Beyond the Signature: Why Executive Commitment Is the Ultimate Security Control
The Phantom Executive and the Inevitable Audit Failure
Imagine a scenario that plays out in boardrooms more often than we care to admit.
Alex, a newly hired CISO, walks into a quarterly board meeting. He has prepared a forty-page slide deck detailing vulnerability patches, firewall uptime, and the latest phishing simulation results. The CEO, distracted by a merger discussion, glances at the screen, nods, and says, “Looks like IT has this handled. Keep us safe, Alex.” The meeting moves on to sales figures.
Six months later, the organization faces a ransomware attack. Recovery is slow because business continuity plans were never tested by business units. Regulatory fines loom large. When the external auditor arrives to assess their ISO/IEC 27001:2022 compliance, the first question is not about the firewall. It is: “Can I speak to the CEO about their role in the Information Security Management System (ISMS)?”
The CEO is baffled. “I hired Alex for that.”
The audit fails. Not because of technology, but because of a fundamental misunderstanding of Clause 5.1: Leadership and Commitment.
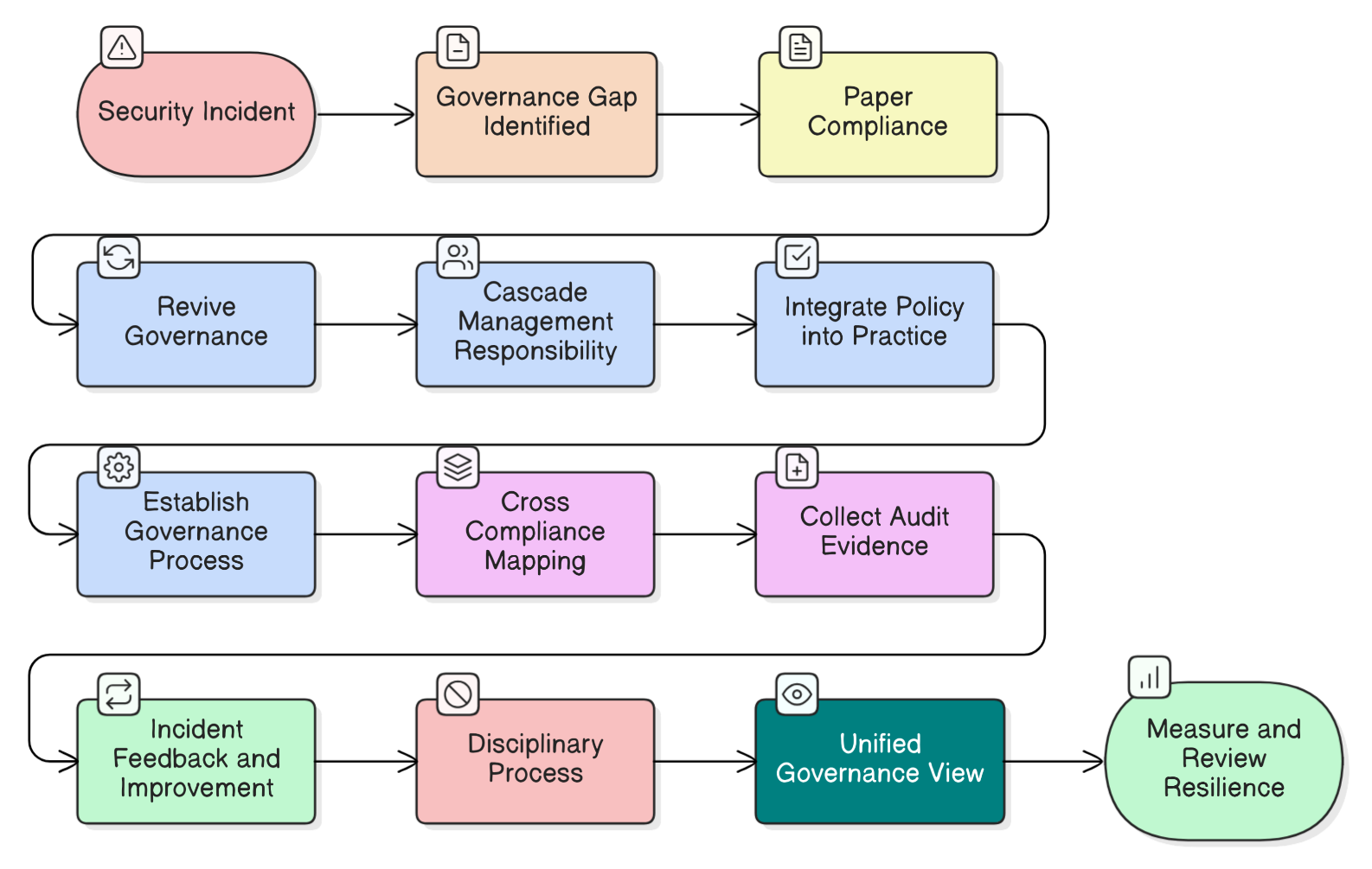
In the modern compliance landscape, the “Phantom Executive”-the leader who signs the checks but ignores the strategy-is the single biggest risk to an organization’s security posture. At Clarysec, we see this disconnect constantly. Security is often siloed as a technical problem rather than embraced as a business imperative. This article guides you through bridging that gap, using the Zenith Blueprint, our Zenith Controls analysis, and real-world policy examples to transform leadership from a passive audience into the driving force of your ISMS.
