From Cloud Chaos to Audit-Proof: Architecting an ISO 27001:2022 Cloud Security Program with Clarysec’s Zenith Toolkit
The Compliance Chasm: Real-world Cloud Chaos in the Audit Spotlight
It’s a common nightmare for cloud-driven enterprises. The notification lands in CISO Maria’s inbox: “Pre-Audit Observation: Publicly Accessible S3 Bucket.” Panic rises. Only days before, the CEO requested full proof of ISO 27001:2022 compliance for a major client. Every asset, supplier, and access path is in scope, and regulatory crosswinds from NIS2, GDPR, DORA, and NIST complicate the landscape.
Maria’s team has deep technical skills. Their cloud migration was cutting-edge. But security engineering alone is not enough. The challenge is the gap between “doing” security, MFA configurations, asset tagging, buckets policies, and proving security with mapped policies, auditable records, and cross-framework alignment.
Scattered scripts and spreadsheets won’t satisfy audit demands. What the auditor and major client care about is perpetual compliance, with evidence mapped from every control to the standards that govern their sector. This is the compliance chasm: the difference between cloud operations and true, audit-ready security governance.
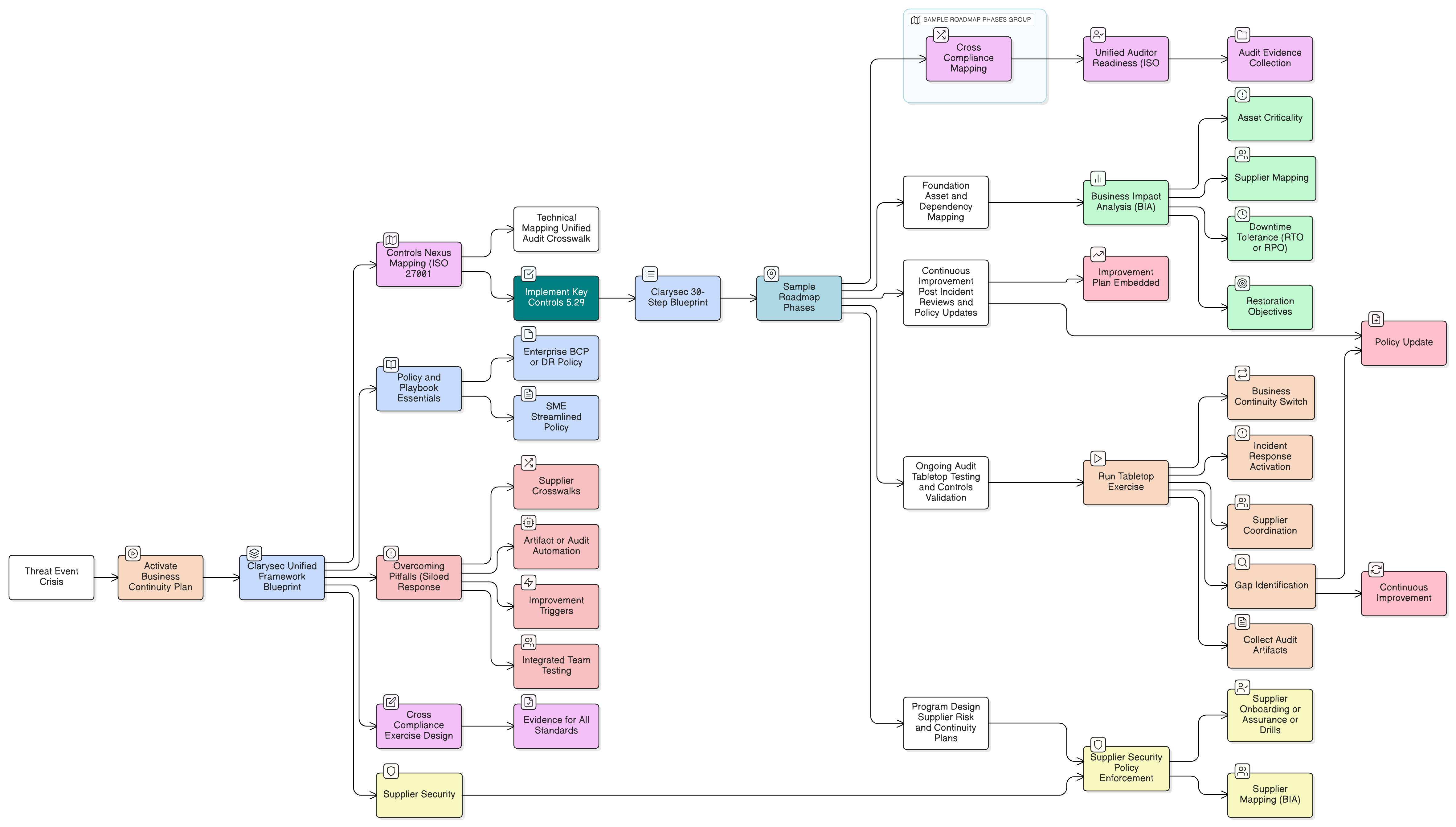
So how do enterprises bridge this chasm, moving from reactive cleanup to a cross-compliance fortress? The answer: structured frameworks, mapped standards, and operational toolkits, unified in Clarysec’s Zenith Blueprint.
Phase One: Precisely Scoping Your Cloud ISMS, The First Line of Audit Defense
Before deploying any technical controls, your Information Security Management System (ISMS) must be defined with surgical precision. It’s a foundational audit question: “What’s in scope?” A vague answer like “our AWS environment” signals instant red flags.
Maria’s team stumbled here initially, their scope a single sentence. But using Clarysec’s Zenith Blueprint Zenith Blueprint:
Phase 2: Scoping and Policy Foundation. Step 7: Define the ISMS Scope. For cloud environments, you must document which services, platforms, data sets, and business processes are included, down to VPCs, regions, and key personnel.
How scope clarity transforms compliance:
- It sets precise boundaries for technical controls and risk management.
