The Data Graveyard: A CISO's Guide to Compliant, Auditable Data Disposal
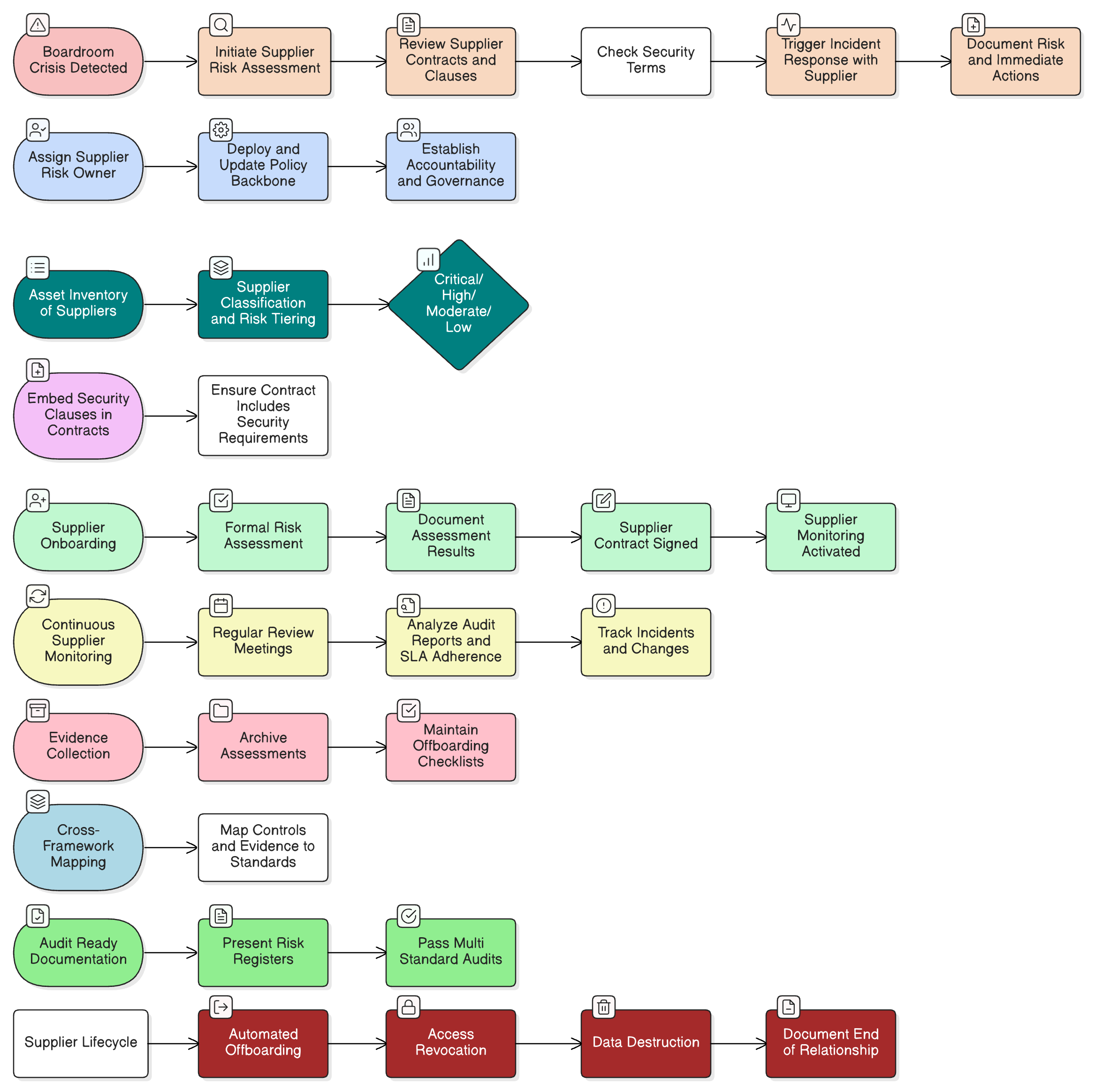
Maria, the CISO of a rapidly growing fintech firm, felt a familiar knot tighten in her stomach. The external GDPR audit was six weeks away, and a routine asset inventory check had just unearthed a ghost from the company’s past: a locked storage room in their old office building, filled with decommissioned servers, dusty backup tapes, and stacks of old employee laptops. The “data graveyard,” as her team grimly called it, was no longer a forgotten problem. It was a ticking compliance bomb.
