Beyond the Questionnaire: A CISO's Definitive Guide to Auditing High-Risk Suppliers for NIS2 and DORA
The report landed on CISO Maria Valen’s desk with a quiet thud that felt more like a siren. It was the pre-audit assessment for their upcoming DORA compliance review, and one line was highlighted in stark red ink: “Insufficient assurance for critical third-party provider, CloudSphere.”
CloudSphere wasn’t just any vendor. They were the backbone of the company’s new digital banking platform, processing millions of transactions daily. Maria had their ISO/IEC 27001:2022 certificate on file. She had their completed security questionnaire, a hefty 200-question document. But the pre-auditors were signaling that for a high-risk, critical supplier, checkbox compliance was no longer enough. The game had changed.
With both the NIS2 Directive and the Digital Operational Resilience Act (DORA) now in full force, regulators are looking past the paper trail. They demand tangible proof of due diligence, continuous monitoring, and robust governance over the entire supply chain. Maria’s challenge is one facing CISOs everywhere: how do you move beyond the questionnaire to truly audit and secure your most critical suppliers? It requires a strategic shift from passive validation to active, evidence-based assurance.
The Flaw of the Static Questionnaire in a Dynamic World
For years, the security questionnaire has been the cornerstone of third-party risk management. But it’s a static snapshot in a dynamic threat landscape. A supplier’s risk profile is not fixed; it evolves with every new threat, system change, or subcontractor they onboard. Relying solely on self-attestation for a critical supplier like CloudSphere is like navigating a storm with last year’s weather map.
The NIS2 directive explicitly calls for a risk-based approach, demanding that security measures are proportional to the actual risks. This means a one-size-fits-all questionnaire is fundamentally misaligned with modern regulatory expectations. Gone are the days when a certificate or a completed checklist could substitute for evidence. The true risk lies beyond the paper trail.
This is where a structured, lifecycle-based approach becomes essential. It’s not about abandoning questionnaires but augmenting them with deeper, more intrusive verification for suppliers that truly matter. This is the core principle embedded in Clarysec’s Third-party and supplier security policy. One of its foundational objectives is to:
“Require formal due diligence and documented risk assessments before engaging new suppliers or renewing high-risk service agreements.”
- From section ‘Objectives’, policy clause 3.3
This clause shifts the mindset from a simple check to a formal investigation, a crucial first step in building a defensible program that stands up to regulatory scrutiny.
Supplier Risk Under NIS2 and DORA: The New Expectations
Both NIS2 and DORA require organizations to systematically identify, assess, and continuously monitor risks across their supplier landscape. They transform supplier management from a procurement function into a core pillar of operational resilience and information security.
The new regulatory climate demands clear frameworks mapped tightly to established standards like ISO/IEC 27001:2022. Here is a high-level summary of what these frameworks expect from your supplier governance program:
| Requirement | NIS2 | DORA | ISO/IEC 27001:2022 Controls |
|---|---|---|---|
| Supplier Risk Assessment | Article 21(2)(d) | Articles 28–30 | 5.19, 5.21 |
| Contractual Security Clauses | Article 21(3), Article 22 | Article 30 | 5.20 |
| Continuous Monitoring | Article 21, Article 22 | Articles 30, 31 | 5.22 |
| Vulnerability and Incident Response | Article 23 | Article 9, 11 | 5.29, 8.8 |
A robust supplier audit program doesn’t need to be invented from scratch. The ISO/IEC 27001:2022 framework, particularly its Annex A controls, provides a powerful blueprint. At Clarysec, we guide clients to build their program around three interconnected controls that form a complete supplier governance lifecycle.
Building a Defensible Audit Framework: The ISO 27001:2022 Lifecycle
To build a program that satisfies regulators, you need a structured approach grounded in a globally recognized standard. The supplier security controls in ISO/IEC 27001:2022 provide a lifecycle for managing third-party risk from inception to termination. Let’s explore how Maria can use this lifecycle to build a defensible audit plan for CloudSphere.
