC 27002:2022 | NIS2 | DORA | GDPR | COBIT 19 | What Auditors Ask |
|---|---|---|---|---|---|
| 5.19 Supplier Security | Art. 21 Supply Chain Security | Art. 28 ICT Third-Party Risk | Art. 28 Processor Contracts | DSS02 Third-Party Services | Evidence of supplier risk management, monitoring, board review, contract security clauses |
Policy Foundation: Real Policies for Holistic Compliance
Documentation is the backbone of a management system, policies must transcend IT.
Clarysec policies integrate cross-compliance best practices:
“Suppliers and third parties must be subject to security screenings and risk assessments prior to engagement; contract clauses ensuring security and compliance with legal and regulatory obligations are required, and ongoing performance is monitored. Corrective actions and improvements are executed where risk or performance issues are identified.”
(Section 3.2, Supplier Assessment, Third-party and supplier security policy)
These policies anchor risk, onboarding, legal drafting, and ongoing review, offering auditors the hard evidence of enterprise-wide engagement needed to pass any assessment.
Hands-On Scenario: Building Audit-Ready Supplier Security
How can a technical team evolve into a management system?
Step-by-step:
- Policy Alignment: Activate Clarysec’s “Third-party and supplier security policy” for cross-department consensus on roles and minimum contract terms.
- Risk-Driven Assessment: Use the Zenith Blueprint roadmap to systematize supplier screening, onboarding documentation, and periodic reassessment.
- Control Mapping: Employ Zenith Controls crosswalks for requirements under NIS2, DORA, GDPR, processor contract content, supply chain resilience evidence.
- Board Review Integration: Include supplier risk in ISMS management reviews, with top management action tracking, improvement registry, and ongoing audit prep.
End result:
The auditor no longer sees IT checklists. They see a documented, business-owned management process integrated across procurement, legal, HR, and board oversight.
What Auditors Really Want: The Multi-Standard Lens
Auditors from different standards probe for systemic evidence:
| Auditor Background | Focus and Evidence Sought |
|---|---|
| ISO/IEC 27001 | Organizational context (Clause 4), top management commitment (Clause 5), documented policies, enterprise risk registers, continual improvement |
| NIS2 | Supply chain and business risk integration, governance linkages, management of external partners |
| DORA | Operational resilience, outsourcing/ICT risk, incident response and board-level review |
| ISACA/COBIT 19 | Alignment between IT and business, control integration, board accountability, performance measurement |
“Management accountability for supplier risk must be demonstrated through board meeting minutes, explicit supplier review records, and evidence of lessons learned/corrective actions from real incidents or supplier issues.”
(Zenith Controls: Audit Methodology overview)
Clarysec’s toolkit ensures all this evidence is systematically generated and mapped for any framework.
Resilience Beyond IT: Business Continuity and Incident Learning
ICT Readiness for Business Continuity: A Cross-Compliance Example
What do auditors expect from controls like ISO/IEC 27002:2022 Control 5.30?
| Auditor Background | Focus Area | Supporting Frameworks |
|---|---|---|
| ISO/IEC 27001 | Business Impact Analysis (BIA), Recovery Time Objectives (RTOs), evidence of disaster recovery tests, feed into risk and management reviews | ISO/IEC 22301, ISO/IEC 22313 |
| DORA | Regulatory mandates for RTOs, resilience tests, inclusion of critical providers, advanced penetration testing | DORA Articles 11-14 |
| NIST | Maturity in response/recovery functions, process definition, active measurement | NIST CSF PR.IP, RS.RP, RC.RP |
| COBIT/ISACA | Board ownership, RACI charts, KPIs, governance metrics | COBIT APO12, BAI04 |
Here, auditors demand a governance feedback loop, linking business requirements to technical controls, validated by testing and continuous review. Zenith Controls show how resilience is a web of processes, not a product.
Incident Response: Systemic Learning vs. Ticket Closure
- Technical approach: Incident detected, contained, ticket closed.
- Management system:
- Plan: Predefined response, cross-functional roles, secure communication.
- Assessment: Impact measured, business requirement determines escalation.
- Response: Coordinated action, evidence handling, stakeholder notification (per NIS2/DORA reporting obligations).
- Review/Learn: Post-mortem analysis, root cause resolution, policy/process updates (continuous improvement).
Clarysec’s blueprint and mapped controls operationalize this cycle, ensuring every incident feeds systemic improvement, and audit success.
