Encryption at Rest Isn't an Option? A CISO's Guide to Bulletproof Compensating Controls
The auditor’s finding landed on CISO Sarah Chen’s desk with a familiar thud. A critical, revenue-generating legacy database, the operational heart of the company’s manufacturing line, could not support modern data-at-rest encryption. Its underlying architecture was a decade old, and the vendor had long since ceased providing security updates. The auditor, rightly, flagged it as a major risk. The recommendation: “Encrypt all sensitive data at rest using industry-standard algorithms.”
For Sarah, this wasn’t just a technical problem; it was a business continuity crisis. Upgrading the system would mean months of downtime and millions in cost, a non-starter for the board. But leaving a trove of sensitive intellectual property unencrypted was an unacceptable risk, a clear deviation from their information security management system (ISMS).
This scenario is the real world of cybersecurity, where perfect solutions are rare and compliance cannot be put on pause. It happens when critical backup files are stored on legacy systems, when a key SaaS provider cites “technical limitations,” or when high-performance applications break under the weight of encryption overhead. The textbook answer, “just encrypt it,” often collides with messy reality.
So, what happens when the primary, prescribed control is off the table? You don’t simply accept the risk. You build a smarter, more resilient defense using compensating controls. This isn’t about making excuses; it’s about demonstrating mature, risk-based security management that can withstand the toughest audit scrutiny.
Why Encryption at Rest Is a High-Stakes Requirement
Encryption at rest is a foundational control in all modern security frameworks, including ISO/IEC 27001:2022, GDPR Article 32, NIS2, DORA, and NIST SP 800-53 SC-28. Its purpose is simple but critical: to render stored data unreadable if physical or logical defenses fail. A lost backup tape or a stolen server containing unencrypted data isn’t just a technical slip-up; it’s often a legally notifiable data breach.