What sensitive customer data, intellectual property, or personally identifiable information (PII) was lurking on those drives? Had any of it been properly sanitized? Did records even exist to prove it? The lack of answers was the real threat. In the world of information security, what you don’t know can, and often will, hurt you.
This scenario isn’t unique to Maria. For countless CISOs, compliance managers, and business owners, legacy data represents a massive, unquantified risk. It’s a silent liability that inflates your attack surface, complicates data subject requests, and creates a minefield for auditors. The core question is simple, yet profoundly challenging: What should you do with sensitive data you no longer need? The answer isn’t just hitting “delete.” It’s about building a defensible, repeatable, and auditable process for information lifecycle management, from creation to secure destruction.
The High Stakes of Data Hoarding
Keeping data forever “just in case” is a relic of a bygone era. Today, it’s a demonstrably dangerous strategy. Sensitive data that lingers beyond its useful or required lifetime exposes your organization to a host of threats, from compliance penalties and privacy breaches to accidental leaks and even ransomware extortion.
Holding onto data past its retention date creates several critical risks:
- Compliance Failure: Regulators are cracking down on unnecessary data retention. A data graveyard is a direct violation of privacy principles and can lead to significant fines.
- Increased Breach Impact: If a breach occurs, every piece of legacy data you hold becomes a liability. A hacker exfiltrating five years of old customer data is exponentially more damaging than exfiltrating one year’s worth.
- Operational Inefficiency: Managing, securing, and searching through mountains of irrelevant data drains resources, slows down systems, and makes fulfilling “right to erasure” requests under GDPR nearly impossible.
Many organizations mistakenly believe that hitting ‘delete’ or removing a database entry makes data vanish. It rarely does, leaving residual data across physical, virtual, and cloud landscapes.
Regulatory Mandates: The End of “Keep It Forever”
The rules have shifted. A convergence of global regulations explicitly requires that personal and sensitive information be retained only as long as necessary and be securely erased when that period ends. This isn’t a suggestion; it’s a legal and operational mandate.
Clarysec’s Zenith Blueprint: An Auditor’s 30-Step Roadmap summarizes the cross-regulatory imperative for secure data disposal:
✓ GDPR Article 5(1)(e), Article 17, Article 32(1)(b–d): Requires that personal data is kept no longer than necessary, supports the right to erasure (“right to be forgotten”), and mandates secure erasure when no longer needed.
✓ NIS2 Article 21(2)(a, d): Demands risk-based technical and organizational measures to ensure data is securely deleted when not required.
✓ DORA Article 9(2)(a–c): Requires the protection of sensitive information throughout its lifecycle, including secure destruction.
✓ COBIT 2019 – DSS01.05 & DSS05.07: Addresses secure data deletion, destruction of media, and removal of information assets at end-of-life.
✓ ITAF 4th Edition – Domain 2.1.6: Requires evidence of secure data destruction and disposal in accordance with legal and regulatory obligations.
This means your organization must have documented, enforced, and auditable processes for data deletion. This applies not just to paper records or hard drives, but to every corner of your digital estate, including cloud storage, backups, application data, and third-party suppliers.