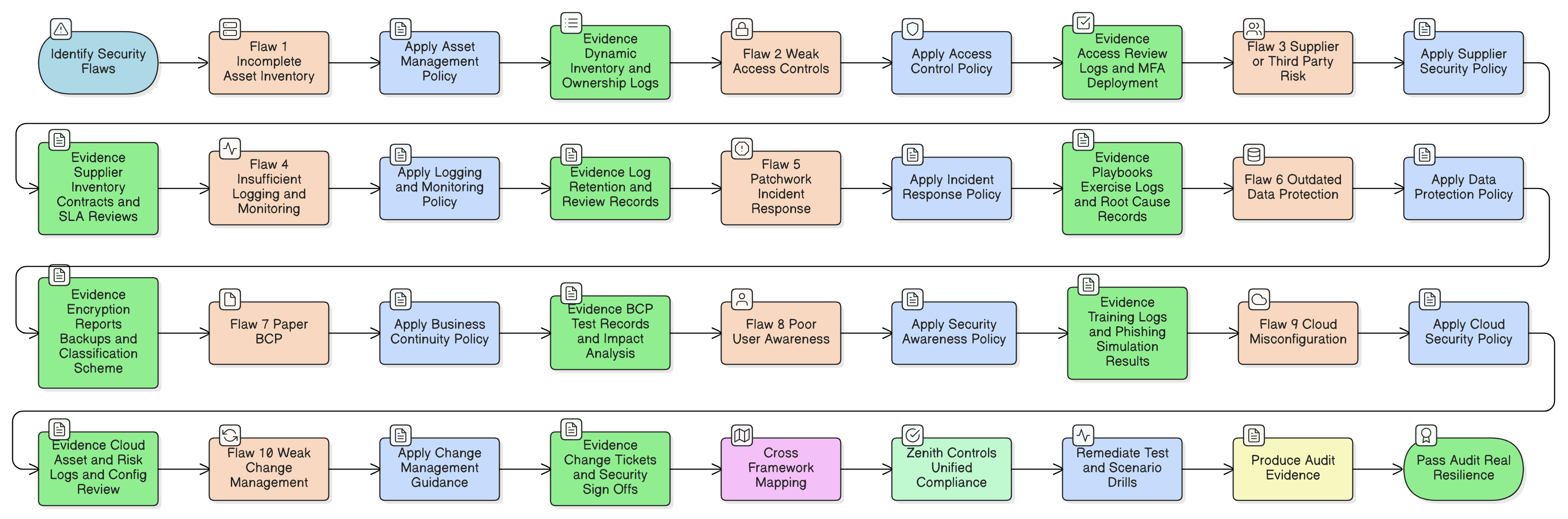
Pitfalls and Gotchas: Where Audit Failures Happen, and Solutions
| Pitfall | Audit Failure Mode | Clarysec Solution |
|---|---|---|
| ISMS “by IT” only | Management system scope too narrow for standards | Zenith Blueprint Phase 1 for enterprise-wide role assignment |
| IT-focused policies | Misses risk, supplier, HR, legal scope, cannot pass NIS2/DORA/GDPR | Clarysec policy pack mapped to Zenith Controls for full coverage |
| No security screening in supplier process | Procurement misses regulatory risks | Third-party and supplier security policy alignment, mapped onboarding/review |
| Skipped/poor management reviews | Misses core management system clauses | Zenith Blueprint Phase 5, formal board-driven reviews and improvement registry |
| Improvement actions not visible across business | Org-wide corrective action required | Documented, trackable improvement methodology (Clarysec toolkit) |
Turning Audit Failure into Systemic Success: Practical Transformation Steps
Your path forward:
- Initiate with the Board: Every journey begins with clear governance, policy commitment, budget backing, alignment with strategic direction.
- Activate the Blueprint: Use Clarysec’s 30-step roadmap to engineer your management system, by phase, with cross-functional milestones and improvement cycles.
- Deploy Mapped Policies: Implement Clarysec’s enterprise policy library (including Information security policy and top management commitment and Third-party and supplier security policy).
- Crosswalk Controls: Make your controls audit-ready across ISO, NIS2, DORA, GDPR, and COBIT, use the Zenith Controls cross-compliance guide for full mapping.
- Drive Continuous Improvement: Schedule management reviews, lessons learned sessions, and keep an audit-ready improvement registry.
Outcome:
Compliance evolves into business resilience. Audits become catalysts for improvement, not triggers for panic.
Integrating Cross-Compliance: The Complete Management System Map
Clarysec’s Zenith Controls provide not just “compliance,” but true alignment, attributes for every control, cross-mapped support for related standards, step-by-step methodology, and board-level audit evidence.
For supplier security alone, you get:
- Attributes: Scope, business function, risk context.
- Supporting Controls: Links to business continuity, HR screening, and risk management.
- ISO/Framework Mapping: Connections to ISO/IEC 27005, 27014, 27036, NIS2, DORA, GDPR, COBIT 19, NIST.
- Audit Steps: Evidence retention, review protocols, improvement cycle triggers.
This systemic integration means you’re never preparing for audits piecemeal. You’re continuously resilient, board, business, and technical alignment, every day.
Call to Action: Transform Compliance from Firewall to Systemic Audit-Readiness
The age of perimeter-based compliance is over. ISO 27001, NIS2, and DORA are management systems, not checklists. Success means boardroom ownership, mapped controls, documented improvement, and enterprise policy alignment, across every supplier, staff, and business process.
Ready to move from tech checklist to true management system?
- Start your maturity gap assessment with Clarysec’s toolkit.
- Download the Zenith Blueprint for the full 30-step roadmap.
- Explore Zenith Controls for mapped, audit-ready controls.
- Activate enterprise policies for robust compliance, across ISO, NIS2, DORA, and more.
Make your next audit the foundation for real business resilience. Contact Clarysec for an ISMS readiness demo or access our toolkit to transform compliance from a failed checklist to a living management system.
Additional Resources:
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council