Building a Resilient and Audit-Proof Supplier Risk Program: ISO/IEC 27001:2022 and the Cross-Compliance Roadmap
It Starts With Crisis: The Day Supplier Risk Becomes a Boardroom Emergency
Maria, the CISO of a fast-growing FinTech firm, stares at the urgent notification from her cloud analytics provider, DataLeap. Unauthorised access to customer metadata has been detected. On her other screen flashes a calendar invite, her DORA readiness audit is days away.
She scrambles: Is the DataLeap contract airtight? Did the last security assessment cover breach timelines? The answers are hidden in outdated spreadsheets and scattered inboxes. Within minutes, the board is demanding concrete assurances:
Which data was exposed?
Did DataLeap meet security obligations?
Can our team prove compliance, right now, to our regulator, auditors, and clients?
Maria’s dilemma is the norm. Supplier risk, once a procurement checkbox, now represents a central business, regulatory, and operational risk. As ISO/IEC 27001:2022, DORA, NIS2, GDPR, NIST, and COBIT increasingly converge on third-party governance, supplier risk programs are under pressure to be proactive, defensible, and audit-ready across all frameworks.
Yet while audit failure rates remain high, the path to resilience is well-trodden, and it starts with transforming chaos into evidence-driven operations. This guide walks through a proven lifecycle approach, mapped directly to Clarysec’s cross-compliance Zenith Controls and toolkits, to help your organization operationalize supplier risk, pass every audit, and build long-term trust.
Why Supplier Risk Programs Get Audits Wrong – And How to Get Them Right
Most businesses still think supplier risk management means keeping a list of vendors and signed NDAs. Modern security standards demand much more:
- Risk-based identification, classification, and management of supplier relationships
- Well-defined contract requirements, tracked for ongoing compliance
- Integration of suppliers in incident response, business continuity, and monitoring
- Evidence, not just documents, for every control, across multiple standards
For Maria and many CISOs, the real failure isn’t policy, it’s lack of continuous, lifecycle management. Every missed security assessment, outdated contract clause, or blind spot in supplier monitoring is a potential audit gap and business liability.
Foundation First: Creating the Supplier Risk Lifecycle
The most resilient supplier risk programs don’t rely on static checklists, they operate as living processes:
- Defined Governance and Ownership: An internal supplier risk owner (often within security or procurement) is accountable for the lifecycle from onboarding to offboarding.
- Clear Policy Backbone: Policies such as Clarysec’s Third-party and supplier security policy are not just regulatory cover, they empower program owners, mandate objectives, and establish risk-based supplier management.
The organization shall identify, document and assess the risks associated with each supplier relationship, prior to engagement and at regular intervals thereafter.
– Third-party and supplier security policy, Section 3.1, Risk Assessment
You must anchor your approach in policy and accountability before controls, contracts, or assessments.
Unpacking ISO/IEC 27001:2022 Controls – The Supplier Security System
Supplier security is not a single step. Under ISO/IEC 27001:2022, and as decomposed by Clarysec’s Zenith Controls, supplier-focused controls operate together as an interconnected system:
Control 5.19: Information Security in Supplier Relationships
- Set requirements upfront based on sensitivity and criticality of data or systems supplied.
- Formalize risk assessments at onboarding, then re-assess in response to incidents or major changes.
Control 5.20: Security Clauses in Supplier Agreements
- Embed enforceable security terms into contracts: breach notification timelines, audit rights, obligations for regulatory alignment, and offboarding procedures.
- Example requirement from policy:
Supplier agreements must specify security requirements, access controls, monitoring obligations, and consequences for non-compliance.
– Third-party and supplier security policy, Section 4.2, Contractual Controls
Control 5.21: Managing Information Security in the ICT Supply Chain
- Look beyond direct suppliers: account for their critical dependencies (fourth parties).
- Audit your supplier’s own supply chain, especially required by DORA and NIS2.
Control 5.22: Continuous Monitoring, Review, and Change Management
- Regular review meetings, continuous monitoring tools, supplier audit report analysis.
- Formal tracking of incidents, SLA adherence, and change notifications.
Control 5.23: Security for Cloud Services
- Clear delineation of shared roles and responsibilities for all cloud services.
- Ensure your team, the supplier (such as DataLeap), and IaaS providers are aligned on physical security, data encryption, access controls, and incident management.
Cross-Compliance Mapping – How Each Control Relates to DORA, NIS2, GDPR, NIST, and COBIT 19
See the tables in later sections for clause-level mapping and audit expectations.