Beyond the Signature: What Real Security Leadership Looks Like
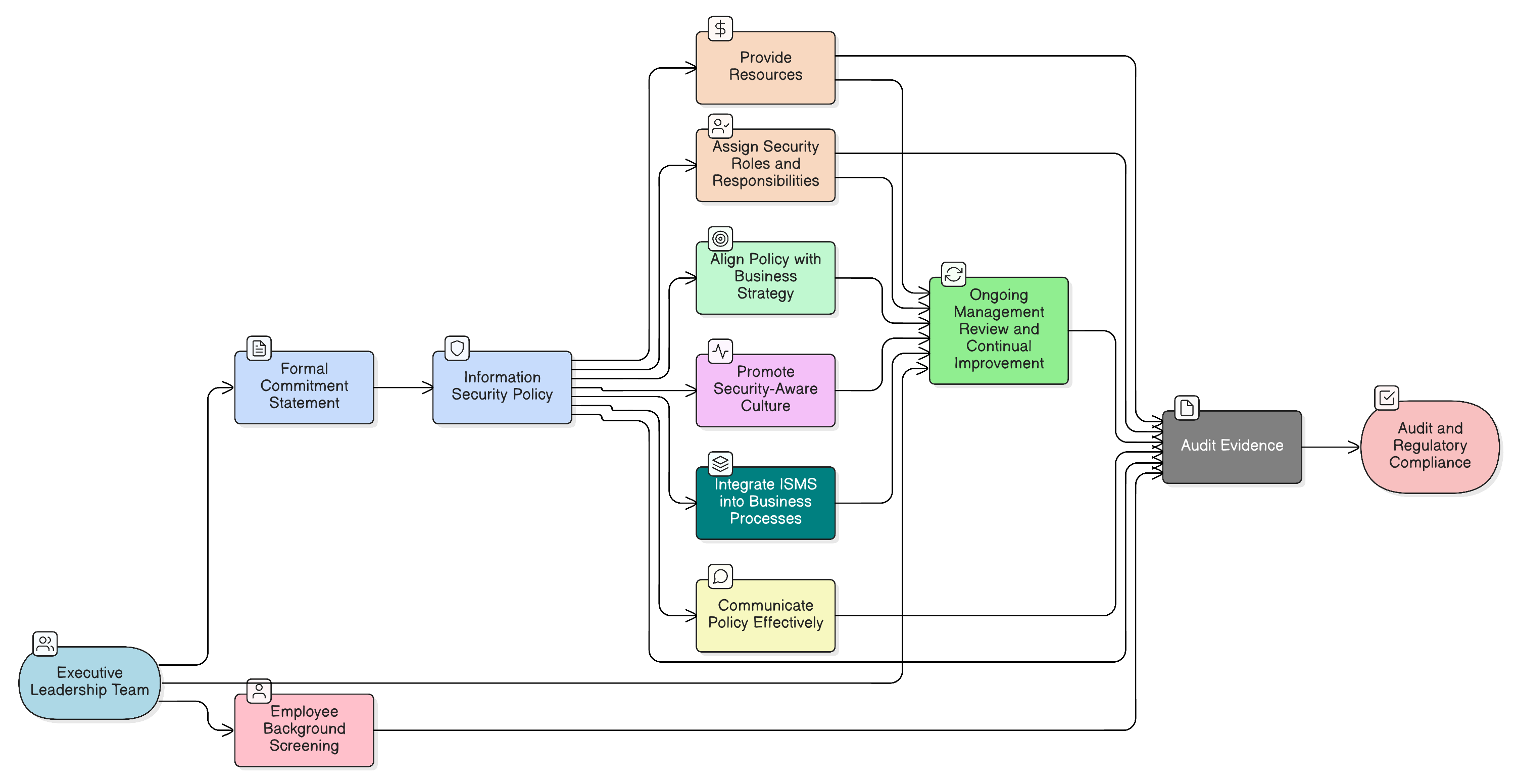
It is easy to mistake a policy signature for genuine commitment. But robust leadership, as demanded by ISO/IEC 27001:2022 Clause 5.1, means executives and board members actively approve, champion, and resource the ISMS-then own its ongoing effectiveness. The standard is explicit: top management cannot delegate accountability.