Step 1: The Foundation - Information Security in Supplier Relationships (5.19)
Control 5.19 is the strategic starting point. It requires you to establish formal processes for identifying, assessing, and managing the information security risks associated with your entire supplier ecosystem. This is where you define what “high-risk” means for your organization and set the rules of the game.
Clarysec’s Zenith Controls: The Cross-Compliance Guide provides a detailed breakdown of 5.19, illustrating its role as a central hub for supplier governance. This control is intrinsically tied to related controls, such as 5.21 (Information security in the ICT supply chain), which covers hardware and software components, and 5.14 (Information transfer), which governs secure data exchange. You cannot effectively manage a supplier relationship without also controlling the technology they provide and the data you share.
For Maria, this means her audit of CloudSphere must go beyond their corporate security posture and dig into the security of the actual platform they provide. The Zenith Controls guide highlights that a strong implementation of 5.19 directly supports compliance with major regulations:
- NIS2 (Article 21(2)(d)): Obligates organizations to manage supply chain risk as a core part of their security framework.
- DORA (Articles 28–30): Mandates a robust ICT third-party risk management framework, including criticality classification and pre-contractual due diligence.
- GDPR (Article 28): Requires controllers to engage only processors who provide sufficient guarantees for data protection.
This control mandates supplier risk tiering, ongoing monitoring, and timely access revocation. Its purpose is to ensure that security is woven into the supplier lifecycle, not bolted on as an afterthought.
Step 2: The Enforcement - Addressing Information Security within Supplier Agreements (5.20)
A security requirement that isn’t in the contract is merely a suggestion. Control 5.20 is where governance becomes legally enforceable. For a high-risk supplier, your contract is your most powerful audit tool.
As Zenith Controls emphasizes, these agreements must be explicit. Vague promises of “industry-best security” are worthless. For a supplier like CloudSphere, Maria must verify the contract includes specific, measurable clauses that grant her organization tangible oversight:
- The Right to Audit: A clause explicitly giving her organization the right to conduct technical assessments, review evidence, or engage a third party to audit on their behalf.
- Breach Notification Timelines: Specific, aggressive timelines (e.g., within 24 hours of discovery) for notifying her company of a security incident, not just a vague “without undue delay.”
- Subcontractor (Fourth-Party) Management: A clause requiring the supplier to enforce the same security standards on their own critical subcontractors and to notify her of any changes. This is crucial for managing downstream risk.
- Secure Exit Strategy: Clear obligations for the return or certified destruction of data upon contract termination.
DORA is particularly prescriptive here. Article 30 lists mandatory contractual provisions, including unimpeded access for auditors and regulators, specific details on service locations, and comprehensive exit strategies. Auditors will sample high-risk supplier contracts and check for these clauses directly.
Step 3: The Continuous Loop - Monitoring, Review, and Change Management of Supplier Services (5.22)
The final piece of the lifecycle is control 5.22, which transforms supplier oversight from a point-in-time check into a continuous process. An audit should not be a surprise event but a validation point within an ongoing relationship of transparency.
This is where many organizations fall short. They get the contract signed and file it away. But for high-risk suppliers, the real work begins after onboarding. The Zenith Controls guide links 5.22 to critical operational processes like 8.8 (Management of technical vulnerabilities) and 5.29 (Information security during disruption). This means effective monitoring involves far more than an annual review meeting. It includes:
- Reviewing Third-Party Evidence: Actively obtaining and analyzing their SOC 2 Type II reports, ISO 27001 surveillance audit results, or penetration test summaries. The key is to review the exceptions and track their remediation.
- Monitoring for Incidents: Tracking publicly disclosed breaches or security incidents involving the supplier and formally assessing the potential impact on your organization.
- Managing Change: Implementing a process where any significant change in the supplier’s service, such as a new data center location or a new critical subcontractor, automatically triggers a risk re-assessment.