- It ensures every cloud asset and data flow is inside the audit perimeter.
- It lets the auditor know exactly what to test, and allows your team to track every control’s effectiveness.
Sample ISMS Scope Table
| Element | Included in Scope | Details |
|---|---|---|
| AWS Regions | Yes | eu-west-1, us-east-2 |
| VPCs/Subnets | Yes | Only production VPCs/subnets |
| Applications | Yes | CRM, customer PII flows |
| Supplier Integrations | Yes | SSO provider, billing SaaS |
| Admin Personnel | Yes | CloudOps, SecOps, CISO |
Clarity here anchors every further compliance step.
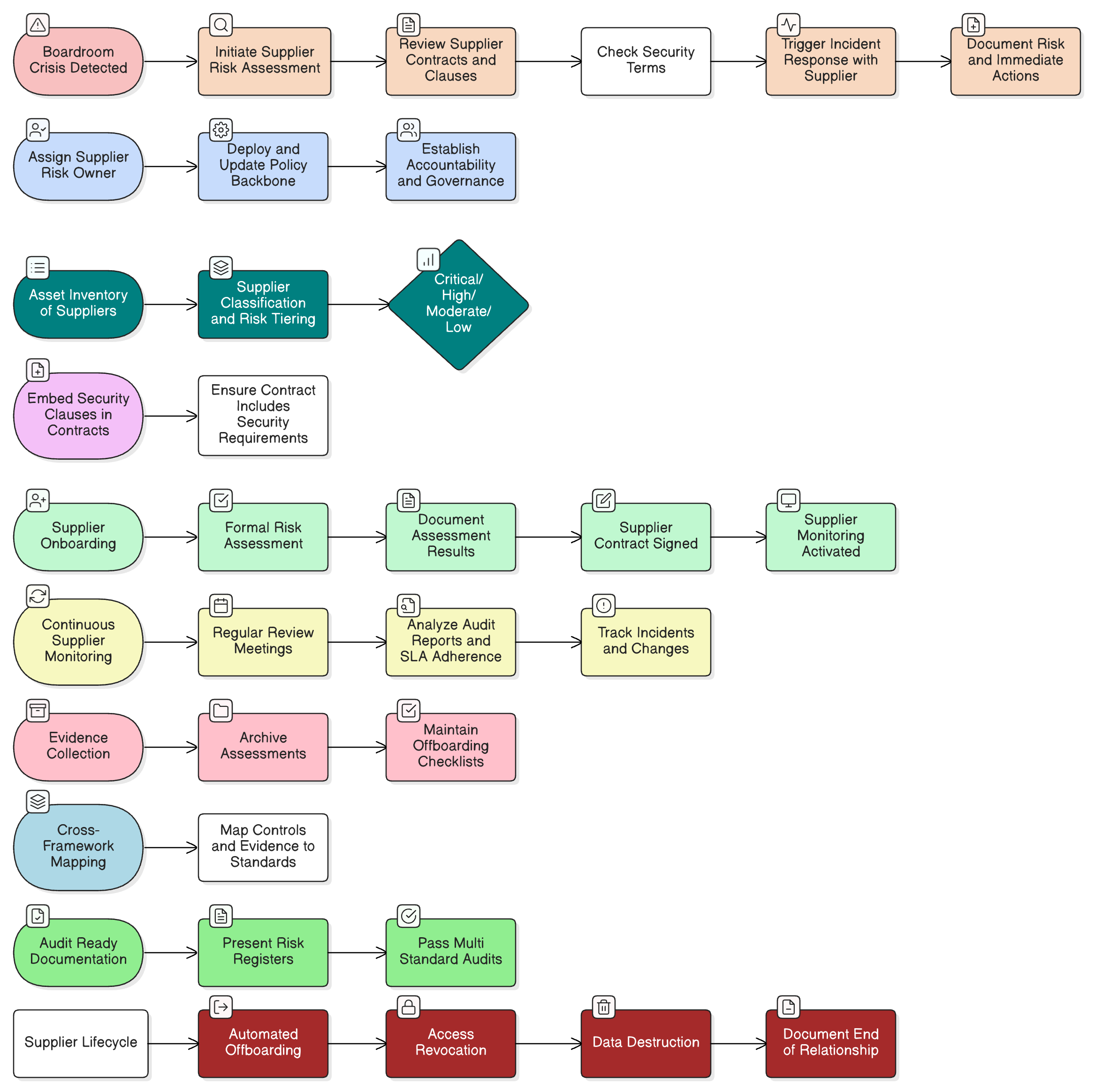
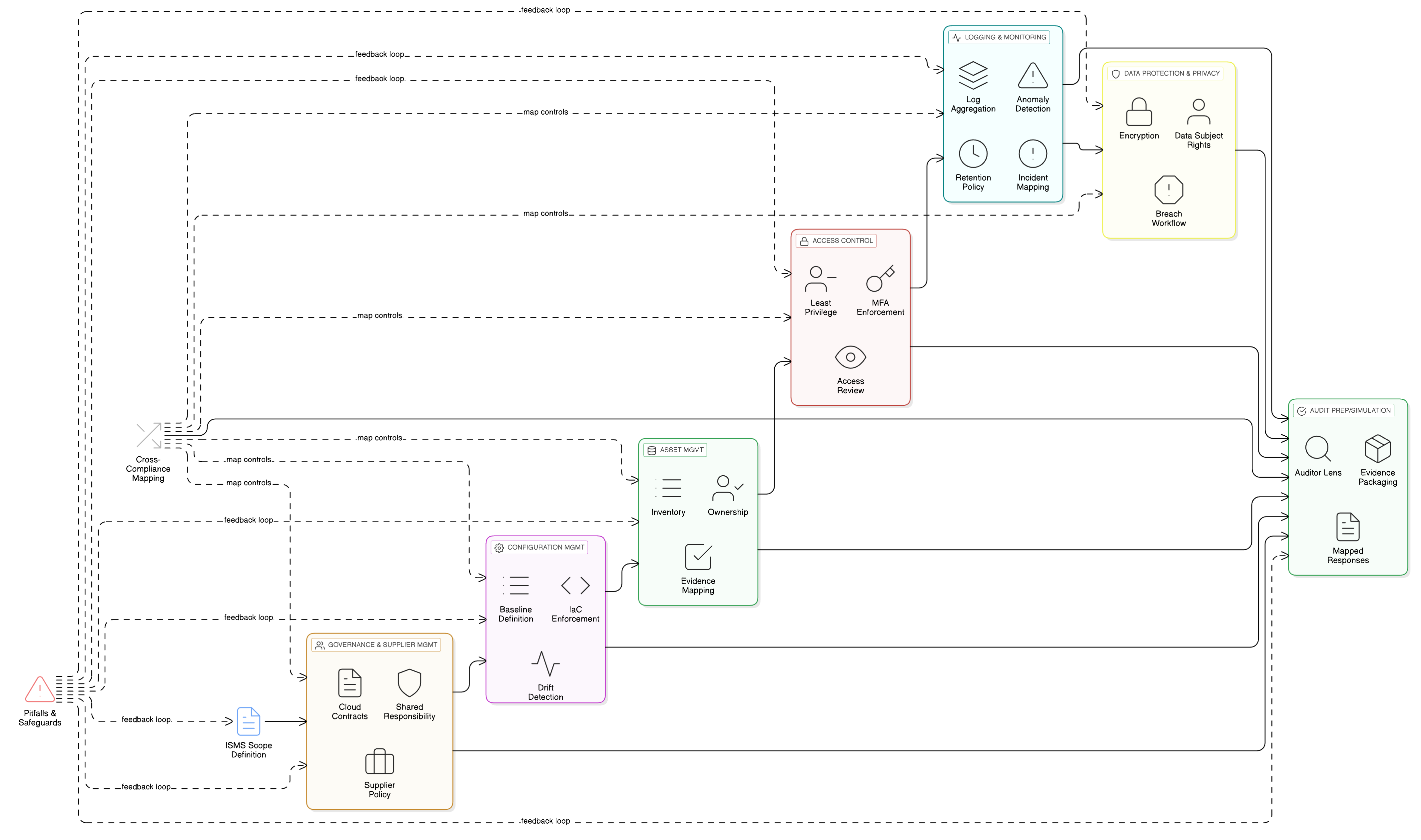
Governance of Cloud and Suppliers: ISO 27001 Control 5.23 and the Shared Responsibility Model
Cloud service providers are your most critical suppliers. Yet many organizations treat cloud contracts like IT utilities, neglecting governance, risk, and role assignment. ISO/IEC 27001:2022 ISO/IEC 27001:2022 responds with Control 5.23: Information security for use of cloud services.
As the Zenith Controls Zenith Controls guide explains, effective governance is not just about technical settings, it’s about management-approved policies and clear legal responsibility boundaries.
Establish a topic-specific policy for cloud usage, approved by management, that defines acceptable use, data classification, and due diligence for every cloud service. All cloud service agreements must outline security roles and shared responsibility for controls.
Clarysec’s Third-party and supplier security policy provides authoritative model clauses:
All suppliers accessing cloud resources must undergo risk assessment and approval, with contractual terms setting compliance standards and audit cooperation. Supplier access is time-bound, and termination requires documented evidence.
SMEs and the hyperscaler challenge:
When negotiating terms with AWS or Azure is impossible, document your responsibility under the provider’s standard terms, and map every control across the shared model. This stands as key audit evidence.
Cross-control mapping must include:
- Control 5.22: Monitoring and review of supplier service change.
- Control 5.30: ICT readiness for business continuity (including cloud exit strategy).
- Control 8.32: Change management, vital for cloud services.