Clarysec’s experience shows that robust executive leadership isn’t just an ISO checkbox. It is the engine driving security culture, effectiveness, and audit-readiness. True commitment is demonstrated by:
- Endorsing the ISMS: Ensuring the information security policy aligns with the organization’s strategic direction.
- Providing Resources: If a risk assessment demands a new tool, specialized training, or more personnel, leadership must fund it.
- Promoting Awareness: When the CEO mentions security in a town hall, it carries more weight than a hundred emails from the IT department.
- Integrating ISMS into Business Processes: Security reviews must be a standard part of project management, supplier onboarding, and product development, not an afterthought.
As detailed in our Zenith Blueprint, an auditor’s 30-step roadmap, demonstrating leadership starts with a formal commitment statement but must be backed by continuous, visible action.
Policy as the Voice of Leadership
The primary vehicle for top management to express their intent is the Information Security Policy. This document is not a technical manual; it is a governance directive that sets the tone for the entire organization.
In our Information Security Policy for enterprises, we state this directly:
“The policy fulfills ISO/IEC 27001:2022 Clause 5.2 and Clause 5.1 by expressing leadership intent, top management commitment, and alignment of security activities with organizational objectives.” (Section ‘Purpose’, policy clause 1.3)
For smaller organizations, the approach is more direct but carries the same weight. Our Information Security Policy SME emphasizes clear ownership:
“Assign Clear Responsibility: Ensure that someone is always accountable for information security. Typically, this is the General Manager or the person they formally assign.” (Section ‘Objectives’, policy clause 3.1)
A common audit pitfall is the difference between policy availability and policy communication. A policy that exists but is unknown is useless. ISO/IEC 27001:2022 Clause 7.3 and Control 6.3 require that the policy is communicated effectively. If an auditor asks a random employee about the company’s security stance and receives a blank stare, it’s a clear failure of Clause 5.1.
Operationalizing Commitment: A Practical Toolkit
Transforming abstract commitment into auditable action requires a structured approach. Here is how Clarysec’s toolkit operationalizes leadership obligations.
1. The Formal Commitment Statement
A public declaration solidifies intent and clarifies expectations. The Zenith Blueprint recommends embedding this directly into your information security policy:
“The CEO and executive team of [ Org Name ] are fully committed to information security. We consider information security a core part of our business strategy and operations. Management will ensure sufficient resources and support are provided to implement and continually improve the Information Security Management System in line with ISO/IEC 27001 requirements.”
This is not cosmetic. Auditors will interview top management to confirm they understand and endorse this statement, asking pointed questions about resource allocation and strategic alignment.
2. Clear Roles, Responsibilities, and Authorities (Clause 5.3)
Commitment becomes tangible when assigned to people. Leadership must designate accountable owners for every element of the ISMS. A RACI (Responsible, Accountable, Consulted, Informed) matrix is invaluable evidence. While a CISO may be Responsible for executing the strategy, top management remains Accountable for the risk.
Our Governance Roles & Responsibilities Policy SME formalizes this architecture:
“This policy defines how governance responsibilities for information security are assigned, delegated, and managed in the organization to ensure full compliance with ISO/IEC 27001:2022 and other regulatory obligations.” (Section ‘Purpose’, policy clause 1.1)
3. Resource Allocation: Money, People, and Tools
An ISMS without resources is just a paper exercise. Top management must demonstrate commitment by allocating a tangible budget for security initiatives identified through risk assessments, whether for new technology, facility upgrades, or specialized training. As the Zenith Blueprint notes, if the risk assessment shows a need, leadership is expected to fund it.
4. Ongoing Review and Continual Improvement (Clause 9.3)
Leadership’s commitment is an ongoing obligation, not a one-time event. Management must participate in formal ISMS review meetings (at least annually) to assess performance against objectives, evaluate new risks, approve significant changes, and direct improvements. Meeting minutes, performance dashboards, and documented improvement plans are critical artifacts for any audit.
