The CISO’s Guide to Audit-Ready Forensic Readiness: Unifying NIS2, DORA, ISO 27001, and GDPR
Maria, CISO at a mid-sized fintech firm, felt a familiar knot tighten in her stomach. The external audit report for their ISO/IEC 27001:2022 certification sat on her desk, its stark conclusion staring back at her. A major non-conformity.
Three weeks ago, a junior developer had accidentally exposed a non-production data store to the public internet for 72 minutes. Operationally, the incident response was a success. The team acted swiftly, locking down the system and confirming no sensitive customer data was involved.
From a compliance perspective, it was a disaster.
When the auditor asked for evidence to prove exactly what happened during those 72 minutes, the team came up short. The cloud provider’s logs were generic and had rolled over after 24 hours. The firewall logs showed connections but lacked packet-level detail. The internal application logs had not been configured to record the specific API calls made. They could not definitively prove that no unauthorized party had attempted to escalate privileges or pivot to other systems.
The auditor’s finding was brutal: “The organization cannot provide sufficient, reliable evidence to reconstruct the timeline of a security event, demonstrating a lack of forensic readiness. This raises significant concerns regarding compliance with NIS2 incident management requirements, DORA’s mandate for detailed incident tracking, and GDPR’s principle of accountability.”
Maria’s problem was not a failure of incident response, it was a failure of foresight. Her team was excellent at fighting fires, but they had not built the capability to investigate the arsonist. This is the critical gap where forensic readiness lives, a capability that is no longer a luxury but a non-negotiable requirement under modern regulations.
From Reactive Logging to Proactive Forensic Readiness
Many organizations, like Maria’s, mistakenly believe that “having logs” is the same as being prepared for an investigation. They are not. Forensic readiness is a strategic capability, not an accidental byproduct of IT operations. As the international standard ISO/IEC 27043 frames it, organizations must establish processes to ensure digital evidence is prepared, accessible, and cost-effective in anticipation of potential security incidents.
In the context of NIS2, DORA, ISO 27001:2022, and GDPR, this means you can:
- Detect relevant events quickly enough to meet tight reporting deadlines.
- Reconstruct a trustworthy sequence of events from tamper-resistant logs.
- Demonstrate to auditors and regulators that your logging and monitoring controls are risk-based, privacy-respecting, and effective.
Clarysec’s implementation guidance in Clarysec’s Zenith Controls: The Cross-Compliance Guide Zenith Controls puts it simply:
Effective forensic readiness in compliance contexts requires minimizing log data collection to what is strictly necessary, avoiding storage of excessive personal or sensitive data, and where feasible, anonymizing or pseudonymizing data. Additional best practices include applying robust security measures like access controls, encryption, frequent audits, and ongoing monitoring, together with enforcing data retention policies aligned to GDPR and regularly purging unneeded information.
This is a fundamental shift in mindset:
- From Data Hoarding to Purposeful Collection: Instead of collecting everything, you define the evidence needed to answer critical questions: Who did what? When and where did it happen? What was the impact?
- From Siloed Logs to Correlated Timelines: Your firewall, application, and cloud logs are individual puzzle pieces. Forensic readiness is the ability to assemble them into a coherent picture.
- From Operational Tool to Evidentiary Asset: Logs are not just for debugging. They are legal and regulatory evidence that must be protected, preserved, and handled with a clear chain of custody.
An inability to prove what happened during a breach is now seen as a control failure in itself, regardless of the incident’s initial impact.