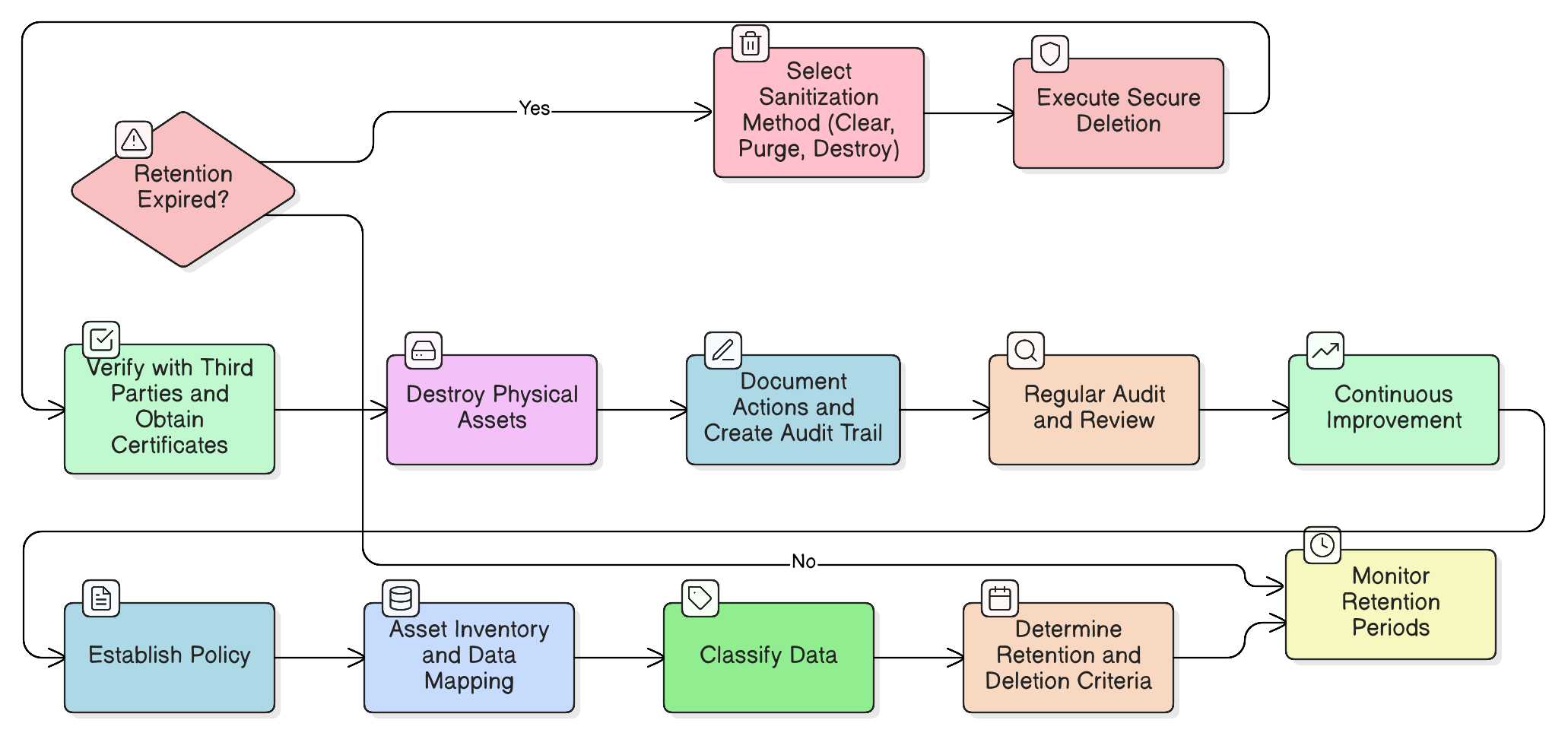
From Chaos to Control: Building a Policy-Driven Disposal Program
The first step in defusing the data graveyard bomb is to establish a clear, authoritative framework. A robust disposal program begins not with shredders and degaussers, but with a well-defined policy. This document serves as the single source of truth for your entire organization, aligning business, legal, and IT teams on how data is managed and destroyed.
Clarysec’s Data Retention and Disposal Policy provides a blueprint for this. One of its core objectives is stated clearly in policy clause 3.1:
“To ensure that data is retained only for as long as legally, contractually, or operationally necessary, and securely disposed of when no longer required.”
This simple statement shifts the organizational mindset from “keep everything” to “keep what’s necessary.” The policy establishes a formal process, ensuring that decisions are not arbitrary but are tied to concrete obligations. As policy clause 1.2 in the Data Retention and Disposal Policy highlights, it is designed to support ISO/IEC 27001:2022 implementation by enforcing control over data storage duration and ensuring readiness for audits and regulatory inspections.
For smaller organizations, a heavyweight enterprise policy can be overkill. The Data Retention and Disposal Policy - SME offers a streamlined alternative, focusing on the essentials, as stated in policy clause 1.1:
“The purpose of this policy is to define enforceable rules for the retention and secure disposal of information within an SME environment. It ensures records are kept only for the duration required by law, contractual obligation, or business necessity, and securely destroyed thereafter.”
Whether for an enterprise or an SME, the policy is the cornerstone. It provides the authority to act and the framework to ensure actions are consistent, defensible, and aligned with security best practices.
Executing the Plan: ISO/IEC 27001:2022 Controls in Practice
With a policy in place, Maria can now translate its principles into concrete actions, guided by the controls within ISO/IEC 27001:2022. Two controls are paramount here:
- Control 8.10 Information Deletion: This requires that “Information stored in information systems, devices, or in any other storage media should be deleted when no longer required.”