5. Fostering a Security-Aware Culture
Visible leadership behavior is the most powerful tool for building culture. When executives adhere to policies and speak about the importance of security, it signals that security is everyone’s responsibility. This is explicitly required in our Information Security Policy, which states that leadership “leads by example and promotes a strong information security culture.” This expectation extends to mid-level managers, who are tasked with enforcing policies within their teams and integrating security into daily operations.
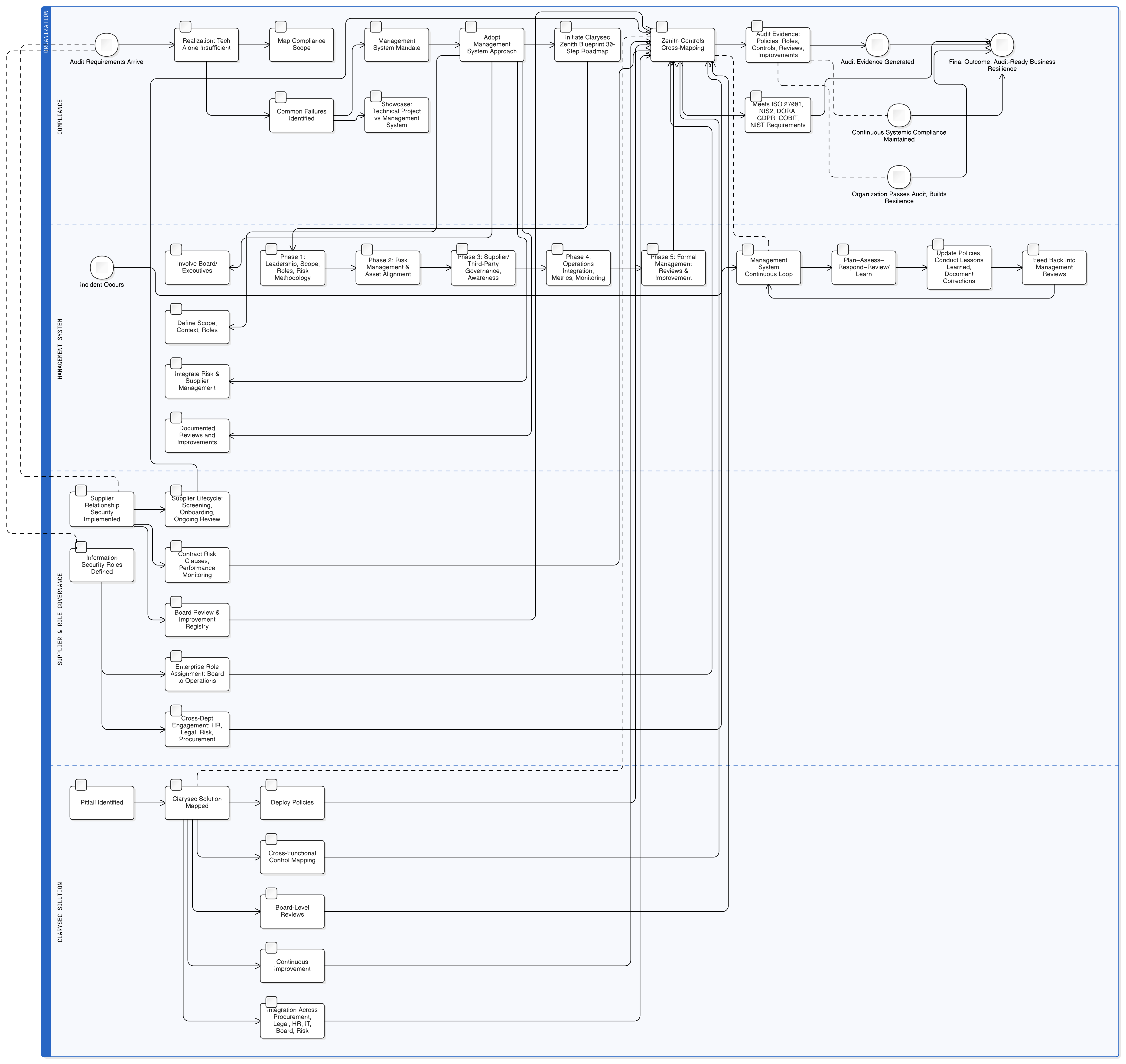
The Cross-Compliance Ecosystem: One Commitment, Many Mandates
Executive leadership is not just an ISO requirement; it is the universal backbone for all major security, privacy, and resilience frameworks. A strong demonstration of commitment for ISO 27001 simultaneously satisfies core governance requirements for NIS2, DORA, GDPR, NIST, and COBIT.