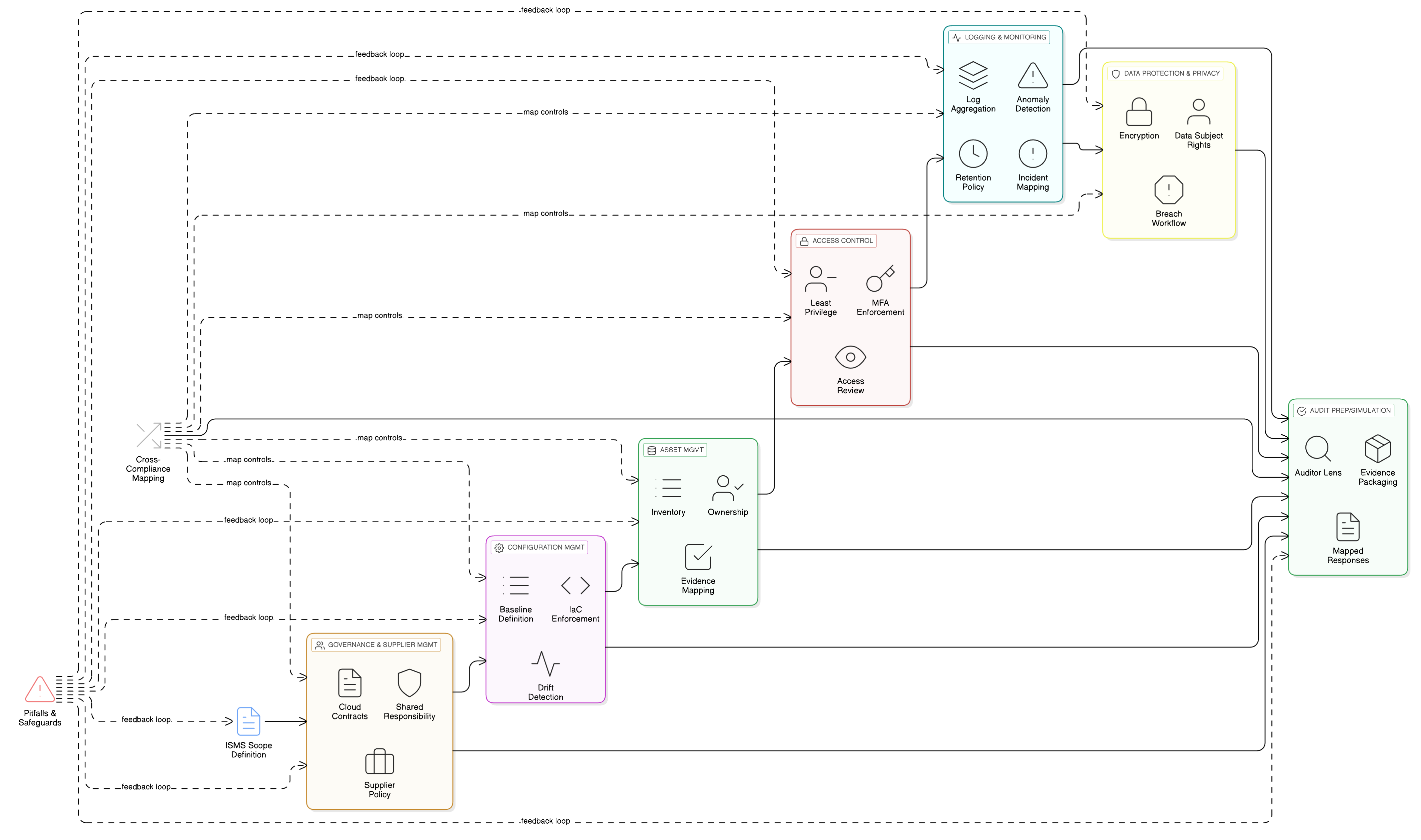
The Foundation: Where Governance and Policy Meet Practice
Before a single log is configured, a forensic readiness program begins with clear governance. An auditor’s first question will not be “Show me your SIEM,” but “Show me your policy.” This is where a structured approach provides immediate, defensible value.
In The Zenith Blueprint: An Auditor’s 30-Step Roadmap Zenith Blueprint, Step 14 of the ‘Risk & Implementation’ phase is dedicated to this foundational work. The objective is explicit:
“Develop or refine specific policies and procedures as required by your chosen risk treatments (and Annex A controls), and ensure alignment with regulations such as GDPR, NIS2, and DORA.”
This step forces organizations to translate risk decisions into documented, enforceable rules. For a CISO like Maria, this means creating a suite of interconnected policies that define the organization’s forensic capability. Clarysec’s policy templates provide the architectural plans for this structure. The key is to establish explicit links between policies to create a cohesive governance framework.
| Policy | Role in Forensic Readiness | Example Link from Clarysec’s Toolkit |
|---|---|---|
| Logging and Monitoring Policy (P22 / P22S) | Defines logging scope, access control, and retention; ensures telemetry is available for forensic analysis. | Referenced by the Evidence Collection and Forensics Policy as the source of forensic data. |
| Data Retention and Disposal Policy (P14) | Governs how long logs and audit evidence are kept and when they are securely deleted. | Linked from the Audit and Compliance Monitoring Policy to govern the lifecycle of compliance records. |
| Evidence Collection and Forensics Policy | Establishes procedures for collecting, preserving, handling, and reviewing digital evidence with a clear chain of custody. | Requires periodic review of the “Adequacy of logging, evidence retention, and forensic readiness procedures.” |
| Audit and Compliance Monitoring Policy | Dictates what audit logs must contain and how compliance activities are themselves monitored and recorded. | Specifies that audit logs must include objectives, evidence reviewed, findings, and actions taken. |
By establishing this policy framework first, you create a defensible position. For example, our Evidence Collection and Forensics Policy states its reliance on the P22 – Logging and Monitoring Policy to ensure “availability of event logs and telemetry for evidence collection and forensic correlation.” This single sentence creates a powerful mandate, declaring that the purpose of logging is not just operational-it is to serve forensic analysis.