- Control 7.14 Secure disposal or re-use of equipment: This focuses on the physical hardware, ensuring that storage media is properly sanitized before the equipment is disposed of, repurposed, or sold.
But what does “securely deleted” actually mean? This is where auditors separate the contenders from the pretenders. According to the Zenith Blueprint, true deletion is far more than moving a file to the recycle bin. It involves methods that render data unrecoverable:
For digital systems, deletion should mean secure erasure, not just pressing ‘delete’ or emptying the recycle bin. True deletion includes:
✓ Overwriting the data (e.g., with DoD 5220.22-M or NIST 800-88 methods),
✓ Cryptographic erasure (e.g., destroying encryption keys used to protect the data),
✓ Or applying secure wipe utilities before decommissioning devices.
For physical records, the Zenith Blueprint recommends cross-cut shredding, incineration, or using certified disposal services. This practical guidance helps organizations move from policy to procedure, defining the exact technical steps required to meet the control’s objective.
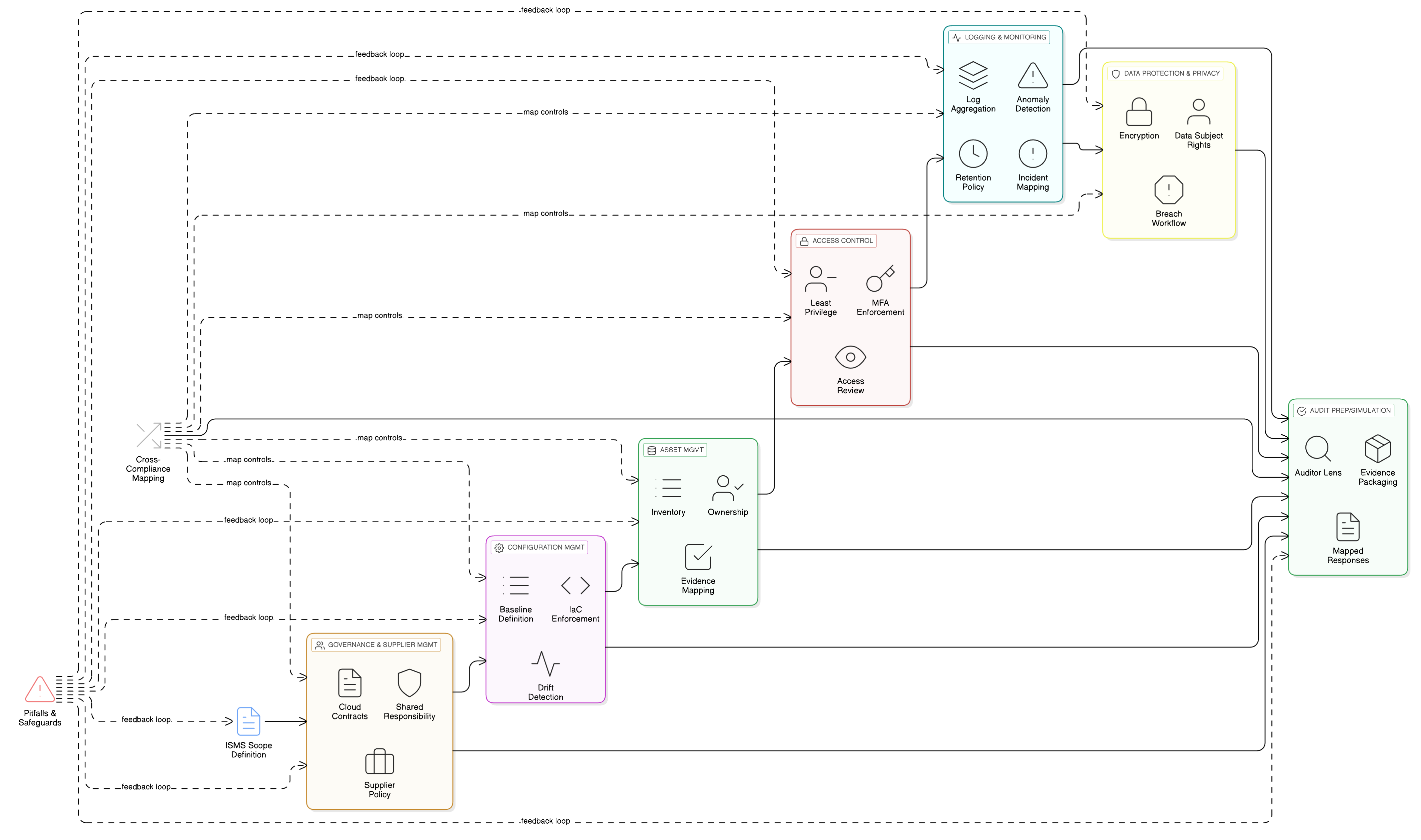
A Holistic View: The Interconnected Security Web of Disposal
Tackling the data graveyard isn’t a single-threaded task. Effective data disposal is deeply interconnected with other security domains. This is where a holistic view, as provided by Clarysec’s Zenith Controls: The Cross-Compliance Guide, becomes indispensable. It acts as a compass, revealing how one control relies on many others to function effectively.
