From Tarmac to Tabletop: Architecting a NIS2-Compliant Incident Response Plan for Critical Infrastructure
The Crisis Scenario: Where Preparedness Meets Real Consequence
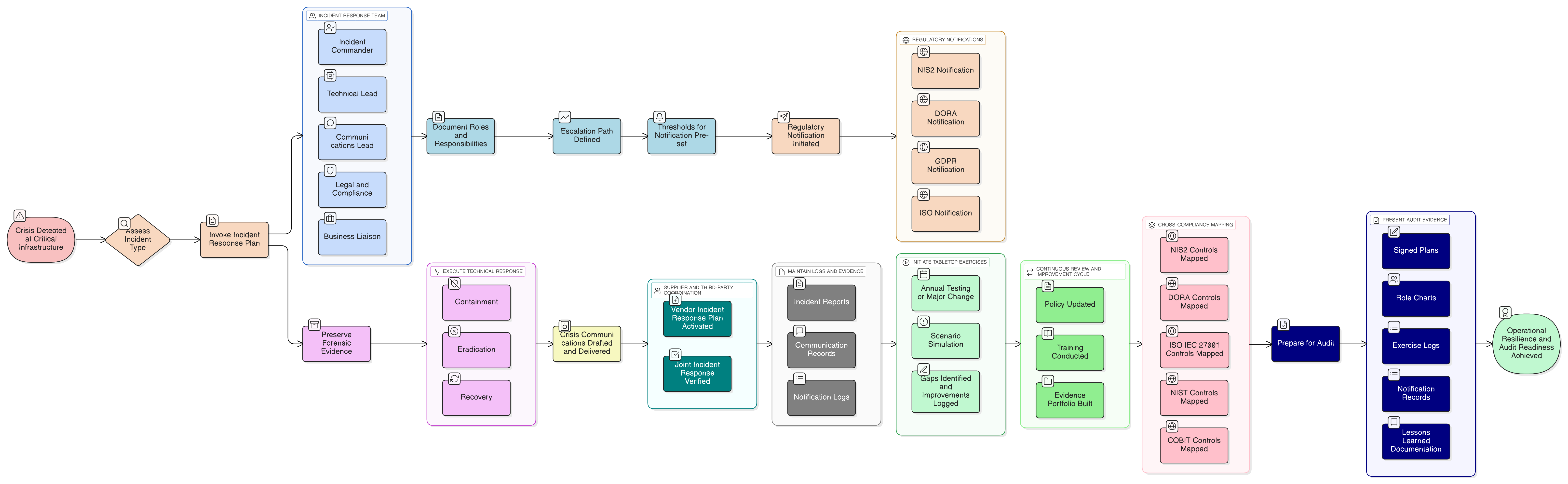
It’s 3:17 AM in the Security Operations Center of a major regional airport. The baggage handling system, vital for thousands of passengers, is locked by an unresponsive control interface. Network traffic spikes in anomalous ways. Is it a momentary IT glitch, a hardware failure, or the prelude to a deep, coordinated cyberattack? Within hours, transatlantic flights will board. Every minute of confusion or slow response will ripple into operational chaos, reputational damage, regulatory scrutiny, and potentially millions in losses.
For leaders charged with managing critical infrastructure, airports, energy grids, water utilities, hospitals, such moments are neither rare nor benign. Today’s regulatory landscape, anchored by the NIS2 Directive, Digital Operational Resilience Act (DORA), and international standards like ISO/IEC 27001:2022, demands not just a plan, but living proof of readiness. The stakes are existential. Incident response must be more than technical, it must be demonstrably compliant, meticulously documented, and cross-mapped for every regulatory lens.
This is the high-pressure world that Clarysec’s Zenith Controls and Zenith Blueprint are made for, a world where a “plan on paper” is not enough, and every decision, communication, and recovery step must withstand legal, regulatory, and operational scrutiny.
The NIS2 Mandate: Incident Response is a Legal Obligation
The arrival of NIS2 resets expectations. Regulators demand structured, repeatable, and auditable incident handling. Article 21(2) requires “policies and procedures concerning incident handling” as legal instruments. This goes beyond a security best practice; it’s a duty that can be directly assessed, and penalized, if absent or ineffective.