For smaller organizations, the principles are identical. Our Evidence Collection and Forensics Policy-sme cross-references its own foundational logging policy: “P22S – Logging and Monitoring Policy: Provides the raw data used as forensic evidence and establishes retention, access control, and logging requirements.”
This documented strategy tells auditors, regulators, and internal teams that you have a defined, intentional approach to evidence management.
The Technical Engine: Powering Readiness with Strategic Monitoring
With a solid policy foundation, the next step is to build the technical engine. This is centered on two key controls from ISO/IEC 27001:2022: 8.15 Logging and 8.16 Monitoring activities. While often discussed together, they serve distinct purposes. Control 8.15 is about recording events. Control 8.16 is about actively analyzing them to detect anomalies and security events. This is the heartbeat of forensic readiness.
The Zenith Controls guide, our intellectual property that maps ISO controls to global standards and audit practices, details how 8.16 Monitoring activities is the linchpin that connects raw data to actionable intelligence. It does not exist in a vacuum; it is part of a deeply interconnected security ecosystem:
- Tied to 8.15 Logging: Effective monitoring is impossible without robust logging. Control 8.15 ensures the raw data exists. Control 8.16 provides the analysis engine to make sense of it. Without monitoring, logs are just a silent, unexamined archive.
- Feeds into 5.25 Assessment and decision on information security events: The alerts and anomalies flagged by monitoring (8.16) are the primary inputs for the event assessment process (5.25). As the Zenith Controls guide notes, this is how you distinguish a minor blip from a full-blown incident requiring escalation.
- Informed by 5.7 Threat intelligence: Your monitoring should not be static. Threat intelligence (5.7) provides new indicators of compromise and attack patterns, which should be used to update your monitoring rules and searches, creating a proactive feedback loop.
- Extends to 5.22 Monitoring of supplier services: Your visibility cannot end at your own perimeter. For cloud services and other suppliers, you must ensure their monitoring and logging capabilities meet your forensic requirements, a key consideration for NIS2 and DORA.
A forensic-ready logging and monitoring strategy starts with purpose. Your alarm thresholds should be based on your risk assessment, with examples such as monitoring for spikes in outbound network traffic, rapid account lockouts, privilege escalation events, malware detections, and unauthorized software installations.
Similarly, log retention must be a deliberate decision. The Zenith Controls guide advises:
The retention and backup of logs should be managed for a predefined period, with protections against unauthorized access and modifications. Log retention periods must be determined by business needs, risk assessments, good practices, and legal requirements…
This means defining retention periods per system (e.g., 12 months online, 3-5 years archived for DORA-critical systems) and ensuring backup copies are preserved for at least as long as logs are regularly reviewed.
The Compliance Balancing Act: Gathering Evidence Without Violating GDPR
A knee-jerk reaction to an audit failure like Maria’s might be to log everything, everywhere. This creates a new and equally dangerous problem: violating data protection principles under GDPR. Forensic readiness and privacy are often seen as opposing forces, but they must be reconciled.
This is where ISO 27001:2022 control 5.34 Privacy and protection of PII becomes critical. It serves as the bridge between your security program and your privacy obligations. As detailed in the Zenith Controls, implementing 5.34 is direct evidence of your ability to meet GDPR’s Article 25 (Data protection by design and by default) and Article 32 (Security of processing).
To achieve this balance, your forensic program must integrate key privacy-enhancing controls:
- Integrate with 5.12 Classification of information: Ensure logs originating from systems that process PII are classified as highly sensitive and receive the strictest protections.
- Implement 8.11 Data masking: Actively use pseudonymization or masking to obscure personal identifiers in logs where raw values are not required for investigation. This is a direct implementation of data minimization.
- Enforce 5.15 and 5.16 (Access control and Identity management): Restrict access to raw logs on a strict need-to-know basis, especially for events relating to employees or customers.
- Map to Privacy Frameworks: Support your program with standards like ISO/IEC 27701 (for PIMS), ISO/IEC 27018 (for PII in the cloud), and ISO/IEC 29100 (for privacy principles).
By integrating these controls, you can design a logging and monitoring strategy that is both forensically sound and privacy-aware, satisfying security teams and data protection officers simultaneously.