Elevating from Policy to Audit-Ready Evidence – What Really Passes Scrutiny
In Clarysec’s cross-framework audit experience, organizations fail supplier audits for one core reason: the inability to produce actionable evidence. Auditors ask not just for policies, but for operational proof:
- Where are supplier risk ratings logged and reviewed?
- How is ongoing supplier performance monitored, and how are exceptions managed?
- What data supports contract compliance and breach notification?
- How does supplier offboarding protect business assets and information?
Clarysec’s Zenith Controls guide recognizes this by detailing mandatory evidence lines, documents, and logs for each phase and standard.
A supplier risk program must produce verifiable records at each stage: risk assessment, due diligence, contractual clause inclusion, monitoring and review. Cross-functional logs, incidents involving suppliers, and even supplier exit procedures are essential evidence lines.
– Zenith Controls: Audit Methodology
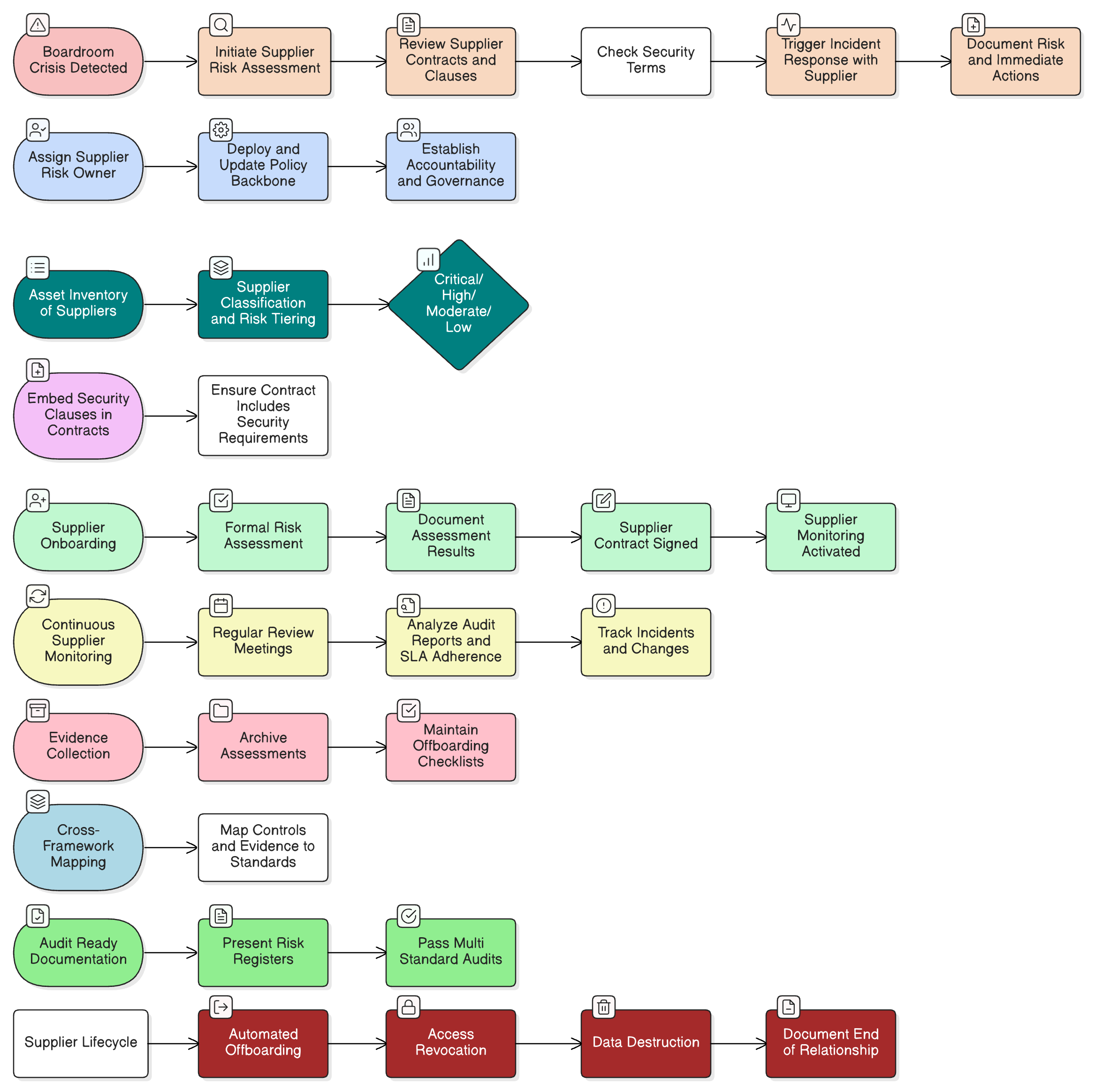
The Step-by-Step Roadmap: Building Your Audit-Proof Program
Clarysec’s 30-Step Zenith Blueprint Sequence
Adapted for real-world effectiveness, below is a practical lifecycle roadmap for supplier risk mastery:
Phase 1: Establishment and Policy Foundation
- Governance: Designate Supplier Risk Owner with documented roles and accountability.