Clarysec’s Zenith Blueprint: An Auditor’s 30-Step Roadmap provides actionable guidance on this, particularly in Step 24, which covers subcontractor risk. It advises:
“For every critical supplier, identify if they use subcontractors (sub-processors) who may access your data or systems. Document how your information security requirements are flowed down to these parties… Where feasible, request a list of key subcontractors and ensure your right to audit or obtain assurance applies to them as well.”
This is a crucial point for Maria. Does CloudSphere use a third-party data analytics firm? Is their infrastructure hosted on a major public cloud? These downstream dependencies represent a significant, often invisible, risk that her audit must bring to light.
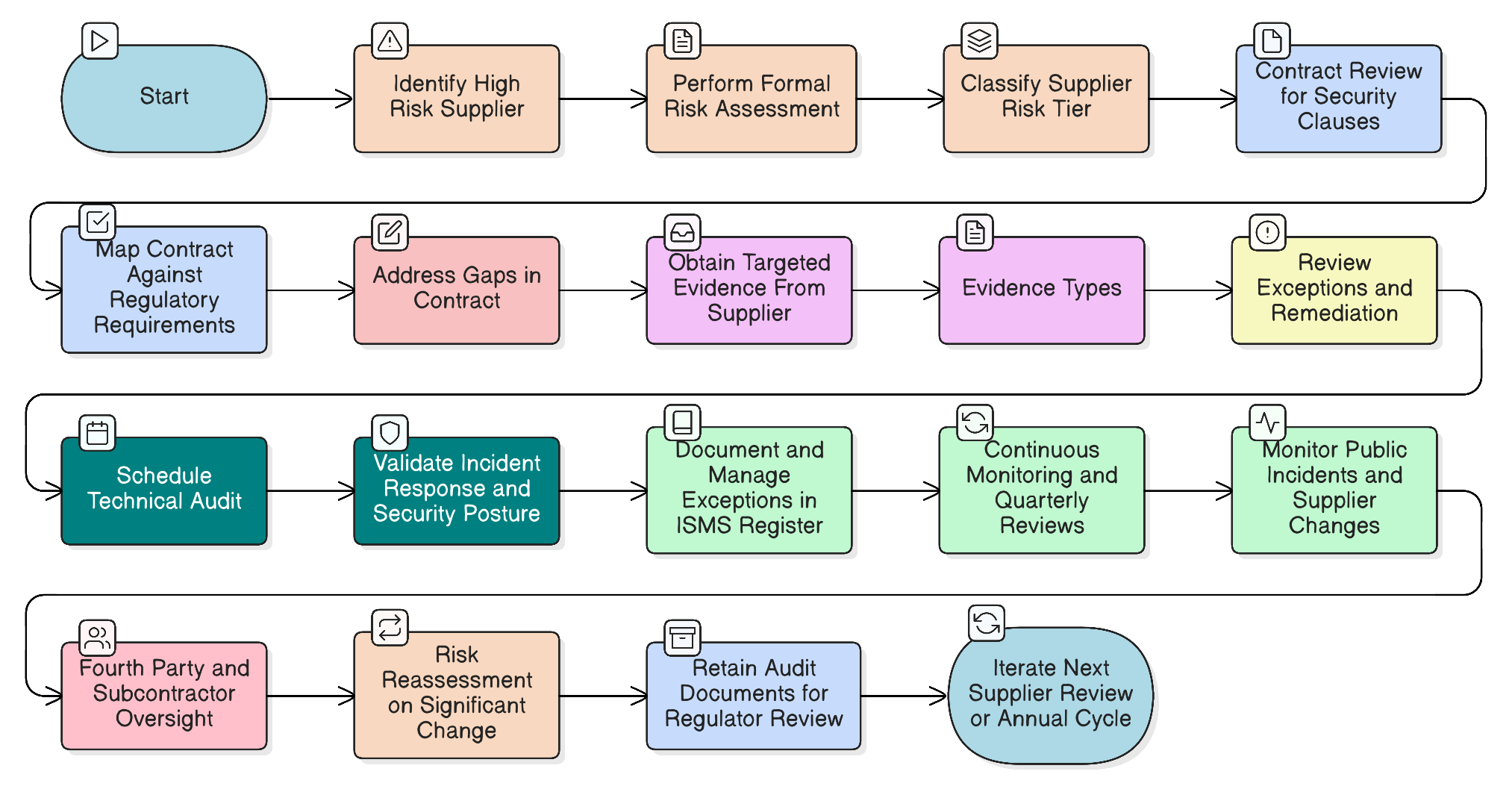
From Theory to Action: Maria’s Practical Audit Plan for CloudSphere
Armed with this ISO 27001:2022 lifecycle, Maria’s team drafts a new audit plan for CloudSphere that goes far beyond the questionnaire, demonstrating the mature, risk-based governance that regulators demand.