Our Zenith Controls analysis provides the critical crosswalk, showing how a single action maps to multiple compliance obligations.
| Framework | Leadership Commitment Requirement | Key Evidence and Artifacts |
|---|---|---|
| ISO/IEC 27001:2022 | Clause 5.1: Leadership and commitment | Approved policy, management review minutes, resource allocation records. |
| EU NIS2 | Art. 21: Management body oversight and approval of cybersecurity measures | Documented framework, management sign-off, training records for management. |
| EU DORA | Arts. 5, 6: ICT Governance framework approved and overseen by the management body | Approved ICT policies, defined roles and responsibilities, risk management framework. |
| EU GDPR | Arts. 5(2), 24, 32: Accountability principle, implementation of appropriate measures | Data protection policies, records of processing activities, evidence of regular review. |
| NIST SP 800-53 Rev. 5 | PL-1, PM-1: Security planning policies, organization-wide program management | Formal security plan, policy dissemination records, leadership interviews. |
| COBIT 2019 | EDM01.02: Ensure governance system maintenance | Governance framework documentation, board meeting minutes, performance reports. |
Under NIS2, national authorities can hold top management personally liable for failures. Similarly, DORA mandates that the management body defines, approves, and oversees the ICT risk management framework. As our Zenith Controls analysis highlights:
“NIS2 requires… documented cybersecurity risk management framework, including governance-level security policies… ISO 27001 Control 5.1 directly fulfills this by mandating a policy that defines security objectives, management commitment, and assignment of responsibilities.”
Implementing ISO 27001 is not just a commercial differentiator; it is a defensive strategy against regulatory actions targeting leadership.
The Human Factor: Screening as a Leadership Decision
What does employee background screening have to do with the C-suite? Everything.
Top management sets the organization’s risk appetite. ISO 27001:2022 Control 6.1: Screening is a direct operational manifestation of this risk decision, determining the level of trust required for individuals to access company assets.
As analyzed in Zenith Controls:
“NIS2 explicitly requires… human resources security measures, including vetting personnel in security-sensitive positions. Control 6.1 directly addresses this requirement by mandating background checks for employees…Through screening, organizations reduce the risk of insider threats, ensuring that only trusted individuals have access.”
This single control is deeply interconnected. It influences terms of employment (Control 6.2), supplier relationships (Control 5.19), and privacy obligations (Control 5.34). When leadership pushes HR to skip background checks to “hire faster,” they are actively undermining the ISMS by prioritizing speed over stated security objectives-a clear violation of Clause 5.1.
The Auditor’s Lens: Preparing for the Interrogation
Auditors will not just read your documents; they will interview your executives. This is where a lack of genuine commitment becomes painfully obvious. A well-prepared CISO ensures their leadership can confidently answer the tough questions.
Here is what auditors, guided by standards like ISO 19011 and ISO 27007, will demand.
| Audit Focus Area | Evidence and Artifacts Required | Typical Auditor Interview Questions for Leadership |
|---|---|---|
| Policy Approval | Signed and dated policy document; board meeting minutes showing discussion and approval. | “When was this policy last reviewed by the executive team? Why is it important to our business goals?” |
| Resource Allocation | Approved budgets for security tools, training, and personnel; purchase records. | “Can you provide an example of a security improvement you personally championed and funded last year?” |
| Management Review | Scheduled review meetings; attendance lists; minutes with action items and decisions. | “How does management stay informed about the performance of the ISMS? What were the key outcomes of your last review?” |
| Role Assignment | Organizational chart; RACI matrix; formal job descriptions with security duties. | “Who is ultimately accountable for information security risk in this organization? How is that communicated?” |
| Communication | Internal announcements; intranet pages; records of all-hands meetings or training sessions. | “How do you ensure every employee, from the front desk to the data center, understands their security responsibilities?” |
A CEO who can articulate how security enables business strategy-by protecting client trust, ensuring service availability, or enabling market access-passes with flying colors. A CEO who says, “It prevents viruses,” signals a critical failure in leadership.
Conclusion: Leadership is the Ultimate Control
In the complex machinery of an ISMS, firewalls can fail and software can have bugs. But the one control that cannot afford to fail is Leadership. Top management commitment is the energy source for the entire system. Without it, policies are just paper, and controls are merely suggestions.
By following the Zenith Blueprint and leveraging the cross-compliance intelligence of the Zenith Controls analysis, you can document, demonstrate, and operationalize this commitment. Security is not something you buy; it is something you do. And that doing starts at the very top.
Ready to transform your leadership team from a compliance risk into your greatest security asset? Contact Clarysec today for a guided workshop or to explore how our Zenith suite can streamline your path to genuine, audit-proof security governance.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council