The risks are clear and significant:
- Theft or loss of portable media like USB drives and backup tapes.
- Data exposure from unmanaged, forgotten, or legacy devices.
- Inability to apply native disk or database encryption in specific SaaS, cloud, OT, or legacy contexts.
- Data recovery risks if encryption keys are lost or mismanaged.
These requirements are not just technical, they are legal mandates. GDPR Article 32 and DORA Articles 5 and 10 explicitly recognize encryption as an “appropriate technical measure.” NIS2 designates it as a baseline for ensuring system and information integrity. When this primary defense is not feasible, the burden of proof shifts to the organization to demonstrate that its alternative measures are equally effective.
Shifting from a Single Checkbox to a Layered Defense
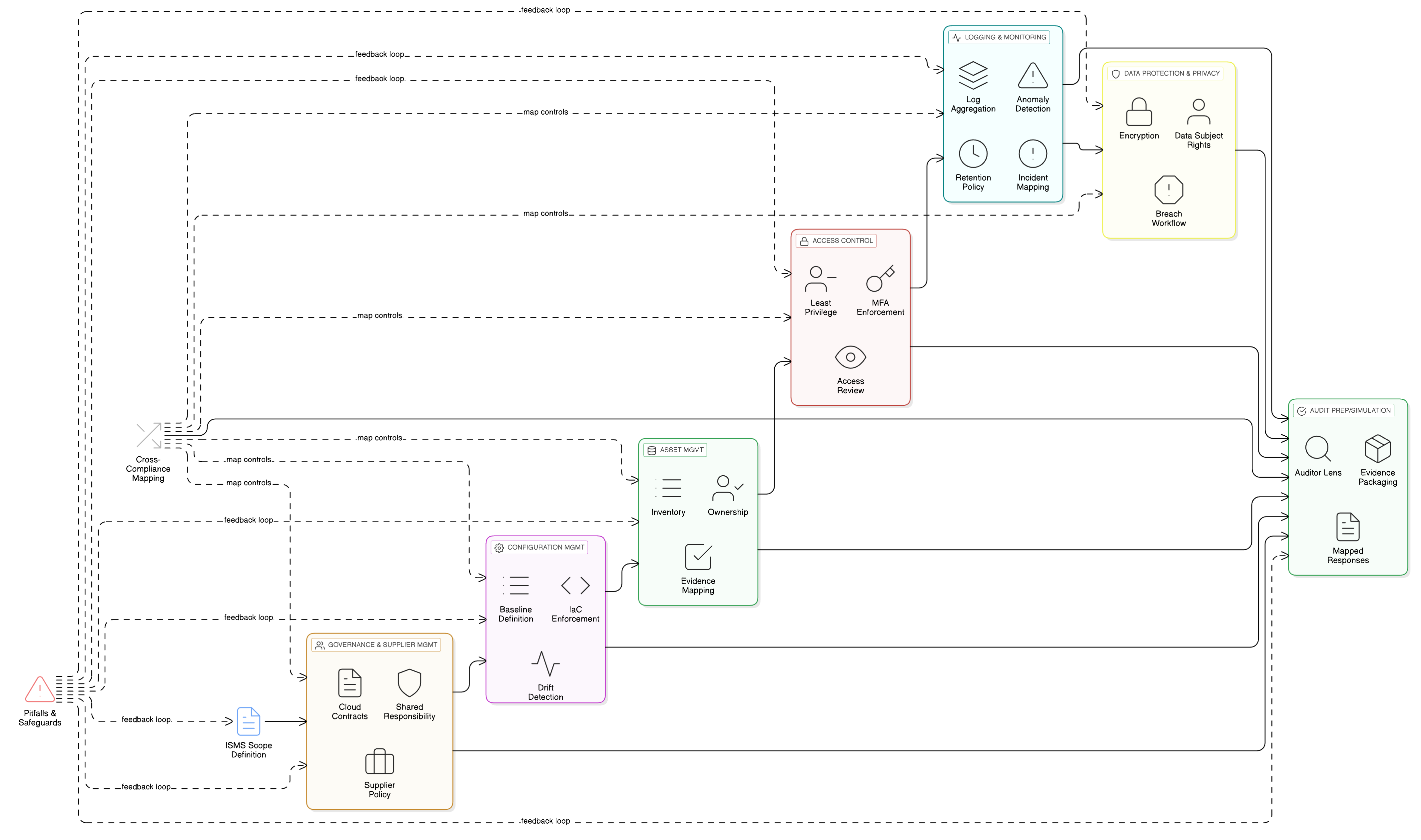
The knee-jerk reaction to an audit finding like Sarah’s is often panic. But a well-structured ISMS anticipates these situations. Sarah’s first move wasn’t to call the infrastructure team; it was to open her organization’s Cryptographic Controls Policy, a document built using Clarysec’s enterprise templates. She navigated directly to a clause that provided the foundation for her strategy.
According to the Cryptographic Controls Policy, Section 7.2.3 explicitly outlines the process for defining:
“Specific compensating controls to be applied”
This clause is a CISO’s best friend. It acknowledges that a one-size-fits-all approach to security is flawed and provides a sanctioned pathway to address risk. The policy doesn’t operate in a vacuum. As stated in clause 10.5, it is directly linked to the Data Classification and Labeling Policy, which “Defines the classification levels (e.g., Confidential, Regulated) that trigger specific encryption requirements.”
This linkage is critical. The data in the legacy database was classified as “Confidential,” which is why the lack of encryption was flagged. Now, Sarah’s mission was clear: build a fortress of compensating controls so robust that it would mitigate the risk of exposure to an acceptable level.