Contractual Review: They start by mapping the existing CloudSphere contract against DORA Article 30 and the best practices for control 5.20. They create a gap analysis report to inform the next renewal cycle and to prioritize areas for the current audit.
Targeted Evidence Request: Instead of a generic questionnaire, they send a formal request for specific evidence, including:
- The latest SOC 2 Type II report and a summary of how all noted exceptions were remediated.
- The executive summary of their most recent external penetration test.
- A complete list of all subcontractors (fourth parties) who will process or access their data.
- Proof that security requirements are contractually flowed down to those subcontractors.
- Logs or reports demonstrating timely patching of critical vulnerabilities (e.g., Log4j, MOVEit) over the last six months.
Technical Validation: They invoke their “right to audit” clause to schedule a technical deep-dive session with CloudSphere’s security team. The agenda focuses on their incident response playbooks, cloud security posture management tools, and data leakage prevention controls.
Formal Exception Management: If CloudSphere pushes back on providing certain evidence, Maria is prepared. Her organization’s governance process, defined in the Third-party and supplier security policy, is clear:
“High-risk exceptions (e.g., suppliers handling regulated data or supporting critical systems) must be approved by the CISO, Legal, and Procurement Leadership and entered into the ISMS Exception Register.”
- From section ‘Risk Treatment and Exceptions’, policy clause 7.3
This ensures that any refusal to provide evidence is not simply ignored but is formally risk-accepted at the highest levels of the organization, a process that auditors respect.
The Auditor’s Perspective: What Different Auditors Will Demand
To build a truly resilient program, you need to think like an auditor. Different audit frameworks come with different lenses, and anticipating their questions is key to success. Here’s a consolidated view of what various auditors would demand when reviewing your supplier governance program:
| Auditor Background | Key Focus Area and Controls | Evidence They Will Demand |
|---|---|---|
| ISO/IEC 27001:2022 Auditor | 5.19, 5.20, 5.22 | Supplier inventory with risk classifications; sampled contracts for high-risk suppliers to verify security clauses; records of due diligence and ongoing review meetings. |
| COBIT 2019 Auditor | APO10 (Manage Suppliers), DSS04 (Manage Continuity) | Evidence of ongoing performance monitoring against SLAs; documentation of how supplier-related incidents are managed; records of supplier risk reviews and change management. |
| DORA / Financial Regulator | Articles 28-30 | The contract with the critical ICT provider, mapped against DORA’s mandatory clauses; the concentration risk assessment; evidence of exit strategy testing or review. |
| NIST SP 800-53 Auditor | SA-9 (External System Services), SR Family (Supply Chain) | Proof of supply chain risk management plan; records of supplier compliance evidence (e.g., FedRAMP, SOC 2); documentation of fourth-party risk visibility. |
| ISACA / IT Auditor | ITAF Performance Standard 2402 | Logs proving that access for terminated supplier personnel was revoked promptly; evidence of unique, MFA-protected accounts for third-party access; incident response records. |
This multi-lens perspective shows that a robust program isn’t about satisfying one standard but about building a holistic governance framework that generates the evidence needed to satisfy them all.