Practical Governance Table: Supplier Security & Cloud Contracts
| Supplier Name | Asset Accessed | Contract Clause | Risk Assessment Done | Termination Process Documented |
|---|---|---|---|---|
| AWS | S3, EC2 | Supplier Policy 3.1 | Yes | Yes |
| Okta | Identity Mgmt | Standard Terms | Yes | Yes |
| Stripe | Billing Data | Standard Terms | Yes | Yes |
Configuration Management (Control 8.9): From Policy to Auditable Practice
Many audit failures stem from a breakdown in configuration management. A misconfigured S3 bucket exposed Maria’s company not because teams lacked expertise, but because they lacked enforceable, documented baselines and change management.
ISO/IEC 27002:2022 Control 8.9, Configuration management, mandates documented secure baselines and managed changes for all IT assets. Clarysec’s Configuration Management Policy Configuration Management Policy codifies:
Secure baseline configurations shall be developed, documented, and maintained for all systems, network devices, and software. Any deviation from these baselines must be formally managed through the change management process.
Audit-proof practice steps:
- Document Baselines: Define the secure state for each cloud service (S3 bucket, EC2 instance, GCP VM).
- Implement via Infrastructure-as-Code: Enforce baselines through Terraform or other deployment modules.
- Monitor for Configuration Drift: Use cloud-native or third-party tools (AWS Config, GCP Asset Inventory) for real-time compliance checks.
Example: Secure S3 Bucket Baseline Table
| Setting | Required Value | Rationale |
|---|---|---|
| block_public_acls | true | Prevents accidental public exposure at ACL level |
| block_public_policy | true | Prevents public exposure via bucket policy |
| ignore_public_acls | true | Adds defense-in-depth layer |
| restrict_public_buckets | true | Restricts public access to specific principals |
| server_side_encryption | AES256 | Ensures data at rest encryption |
| versioning | Enabled | Protects against deletion/modification errors |
With Clarysec’s Zenith Blueprint:
- Phase 4, Step 18: Implement Annex A controls for configuration management.
- Step 19-22: Monitor baselines with configuration drift alerts and tie logs to change management records.
Holistic Asset Management: Mapping ISO, NIST, and Regulatory Evidence
The backbone of compliance is your asset inventory. ISO/IEC 27001:2022 A.5.9 requires up-to-date inventory for all cloud and supplier assets. The Zenith Controls Zenith Controls audit guidance specifies continuous updates, automated discovery, and mapping of responsibility.
Asset Inventory Audit Table
| Asset Type | Location | Owner | Business Critical | Supplier Linked | Last Scan | Configuration Evidence |
|---|---|---|---|---|---|---|
| S3 Bucket X | AWS EU | John Doe | High | Yes | 2025-09-16 | MFA, encryption, public block |
| GCP VM123 | GCP DE | IT Ops | Moderate | No | 2025-09-15 | Hardened image |
| SaaS Connector | Azure FR | Procurement | Critical | Yes | 2025-09-18 | Supplier contract, access log |
Mapping for Auditors:
- ISO expects owner assignment, business criticality, and evidence links.
- NIST requires automated discovery and response logs.
- COBIT wants governance mapping and risk impact scoring.
Clarysec’s Zenith Blueprint guides you through establishing these baselines, verifying discovery tooling, and linking each asset to its audit record.
Access Control: Technical Enforcement Meets Policy Governance (Controls A.5.15–A.5.17)
Access management is the core of cloud risk and regulatory scrutiny. Multi-factor authentication (MFA), least privilege, and regular access reviews are mandated across frameworks.
Zenith Controls (A.5.15, A.5.16, A.5.17) guidance:
MFA in cloud environments must be proven with configuration evidence and mapped to enterprise-approved policies. Access rights must be tied to business roles, and reviewed regularly with logged exceptions.
Clarysec’s Identity and access management policy Identity and access management policy states:
Access rights to cloud services must be provisioned, monitored, and withdrawn according to business requirements and documented roles. Logs are reviewed regularly, with exclusions justified.
Clarysec Blueprint steps:
- Identify and map privileged accounts.
- Validate MFA with exportable logs for audit.
- Conduct regular access reviews, map findings to Zenith Controls attributes.