Let’s examine Control 7.14 (Secure disposal or re-use of equipment) through this lens. The Zenith Controls guide shows it is not an isolated activity. Its success depends on a web of related controls:
- 5.9 Inventory of assets: You cannot securely dispose of what you don’t know you have. Maria’s first step must be to inventory every server, laptop, and tape in that storage room. An accurate asset inventory is the foundation.
- 5.12 Classification of information: The method of disposal depends on the data’s sensitivity. You must know what you’re destroying to choose the appropriate sanitization level.
- 5.34 Privacy and protection of PII: Equipment often contains personal data. The disposal process must ensure all PII is irreversibly destroyed, linking directly to privacy obligations under regulations like GDPR.
- 8.10 Information Deletion: This control provides the “what” (delete information when no longer needed), while 7.14 provides the “how” for the underlying physical media. They are two sides of the same coin.
- 5.37 Documented operating procedures: Secure disposal must follow a defined, repeatable process to ensure consistency and create an audit trail. Ad-hoc disposals are a red flag for any auditor.
This interconnectedness demonstrates that a mature security program treats data disposal not as a cleanup task, but as an integrated part of its Information Security Management System (ISMS).
Technical Deep Dive: Media Sanitization and Supporting Standards
To implement these controls effectively, it’s vital to understand the different levels of media sanitization, as outlined in frameworks like NIST SP 800-88. These methods offer a layered approach to ensure data is unrecoverable, appropriate to its sensitivity.
| Sanitization Method | Description | Use Case Example |
|---|---|---|
| Clear | Overwriting data with non-sensitive data using standard read/write commands. Protects against simple data recovery techniques. | Repurposing a laptop for another employee within the same secure environment. |
| Purge | Advanced techniques like degaussing (for magnetic media) or cryptographic erase. Resists laboratory recovery attacks. | Decommissioning a server that contained sensitive but not top-secret financial data. |
| Destroy | Physical destruction of the media (shredding, incineration, pulverizing). Data is impossible to recover. | Disposing of hard drives containing highly confidential intellectual property or PII. |
Choosing the right method depends on the data’s classification. Guidance from specialized standards is invaluable here. A robust program draws on a wide net of supporting frameworks beyond just ISO/IEC 27001:2022.
| Standard | Key Relevance |
|---|---|
| ISO/IEC 27005:2022 | Embeds deletion as a risk treatment option and identifies insecure disposal as a high-impact risk. |
| ISO/IEC 27701:2019 | Requires specific controls for the deletion of PII when reusing or disposing of equipment. |
| ISO/IEC 27018:2019 | Mandates the secure erasure of cloud-based PII before any asset containing it is disposed of. |
| ISO/IEC 27017:2015 | Provides cloud-specific guidance, ensuring asset sanitization when terminating virtual or physical resources. |
| NIST SP 800-88 | Offers detailed technical guidelines for media sanitization, defining the Clear, Purge, and Destroy techniques. |
The Auditor is Coming: How to Prove Your Process Works
Passing an audit isn’t just about doing the right thing; it’s about proving you did the right thing. For Maria, this means documenting every step of the disposal process for the assets in her data graveyard. The Zenith Blueprint provides a clear checklist of what auditors will demand for Control 8.10 (Information Deletion):
“Provide your Information Deletion Policy… Demonstrate technical enforcement through configured retention settings in your business systems… They may ask for evidence of secure deletion methods: wiping disks with approved tools… or secure document disposal. If you delete data upon contract expiration… show the audit trail or ticket confirming it.”
To satisfy auditors, you must create a comprehensive evidence package for each disposal event. A Data Deletion Register is essential.