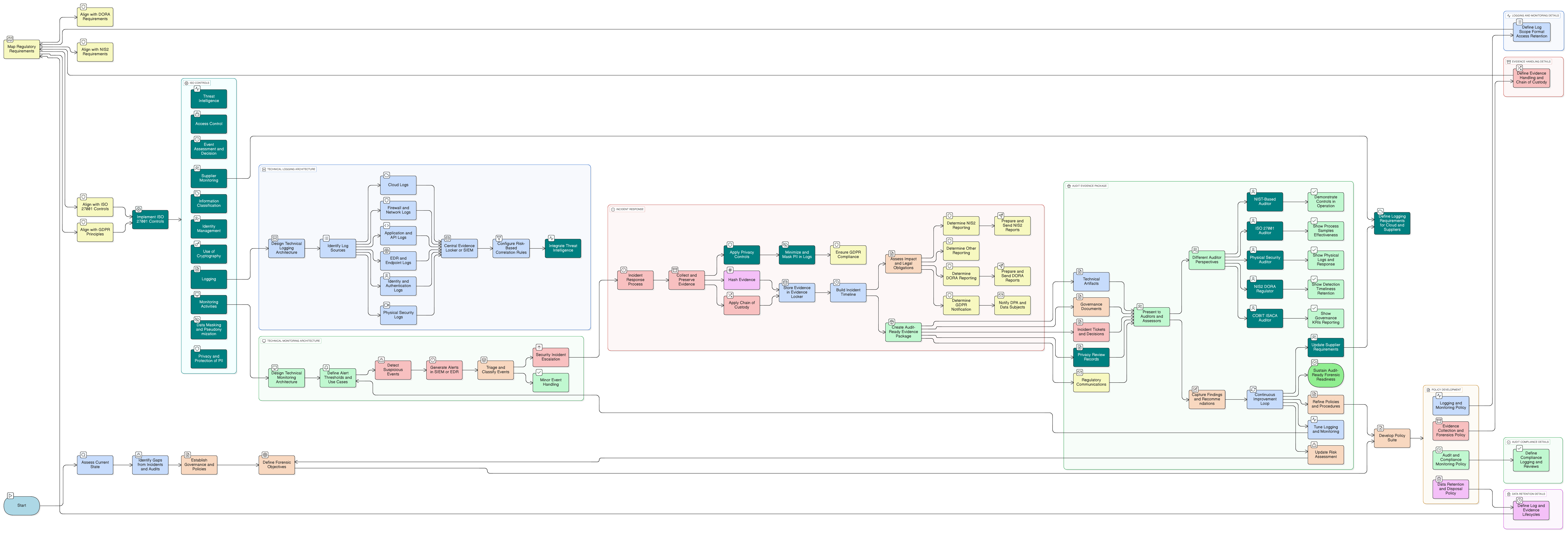
From Theory to Audit: What Different Auditors Actually Look For
Passing an audit requires presenting the right evidence in a way that satisfies the auditor’s specific methodology. An ISO 27001 auditor thinks differently from a COBIT auditor, and both have a different focus from a NIS2 regulator.
The audit_methodology section within our Zenith Controls guide for 8.16 Monitoring activities provides an invaluable roadmap for CISOs, translating the control’s objective into tangible evidence for different audit perspectives.
Here’s how to prepare for scrutiny from various angles:
| Auditor Background | Primary Focus | Key Evidence They Will Ask For |
|---|---|---|
| ISO/IEC 27001 Auditor (using ISO 19011/27007) | Operational Effectiveness: Is the process documented and followed consistently? Are controls operating as designed? | Sampled log files, SIEM alerts, and corresponding incident tickets from the last 3-6 months. A live walkthrough of how a recent critical event was logged, detected, and resolved. |
| COBIT / ISACA Auditor (using ITAF) | Governance & Maturity: Is the process managed, measured, and contributing to business objectives? | Key Risk Indicators (KRIs) for monitoring (e.g., mean-time-to-detect). Management reports on security events. Evidence of system tuning and false positive reduction. |
| NIST Auditor (using SP 800-53A) | Examine, Interview, Test: Can you prove the control works through demonstration, discussion, and direct testing? | Live demonstration of the monitoring system (e.g., SIEM query). Configuration files proving logging is enabled on critical systems. Records of a recent penetration test and proof of detection. |
| Regulatory Assessor (NIS2/DORA) | Mandate Fulfillment: Do your capabilities directly meet the explicit legal requirements for detection, reporting, and record-keeping? | A clear mapping of your monitoring processes to NIS2 Article 21(2)(d). Log retention policies that meet DORA’s specific timeframes. Records proving timely incident classification and reporting. |
| Physical Security Auditor | Physical Asset Protection: How do you detect and record unauthorized physical access? | Floor plans with CCTV placement, retention settings for footage, and alarm configuration records. Event logs showing how a recent physical alarm was handled. |
Understanding these different lenses is crucial. For an ISO auditor, a well-documented process for handling a false alarm is excellent evidence of a working system. For a NIST auditor, a live test showing an alert fire in real-time is more compelling. For a NIS2 or DORA regulator, proof of timely detection and escalation is paramount. Maria’s team failed because they could not provide evidence that would satisfy any of these perspectives.