- Policy: Deploy the Third-party and supplier security policy as the backbone. Update policies with guidance on onboarding, risk assessments, monitoring, and offboarding.
Phase 2: Risk Assessment and Supplier Categorization
- Asset Inventory: List suppliers who access critical assets, financial data, and personal information. Map out flows and privileges for GDPR and ISO requirements.
- Risk Tiering: Use Clarysec’s tiering matrices to classify suppliers (critical, high-risk, moderate, low).
Phase 3: Contracting and Control Definition
- Embed Clauses: Hardwire security terms into contracts: breach notification SLAs, audit rights, regulatory compliance. Use templates from your Clarysec policy toolkit.
- Incident Response Integration: Engage suppliers in planned incident response and drill exercises.
Phase 4: Operationalization and Continuous Monitoring
- Continuous Reviews: Monitor supplier activities, conduct regular contract/controls reviews, and log all findings.
- Automated Offboarding: For supplier terminations, use workflow scripts, ensure access revocation, data destruction, and evidence of secure handover.
Phase 5: Audit-Ready Documentation and Evidence Trail
- Evidence Mapping: Archive assessments, contract reviews, monitoring logs, and offboarding checklists, all mapped to controls from ISO/IEC 27001:2022, NIS2, DORA, GDPR, NIST, COBIT.
By following this validated framework, your team creates an operational lifecycle, from intent to renewal to exit, proven to pass most rigorous audit scrutiny.
Practical Example: From Chaos to Audit Trail
Back to Maria’s breach scenario. Here’s how she regains control using Clarysec’s toolkits:
- Risk Assessment Initiation: Use the Clarysec “High-Risk Supplier” template to assess impact, document risks, and trigger remediation workflows.
- Contract Review: Retrieve DataLeap’s agreement. Amend to include explicit notification SLA (e.g., breach reporting within 4 hours), mapping directly to Control 5.20 and DORA Article 28.
- Monitoring and Documentation: Assign monthly supplier log reviews via Clarysec’s dashboard. Store the evidence in an audit-ready repository mapped to Zenith Controls.
- Offboarding Automation: Schedule contract expiry triggers, enforce access revocation, and file data deletion confirmations, all logged for future audits.
Maria presents auditors with her risk register, documented remediations, updated contracts, and supplier monitoring records, transforming a crisis into a demonstration of mature, adaptive governance.
Integrating Supporting Controls: The Supplier Risk Ecosystem
Supplier risk is not isolated. Clarysec’s Zenith Controls make relationships and dependencies clear:
| Primary Control | Related Controls | Description of Relationship |
|---|---|---|
| 5.19 Supplier Rel. | 5.23 Monitoring, 5.15 Access, 5.2 Asset Mgmt | Asset management identifies data assets at risk; monitoring ensures ongoing compliance; access controls reduce attack surface |
| 5.20 Agreements | 5.24 Privacy/Data Protec., 5.22 Information Transfer | Ensures data protection and safe transfer are explicitly managed in supplier contracts and data flows |
Using the Clarysec crosswalks below, each relationship is mapped for seamless multi-framework compliance.
Framework Mapping Table: Supplier Risk Requirements Across Major Regulations
| Standard/Framework | Clause/Control | Supplier Risk Requirement |
|---|---|---|
| NIS2 | Article 21(2,3,5) | Mandatory supplier risk assessments, monitoring, reporting for essential/important entities |
| DORA | Article 28 | Contract clauses for ICT third-parties, audits, incident notifications |
| GDPR | Article 28, 32 | Processor contract clauses, technical controls, ongoing assurance |
| COBIT 19 | DSS05, DSS06 | Supplier relationship management, contract obligations, performance assessment |
| NIST CSF | ID.SC: Supply Chain Risk Mgmt | Formal process for identifying, assessing, and managing supply chain risks |
| ISO/IEC 27001:2022 | Annex A (5.19-5.23) | Full supplier lifecycle security: onboarding, contracts, monitoring, offboarding |
Leveraging Zenith Controls enables you to demonstrate overlapping compliance, reducing audit duplication and friction.