Logging, Monitoring, and Incident Response: Cross-Framework Audit Assurance
Effective logging and monitoring isn’t just technical, it must be policy-driven and audited for every key business system. ISO/IEC 27001:2022 A.8.16 and related controls demand centralized aggregation, anomaly detection, and policy-linked retention.
Zenith Controls (A.8.16) states:
Cloud logs must be centrally aggregated, anomaly detection enabled, and retention policies enforced. Logging is the evidence base for incident response across ISO 27035, GDPR Article 33, NIS2, and NIST SP 800-92.
Maria’s team, guided by Clarysec’s Logging and Monitoring playbook, made every SIEM log actionable and mapped it to audit controls:
Logging Evidence Table
| System | Log Aggregation | Retention Policy | Anomaly Detection | Last Audit | Incident Mapping |
|---|---|---|---|---|---|
| Azure SIEM | Centralized | 1 year | Enabled | 2025-09-20 | Included |
| AWS CloudTrail | Centralized | 1 year | Enabled | 2025-09-20 | Included |
Clarysec’s Blueprint, Phase 4 (Steps 19–22):
- Aggregate logs from all cloud providers.
- Map logs to incidents, breach notification, and policy clauses.
- Automate evidence export packages for audit.
Data Protection & Privacy: Encryption, Rights, and Breach Evidence
Cloud security is inseparable from privacy obligations, especially in regulated jurisdictions (GDPR, NIS2, sectoral regulations). ISO/IEC 27001:2022 A.8.24 and privacy-focused controls require proven, policy-backed encryption, pseudonymization, and data subject request logging.
Zenith Controls (A.8.24) summary:
Data protection controls must apply to all cloud-stored assets, referencing ISO/IEC 27701, 27018, and GDPR for breach notification and processor assessment.
Clarysec’s Data protection and privacy policy Data protection and privacy policy:
All personal and sensitive data in cloud environments is encrypted using approved algorithms. Data subject rights are honored, with access logs supporting request traceability.
Blueprint Steps:
- Review and log all encryption key management.
- Export access logs supporting GDPR request tracing.
- Simulate breach notification workflows for audit evidence.
Data Protection Crosswalk Table
| Control | Attribute | ISO/IEC Standards | Regulatory Overlay | Audit Evidence |
|---|---|---|---|---|
| A.8.24 | Encryption, Privacy | 27018, 27701 | GDPR Art.32, NIS2 | Encryption config, access record, breach log |
Cross-Compliance Mapping: Maximizing Framework Efficiency
Maria’s company faced overlapping obligations (ISO 27001, DORA, NIS2, NIST CSF, COBIT 19). With Zenith Controls Zenith Controls, controls are mapped for cross-framework leverage.
Framework Mapping Table
| Framework | Clause/Article | ISO 27001 Control Addressed | Audit Evidence Provided |
|---|---|---|---|
| DORA | Article 9 (ICT Risk) | 5.23 (Cloud Supplier) | Supplier policy, contract logs |
| NIS2 | Article 21 (Supply Chain) | 5.23 (Supplier Management), 8.9 (Configurations) | Asset and supplier audit trail |
| NIST CSF | PR.IP-1 (Baselines) | 8.9 (Configuration Mgmt) | Secure baseline, change log |
| COBIT 2019 | BAI10 (Config Mgmt) | 8.9 (Configuration Mgmt) | CMDB, process metrics |
Any control implemented with audit-ready evidence serves multiple frameworks. This multiplies compliance efficiency and ensures resilience in a shifting regulatory landscape.
Facing the Auditor: Internal Preparation Across Methodologies
An audit is not a single lens experience. Whether ISO 27001, NIST, DORA, or COBIT, each auditor will probe with their own focus. With Clarysec’s toolkit, your evidence is mapped and packaged for all perspectives:
Sample Auditor Questions and Evidence Response
| Auditor Type | Focus Areas | Sample Requests | Clarysec Evidence Mapped |
|---|---|---|---|
| ISO 27001 | Policy, asset, logged control | Scope docs, access logs | Zenith Blueprint, mapped policies |
| NIST Assessor | Operations, change lifecycle | Baseline updates, incident logs | Change mgmt log, incident playbook |
| COBIT/ISACA | Governance, metrics, process owner | CMDB, KPI dashboard | Governance mappings, ownership logs |
By anticipating each lens, your team demonstrates not just compliance but operational excellence.