Architecting a Defensible Strategy with the Zenith Blueprint
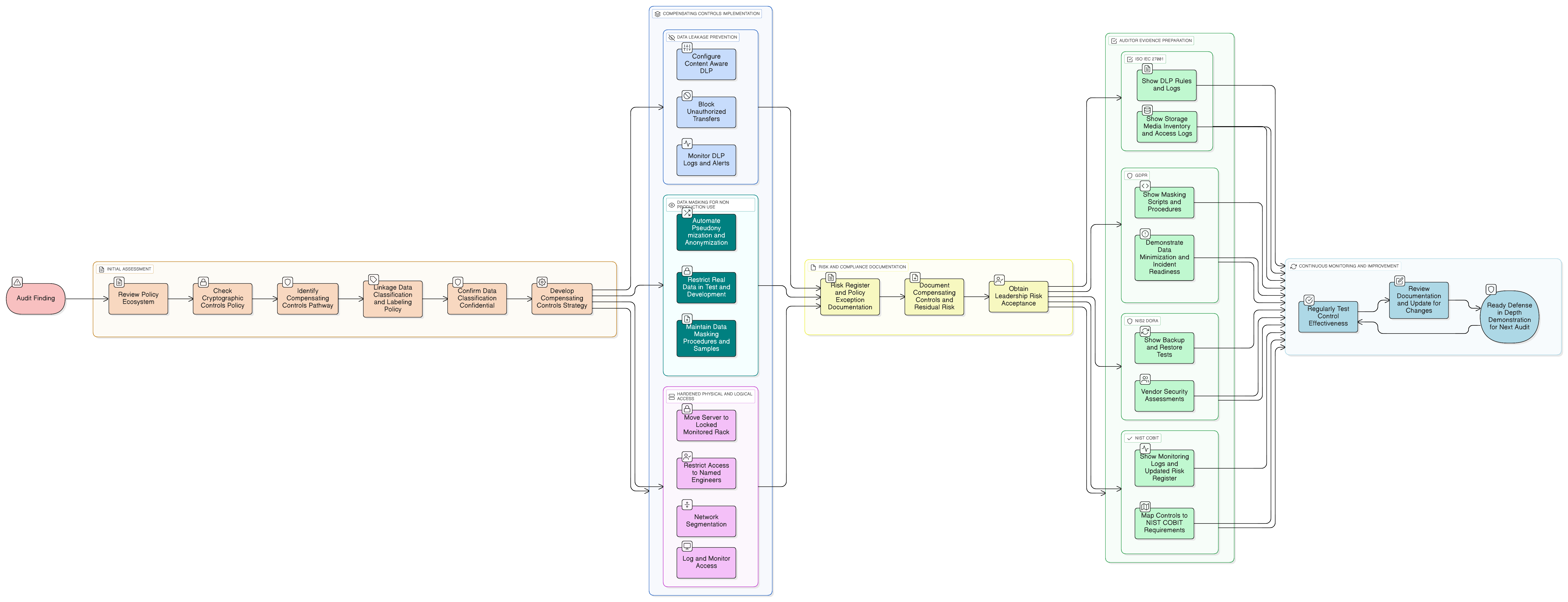
Encryption is a cornerstone of modern security, but as Clarysec’s Zenith Blueprint: An Auditor’s 30-Step Roadmap explains in Step 21, Control 8.24 Use of Cryptography is not about simply “turning encryption on.” Instead, it’s about “embedding cryptography into the organization’s design, policy, and lifecycle management.”
When one part of the design (the legacy database) fails, the policy and lifecycle aspects must compensate. Sarah’s team used this framework to architect a multi-layered defense rooted in preventing the data from ever leaving its secure, albeit unencrypted, container.
Compensating Control 1: Data Leakage Prevention (DLP)
If you can’t encrypt the data where it lives, you must ensure it cannot leave. Sarah’s team deployed a Data Leakage Prevention (DLP) solution to act as a digital guard. This wasn’t a simple network rule; it was a sophisticated, content-aware control.
Using Clarysec’s Zenith Controls: The Cross-Compliance Guide, they configured the DLP system based on the guidance for ISO/IEC 27001:2022 control 8.12 Data leakage prevention. The rules were directly informed by 5.12 Classification of information. Any data matching the schemas of the “Confidential” information in the legacy database was automatically blocked from being transferred via email, web uploads, or even copy-pasted into other applications.
As Zenith Controls explains:
“Data Leakage Prevention (DLP) depends fundamentally on accurate data classification. Control 5.12 ensures that data is labeled according to sensitivity… DLP is a specialized form of continuous monitoring, targeting data movement… 8.12 may enforce encryption policies for data leaving the organization, ensuring that even if data is exfiltrated, it remains unreadable to unauthorized parties.”
This control is recognized across multiple frameworks, mapping to GDPR Art. 32, NIS2 Art. 21, DORA Art. 10, and NIST SP 800-53 SI-4. By implementing it, Sarah’s team created a powerful protective bubble, ensuring the unencrypted data remained isolated.
Compensating Control 2: Data Masking for Non-Production Use
One of the biggest risks for legacy data is its use in other environments. The development team frequently needed data from the manufacturing system to test new application features. Simply handing them unencrypted, confidential data was out of the question.