How Auditors See Your Program – Adapting to Every Lens
Each standard brings its own flavor to supplier audits. Clarysec’s audit methodologies ensure you never get blindsided:
- ISO/IEC 27001 Auditor: Seeks process documentation, risk registers, meeting notes, and evidence of contract compliance.
- DORA Auditor: Focuses on operational resilience, contract clause specificity, supply chain concentration risk, and incident recoverability.
- NIST Auditor: Emphasizes risk management lifecycle, process efficacy, and incident adaptation across all suppliers.
- COBIT 19 Auditor: Assesses governance structures, vendor performance metrics, review dashboards, and value delivery.
- GDPR Auditor: Audits contracts for data protection addenda, records of subject impact assessments, and breach response logs.
An audit-proof supplier risk program must produce not only policy evidence but practical, ongoing records, spanning risk assessments, supplier reviews, incident integrations, and contract management artifacts. Each standard or framework will emphasize different artifacts, but all demand a living, operational system.
– Zenith Controls: Audit Methodology
Cloud Services and Shared Responsibility: Mapping Duties for Maximum Assurance
Cloud-based suppliers (like DataLeap) introduce unique risks. According to ISO/IEC 27001 Controls 5.21 and 5.23, and as mapped in Zenith Controls, here is the shared responsibility breakdown:
| Responsibility Area | Cloud Provider (e.g., AWS) | Supplier (e.g., DataLeap) | Customer (You) |
|---|---|---|---|
| Physical Security | Data center security | N/A | N/A |
| Infrastructure Security | Compute, network protections | App environment configuration | N/A |
| Application Security | N/A | SaaS development and control | User access permissions |
| Data Security | Encryption tools provided | Data encryption implemented | Data classification, access policies |
Documenting your role and ensuring controls are mapped gives you robust defense for DORA and NIS2 audits.
Turning a Single Action Into Multi-Standard Compliance
A supplier risk assessment log prepared for ISO/IEC 27001:2022 Control 5.19 can, through Clarysec’s mappings, be re-used for NIS2, DORA, GDPR, and NIST audits. Contract updates reflect both GDPR Article 28 and DORA incident requirements. Continuous monitoring evidence feeds COBIT 19 metrics.
This multiplies the business value: saving time, preventing gaps, and ensuring no critical obligation goes untracked.
Common Audit Pitfalls and How to Avoid Them
Field experience and Clarysec’s data show that failed audits most often result from:
- Static, outdated supplier lists lacking periodic review
- Generic contracts without actionable security terms
- No logs of continuous supplier monitoring or privileged access
- Omission of suppliers from incident, business continuity, or recovery exercises
Clarysec’s Zenith Blueprint eliminates these gaps with integrated policies and automation scripts, ensuring operational controls match documented intent.
Conclusion and Next Steps: Transforming Supplier Risk Into Business Value
The message is clear: Supplier risk is a dynamic business risk, central, not peripheral. Success means shifting from static, checklist-based thinking to an evidence-driven lifecycle, rooted in policy and mapped across compliance frameworks.
With Clarysec’s Zenith Blueprint, Zenith Controls, and the proven Third-party and supplier security policy, your organization gains:
- Immediate cross-framework credibility
- Streamlined audit response for ISO/IEC 27001:2022, NIS2, DORA, GDPR, NIST, COBIT 19
- Operational resilience and continuous risk reduction
- Automated, evidence-ready lifecycle for the entire supply chain
Don’t wait for your DataLeap moment or the next auditor’s call. Audit-proof your supplier program, streamline compliance, and convert risk management from a reactive pain point to proactive business differentiation.
Ready for Resilience?
Download the Zenith Blueprint, review the Zenith Controls, and put Clarysec’s policy toolkit to work for your team today.
For a tailored demo or risk assessment, contact the Clarysec Compliance Advisory Team.
References
- Clarysec Zenith Controls: The Cross-Compliance Guide Zenith Controls
- Zenith Blueprint: An Auditor’s 30-Step Roadmap Zenith Blueprint
- Third-party and supplier security policy Third-party and supplier security policy
- ISO/IEC 27001:2022, ISO/IEC 27002:2022
- NIS2, DORA, GDPR, NIST, COBIT 19
For personalized assistance in supplier risk program design and operation, contact Clarysec’s Compliance Advisory Team today.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council