Pitfalls and Protection: How Clarysec Prevents Common Audit Failures
Typical missteps without Clarysec:
- Out-of-date asset inventories.
- Misaligned access controls.
- Missing contractual compliance clauses.
- Controls not mapped to DORA, NIS2, GDPR.
With Clarysec’s Zenith Blueprint and Toolkit:
- Mapped checklists aligned to operational steps.
- Automated evidence collection (MFA, asset discovery, supplier review).
- Sample audit packages generated for every major framework.
- Every “what” anchored in “why”, policy and standard crosswalk.
Clarysec Evidence Table
| Audit Step | Evidence Type | Zenith Controls Mapping | Frameworks | Policy Reference |
|---|---|---|---|---|
| Asset Inventory | CMDB export | A.5.9 | ISO, NIS2, COBIT | Asset management policy |
| MFA Validation | Log files, screenshots | A.5.15.7 | ISO, NIST, GDPR | Access management policy |
| Supplier Review | Contract scans, access logs | A.5.19, A.5.20 | ISO, DORA, GDPR | Supplier security policy |
| Logging Audit | SIEM outputs, retention proof | A.8.16 | ISO, NIST, GDPR | Monitoring policy |
| Data Protection | Encryption keys, breach records | A.8.24 | ISO, GDPR, NIS2 | Data protection policy |
End-to-End Audit Simulation: From Architecture to Evidence
Clarysec’s toolkit navigates every phase:
- Start: Export asset list, map to policy and controls.
- Access: Validate MFA with evidence, link to access management procedures.
- Supplier: Cross-reference contracts with supplier policy checklist.
- Logging: Produce log retention exports for review.
- Data Protection: Show encrypted asset registry, breach response package.
Each evidence item traces to Zenith Controls attributes, cross-links to policy clause and supports every framework demanded.
Result: Audit is completed with confidence, demonstrating cross-compliance resilience and operational maturity.
Conclusion & Action Step: Move from Chaos to Perpetual Compliance
Maria’s journey, moving her company from reactive patches to proactive governance, is a roadmap for every cloud-driven organization. Configuration, supplier security, asset management, and data protection cannot stand alone. They must be mapped to rigorous standards, enforced through documented policies, and evidenced for every audit scenario.
Three pillars drive success:
- Clear Scope: Define clear audit boundaries using the Zenith Blueprint.
- Strong Policies: Adopt Clarysec’s policy templates for every critical control.
- Verifiable Controls: Turn technical settings into auditable records mapped across standards.
Your organization needn’t wait for the next panic-bearing audit notification. Build resilience now, leveraging Clarysec’s unified toolkits, Zenith Blueprint, and cross-regulatory mapping for audit-proof, perpetual compliance.
Ready to bridge your compliance chasm and lead in secure cloud operations?
Explore Clarysec’s Zenith Blueprint and download our toolkits and policy templates to architect your audit-ready cloud program. Request an assessment or demo, and move from cloud chaos to an enduring compliance fortress.
References:
- Zenith Blueprint: An Auditor’s 30-Step Roadmap Zenith Blueprint
- Zenith Controls: The Cross-Compliance Guide Zenith Controls
- Configuration Management Policy Configuration Management Policy
- Identity and access management policy Identity and access management policy
- Third-party and supplier security policy Third-party and supplier security policy
- Data protection and privacy policy Data protection and privacy policy
- ISO/IEC 27001:2022
- ISO/IEC 27002:2022
- ISO/IEC 27036-2:2023
- ISO/IEC 27701:2019
- NIS2, GDPR, DORA, NIST, COBIT 19
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council