Here, Sarah turned to Step 20 of the Zenith Blueprint, which covers 8.11 Data masking. The guide notes that auditors will pointedly ask: “Do you ever use real personal data in test systems? If so, how is it protected?”
Following this guidance, Sarah’s team implemented a strict data masking procedure. Any data extract requested by the development team had to go through an automated process that pseudonymized or anonymized sensitive fields. Customer names, proprietary formulas, and production metrics were replaced with realistic but fake data. This single control eliminated a massive surface area of risk, ensuring that the sensitive data never left its highly controlled production environment in its original form.
Compensating Control 3: Hardened Physical and Logical Controls
With data leakage and non-production use addressed, the final layer of defense focused on the system itself. Drawing on the principles of 7.10 Storage media from Zenith Controls, Sarah’s team treated the physical server as a high-security asset. While 7.10 is often associated with removable media, its principles of lifecycle management and physical security are perfectly applicable.
As Zenith Controls notes on this topic:
“ISO/IEC 27002:2022 provides comprehensive guidance under Clause 7.10 for managing storage media securely throughout its lifecycle. The standard advises organizations to maintain a register of all removable media…”
Applying this logic, the server was moved to a dedicated, locked rack in the data center, accessible only by two named senior engineers. Physical access required a sign-in and was monitored by CCTV. On the network side, the server was placed in a segmented “legacy” VLAN. Firewall rules were configured to deny all traffic by default, with a single, explicit rule allowing communication only from the designated application server on a specific port. This extreme isolation drastically reduced the attack surface, making the unencrypted data invisible and inaccessible.
Facing the Audit: Presenting a Defensible, Multi-Lens Strategy
When the auditor returned for a follow-up, Sarah didn’t present excuses. She presented a comprehensive risk treatment plan, complete with documentation, logs, and live demonstrations of her team’s compensating controls. An audit isn’t a single event; it’s a conversation viewed through different lenses, and a CISO must be prepared for each one.
The ISO/IEC 27001 Auditor Lens: The auditor wanted to see operational effectiveness. Sarah’s team demonstrated the DLP system blocking an unauthorized email, showed the data masking script running, and provided physical access logs cross-referenced with work tickets.
The GDPR and Privacy Lens: The auditor asked how data minimization was enforced. Sarah showed the automated scripts for secure deletion of cached data and the pseudonymization process for any data leaving the production system, aligning with GDPR Article 25 (Data protection by design and by default). The Cryptographic Controls Policy-sme explicitly assigns the DPO responsibility to “Ensures encryption controls align with data protection obligations under Article 32 of the GDPR.”
The NIS2/DORA Lens: This perspective focuses on operational resilience. Sarah presented backup and restore test results for the isolated system and vendor security addenda for the legacy software, demonstrating proactive risk management as required by NIS2 Article 21 and DORA Article 9.
The NIST/COBIT Lens: An auditor using these frameworks looks for governance and metrics. Sarah presented the updated risk register showing formal acceptance of the residual risk (COBIT APO13). She mapped the DLP to NIST SP 800-53 SI-4 (System Monitoring), network segmentation to SC-7 (Boundary Protection), and access controls to AC-3 and AC-4, proving that while SC-28 (Protection of Information at Rest) was not met directly, an equivalent set of controls was in place.
Key Auditor Evidence for Compensating Controls
To effectively communicate their strategy, Sarah’s team prepared evidence tailored to what auditors look for.
| Audit Lens | Evidence Required | Common Audit Test |
|---|---|---|
| ISO/IEC 27001 | Risk register entries, policy exception logs, DLP rules, storage media inventories | Review risk/exception logs, request logs of DLP actions; trace media lifecycle. |
| GDPR | Data masking procedures, breach notification readiness, data deletion records | Review sample datasets (masked vs. non-masked), test DLP triggers, simulate a breach scenario. |
| NIS2/DORA | Backup/restore testing results, vendor security assessments, incident response drills | Simulate a data export attempt; review backup handling processes; test DLP controls on critical data. |
| NIST/COBIT | Technical monitoring logs, policy integration documentation, staff interviews | Simulate data exfiltration, compare policy to procedure, interview key data custodians and system owners. |
By anticipating these different perspectives, Sarah turned a potential non-conformity into a demonstration of security maturity.