Critical Pitfalls: Where Supplier Audits Fail
Many supplier oversight programs fall short due to common, avoidable mistakes. Be vigilant against these critical pitfalls:
- Auditing as an Event: Relying on one-off audits during onboarding or renewal instead of implementing continuous monitoring.
- Certification Complacency: Accepting an ISO or SOC 2 certificate at face value without reviewing the report details, scope, and exceptions.
- Vague Contracts: Failing to include explicit, enforceable clauses for audit rights, breach notification, and data handling.
- Poor Inventory Management: Being unable to produce a complete, risk-tiered inventory of all suppliers and the data they access.
- Ignoring Downstream Risk: Failing to identify and manage the risks posed by a supplier’s own critical subcontractors (fourth-party risk).
- Unverified Vulnerability Management: Trusting that a supplier is patching critical vulnerabilities without asking for evidence.
Actionable Checklist for High-Risk Supplier Audits
Use this checklist, adapted from the Zenith Blueprint, to ensure your audit process for every high-risk supplier is thorough and defensible.
| Step | Action | Evidence to Collect and Retain |
|---|---|---|
| Due Diligence | Perform and document a formal risk assessment before onboarding or renewal. | Completed supplier risk worksheet; classification record; due diligence report. |
| Contract Review | Verify that security, privacy, and audit clauses are present and enforceable. | Signed contract with highlighted clauses; legal review sign-off; data processing agreement. |
| Ongoing Monitoring | Schedule and conduct quarterly or annual reviews based on risk level. | Meeting minutes; reviewed SOC 2 / ISO 27001 reports; vulnerability scan summaries. |
| Subcontractor Oversight | Identify and document all critical downstream suppliers (fourth parties). | List of sub-processors provided by supplier; evidence of security flow-down clauses. |
| Vulnerability Management | Require evidence of a mature vulnerability management program. | Recent penetration test executive summary; sample vulnerability scan reports; patching timelines. |
| Incident Reporting | Test and validate the supplier’s incident notification process. | Records of past incident notifications; documented breach notification SLAs. |
| Change Management | Review all significant technical or organizational changes at the supplier. | Supplier change logs; risk re-assessment reports triggered by changes. |
| Regulatory Mapping | Map your implemented controls directly to NIS2, DORA, and GDPR requirements. | Internal compliance mapping table; evidence log for regulators. |
Conclusion: Building a Resilient and Defensible Supply Chain
The era of checkbox compliance for critical suppliers is over. The intense scrutiny from regulations like NIS2 and DORA demands a fundamental shift toward a model of continuous, evidence-based assurance. CISOs like Maria must lead the charge to move their organizations beyond the static questionnaire.
By building a program on the proven lifecycle of ISO/IEC 27001:2022 controls, you create a framework that is not only compliant but genuinely effective at reducing risk. This involves treating supplier security as a strategic discipline, embedding enforceable requirements in contracts, and maintaining vigilant oversight throughout the relationship.
Your organization’s security is only as strong as your weakest link, and in today’s interconnected ecosystem, that link often lies with a third party. It’s time to take back control.
Ready to Move Beyond the Questionnaire?
Clarysec’s integrated toolkits provide the foundation you need to build a world-class supplier risk management program that stands up to any audit.
- Download Our Policy Templates: Implement a robust governance framework with our enterprise-grade Third-Party and Supplier Security Policy and its counterpart for SMEs.
- Follow the Zenith Blueprint: Use our Zenith Blueprint: An Auditor’s 30-Step Roadmap to implement and audit a compliant ISMS, with dedicated steps for mastering supplier risk.
- Leverage Zenith Controls: Request a demo of our Zenith Controls: The Cross-Compliance Guide to map supplier controls to NIS2, DORA, GDPR, NIST, and more, ensuring your audit plan is comprehensive and defensible.```
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council