Practical Scenario: Building an Audit-Ready Evidence Package
Let’s apply this to a real-world scenario: a malware campaign affects several endpoints in your EU operations, some of which process customer PII. You need to satisfy GDPR, NIS2, DORA, and your ISO 27001 auditor.
Your evidence package should be a structured narrative, not just a data dump. It should include:
Technical Timeline & Artifacts:
- SIEM alerts showing initial detection, tied to 8.16 Monitoring activities.
- EDR logs with file hashes, process trees, and containment actions.
- Firewall and network logs showing C2 communication attempts.
- Authentication logs showing any lateral movement attempts.
- Hashes of all collected log files to prove integrity, aligning with 8.24 Use of cryptography.
Governance and Procedural Evidence:
- A copy of your Evidence Collection and Forensics Policy.
- A copy of your Logging and Monitoring Policy, demonstrating the mandate to collect this data.
- The relevant excerpt from your Data Retention and Disposal Policy Data Retention and Disposal Policy showing the retention periods for these specific logs.
Incident Management Linkage:
- The incident response ticket showing classification, severity assessment, and escalation, linking monitoring (8.16) to incident assessment (5.25).
- Records of the decision-making process for notifying authorities under NIS2 Article 23 or GDPR Article 33.
Privacy Compliance Evidence:
- A note from the DPO confirming a privacy review was conducted on the evidence package.
- Demonstration that any PII within the logs was handled according to policy (e.g., access was restricted), aligning with control 5.34 Privacy and protection of PII.
Regulatory Communications:
- A record of any correspondence with the Data Protection Authority or national cybersecurity authority, as recommended by our guidance in the Zenith Controls.
This structured package turns a chaotic event into a demonstration of control, process, and due diligence.
Building Your Evidence Locker: An Actionable Plan
How can a CISO move from a reactive posture to a state of continuous, audit-ready forensic readiness? The key is to systematically build an “evidence locker” containing the proof auditors need before they ask for it.
1. Document Your Strategy:
- Finalize Policies: Approve and publish your Logging and Monitoring Policy, Evidence Collection Policy, and Data Retention Policy, using Step 14 of the Zenith Blueprint as your guide.
- Map Your Data Flow: Maintain a diagram showing where logs are collected from, where they are aggregated (e.g., SIEM), and how they are protected.
2. Configure and Validate Your Tooling:
- Set Risk-Based Thresholds: Document the thresholds for key alerts and justify them based on your risk assessment.
- Validate Retention Settings: Take screenshots from your log management platform or cloud console that clearly show the configured retention periods for different data types.
- Prove Integrity: Establish a process for cryptographically hashing critical evidence files upon collection and store the hashes separately.
3. Demonstrate Operational Effectiveness:
- Keep Detailed Records: Maintain records of how you handled at least three recent security events, even false alarms. Show the initial alert, triage notes, actions taken, and final resolution with timestamps.
- Log Your Log Access: Be ready to show who has access to view raw logs and provide audit trails of their access.
- Test and Record: Keep records showing your monitoring systems are healthy and that periodic tests (e.g., alarm tests) are conducted and logged.
Maria’s audit failure was not technical, it was strategic. She learned the hard way that in today’s regulatory landscape, an uninvestigable incident is almost as bad as the incident itself. Logs are no longer a simple byproduct of IT; they are a critical asset for governance, risk management, and compliance.
Don’t wait for a non-conformity to expose your gaps. By building a true forensic readiness capability, you transform your security data from a potential liability into your greatest asset for proving due diligence and resilience.
Ready to build your own audit-ready forensic capability? Explore Clarysec’s The Zenith Blueprint: An Auditor’s 30-Step Roadmap to build your documented ISMS from the ground up, and dive into our Zenith Controls to understand the precise evidence auditors require for every control. Schedule a consultation today to see how our integrated toolkits can accelerate your journey to demonstrable compliance.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council