Audit Trail Example Table
| Asset ID | Asset Type | Location | Deletion Method | Evidence/Log | Approver |
|---|---|---|---|---|---|
| SRV-FIN-04 | Server HDD | On-prem DC | Degaussed + Physical Shred | Disposal Cert #DC44C8 | Data Owner |
| CUST-DB-BKP-112 | LTO-8 Tape | Iron Mountain | Incinerated (certified) | Destruction Cert #IM7890 | IT Ops |
| PROJ-X-DATA | AWS S3 Bucket | eu-west-1 | Lifecycle Policy ‘DeleteObject’ | AWS Erasure Log #1192 | Cloud Ops |
| HR-LAPTOP-213 | Laptop SSD | IT Storage | Cryptographic Erase | Wipe Log #WL5543 | IT Support |
Auditors approach this from different perspectives. The Zenith Controls guide details how various audit frameworks scrutinize the process:
| Audit Framework | Evidence Required | Approach |
|---|---|---|
| ISO/IEC 19011:2018 | Observation of practices, review of retention logs and disposal certificates. | Interviews, Document Review, Sampling |
| ISACA ITAF | Sufficient and reliable evidence triangulation from policies, logs, and interviews. | Triangulation |
| NIST SP 800-53A | Records proving that approved sanitization methods (per NIST SP 800-88) were used. | Technical Testing, Records Inspection |
| COBIT 2019 | Proof of governance oversight, risk management integration, and reporting. | Governance Review, Process Walkthrough |
Common Pitfalls and How to Avoid Them
Even with a policy in place, many organizations stumble during execution. Here are common pitfalls and how a structured approach helps solve them:
| Pitfall | How a Clarysec-Guided Approach Helps |
|---|---|
| Shadow Data: Data lives on in forgotten backups, archives, or shadow IT. | An enforced Retention Register linked to a complete asset inventory ensures all copies are identified and tracked for disposal. |
| Logical Deletion Only: Data is marked as deleted but remains recoverable. | The policy mandates secure erasure methods (overwriting, crypto-erase, physical destruction) based on data classification. |
| Cloud Provider Ambiguity: Unclear processes for secure deletion in SaaS/IaaS. | Supplier contracts are updated to require erasure certification or verifiable log confirmation upon service termination. |
| Manual and Error-Prone Processes: Relying on individuals to remember to delete data. | Automate wherever possible using system lifecycle policies (e.g., in M365, AWS S3). Require documented evidence for all manual deletions. |
| No Proof of Disposal: Lack of auditable records to satisfy regulators. | A centralized Data Deletion Register and the retention of all third-party destruction certificates create a defensible audit trail. |
Conclusion: Turn Your Data Graveyard into a Strategic Advantage
Six weeks later, Maria walked the GDPR auditor through her team’s work. The storage room was empty. In its place was a digital archive containing a meticulous record for every decommissioned asset: inventory logs, data classification reports, sanitization procedures, and signed certificates of destruction. What was once a source of anxiety was now a showcase of mature risk management.
The data graveyard is a symptom of a reactive security culture. Transforming it requires a proactive, policy-driven approach. It demands that we see data disposal not as an IT cleanup chore, but as a strategic security function that reduces risk, ensures compliance, and demonstrates a commitment to protecting sensitive information.
Ready to tackle your own data graveyard? Start by building the foundation for an evidence-based, resilient approach to information lifecycle management.
Actionable Next Steps:
- Establish the Foundation: Implement a clear and enforceable policy using Clarysec’s templates, such as the Data Retention and Disposal Policy or the Data Retention and Disposal Policy - SME.
- Map Your Universe: Create and maintain a comprehensive inventory of all information assets. You can’t dispose of what you don’t know you have.
- Define and Enforce Retention: Establish a formal retention schedule that links every data type to a legal, contractual, or business requirement, and then automate its enforcement.
- Operationalize Secure Disposal: Integrate secure deletion and sanitization procedures into your standard operating procedures for IT asset decommissioning.
- Document Everything: Create and maintain an audit-proof trail for every disposal action, including logs, tickets, and third-party certificates.
- Extend to Your Supply Chain: Ensure your contracts with cloud providers and other suppliers include strict requirements for secure data disposal and demand proof of compliance.
Every byte of unnecessary data is a risk. Take back control, harden your compliance, streamline audits, and reduce breach exposure.
Contact us for a demonstration or explore the full Zenith Blueprint and Zenith Controls library to begin your journey.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council