A Practical Summary for Your Next Audit
To make the strategy clear and defensible, Sarah’s team created a summary table in their risk treatment plan. It’s an approach any organization can adopt.
| Risk | Primary Control (Not Feasible) | Compensating Control Strategy | Clarysec Resource | Evidence for Auditor |
|---|---|---|---|---|
| Unauthorized disclosure of data at rest | Full Disk Encryption (AES-256) | 1. Data Leakage Prevention (DLP): Monitor and block all unauthorized data exfiltration attempts based on content and context. | Zenith Controls (8.12) | DLP policy configuration, alert logs, incident response procedures. |
| 2. Strict Logical Access Control: Isolate the server in a segmented network with “deny-all” firewall rules and highly restricted service account access. | Zenith Controls (8.3) | Network diagrams, firewall rule sets, user access reviews, service account credentials policy. | ||
| 3. Enhanced Physical Security: House the server in a dedicated, locked rack with logged and monitored physical access. | Zenith Controls (7.10) | Data center access logs, CCTV footage records, rack key sign-out sheets. | ||
| Use of sensitive data in non-production environments | Encryption of test data copies | Data Masking: Implement a formal procedure to pseudonymize or anonymize all data extracts before use in test or development. | Zenith Blueprint (Step 20) | Formal Data Masking Procedure document, demonstration of masking scripts, sample masked dataset. |
Cross-Compliance at a Glance
A strong compensating control strategy is defensible across all major frameworks. Clarysec’s Zenith Controls provides the crosswalk mapping to ensure your defenses are universally understood and accepted.
| Framework | Key Clause/Reference | How Compensating Controls Are Recognized |
|---|---|---|
| ISO/IEC 27001:2022 | 8.24, 7.10, 8.12, 8.11, 5.12 | Risk-based approach allows for alternative controls like DLP, storage media management, and data masking when justified. |
| GDPR | Art. 5(1)(f), 25, 32 | Requires “appropriate” technical measures; pseudonymization, access controls, and DLP can fulfill this if encryption is not feasible. |
| NIS2 | Art. 21, 23 | Mandates a risk-based approach; layered controls like DLP, backup protection, and vendor checks are valid risk treatments. |
| DORA | Art. 5, 9, 10, 28 | Emphasizes operational resilience; DLP, access control, and robust logging are key to protecting financial data, with or without encryption. |
| NIST SP 800-53 | SC-28, MP-2 to MP-7, AC-3/4, SI-4 | Allows for compensating controls; DLP (SI-4), access restrictions (AC-3), and media tracking (MP series) can address the risks of unencrypted data. |
| COBIT | DSS05, APO13, MEA03 | Focuses on governance and measurement; documented risk acceptance (APO13) and monitoring of compensating controls (MEA03) demonstrate due diligence. |
Conclusion: Turn Your Weakest Link into a Strength
The story of the un-encryptable legacy database is not a story of failure. It’s a story of mature, intelligent risk management. By refusing to accept a simple “can’t be done” answer, Sarah’s team transformed a significant vulnerability into a showcase of their defense-in-depth capabilities. They proved that security is not about ticking a single box labeled “encryption.” It’s about understanding the risk and building a thoughtful, layered, and auditable defense to mitigate it.
Your organization will inevitably have its own version of this legacy database. When you find it, don’t see it as a roadblock. See it as an opportunity to build a more resilient and defensible security program.
Ready to build your own bulletproof, audit-ready control framework? Start with the right foundation.
- Review your policy ecosystem with Clarysec’s comprehensive policy toolkits.
- Explore The Zenith Blueprint: An Auditor’s 30-Step Roadmap to guide your implementation.
- Leverage Zenith Controls: The Cross-Compliance Guide to ensure your defenses stand up to scrutiny from any angle.
Get in touch with Clarysec for a tailored workshop or a full cross-compliance assessment. Because in today’s regulatory landscape, preparedness is the only control that matters.
References:
- Cryptographic Controls Policy
- Cryptographic Controls Policy-sme
- Data Classification and Labeling Policy
- Zenith Blueprint: An Auditor’s 30-Step Roadmap
- Zenith Controls: The Cross-Compliance Guide
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council