Key NIS2 incident response requirements:
- Documented incident management processes
- Complete evidence of threat handling: identification, containment, eradication, recovery
- Defined and mapped roles, including external supplier responsibilities
- Mandatory testing, including tabletop exercises and effectiveness reviews
- Cross-framework compliance with DORA, NIST, COBIT, GDPR, and ISO/IEC 27001:2022
If your plan cannot answer critical questions instantly, who leads, who communicates, who reports, and how the response is tracked, tested, and improved, it is simply not compliant.
Laying the Foundation: Planning and Operationalizing Your Response
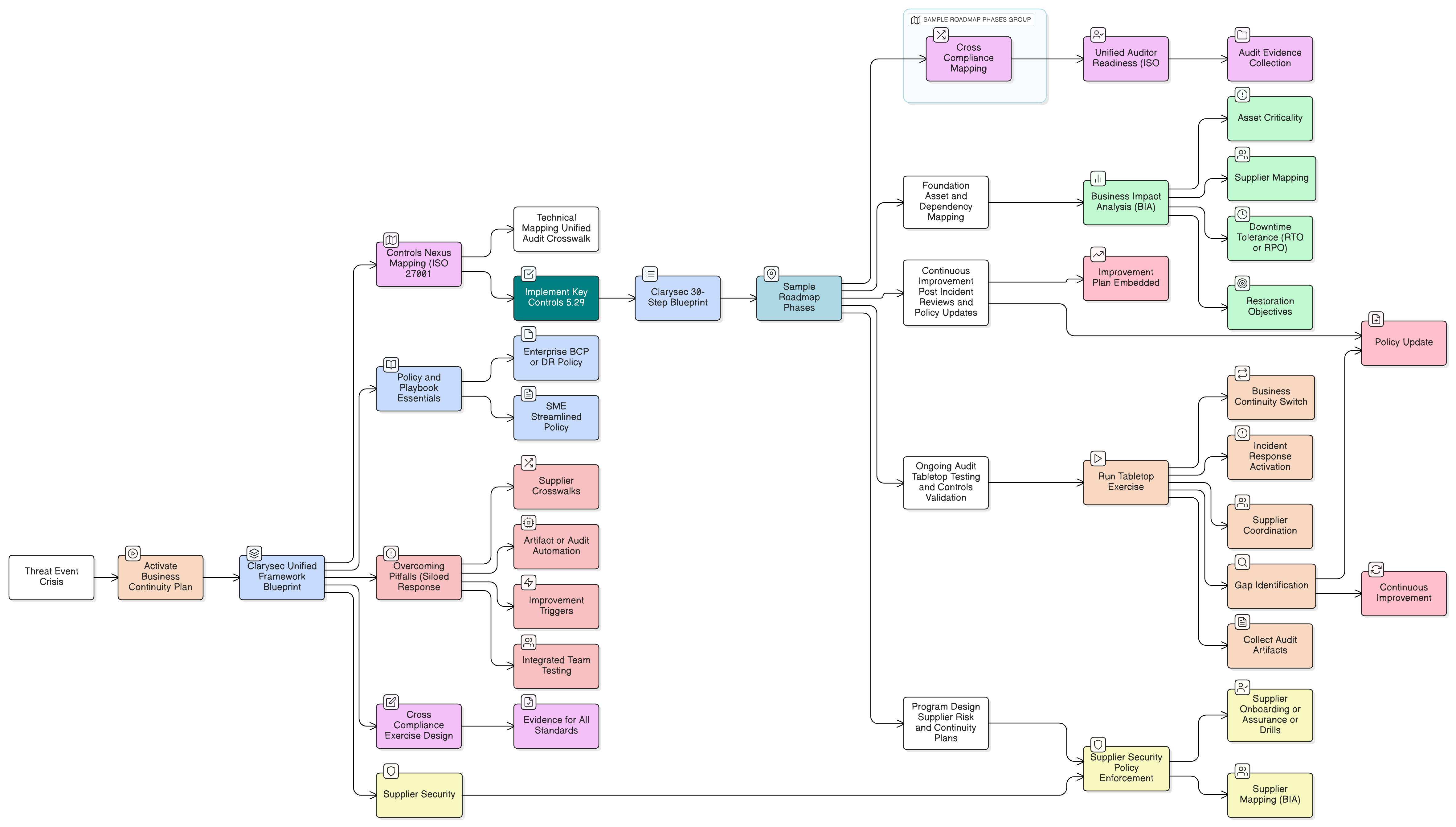
A robust incident response starts with the right blueprint. ISO/IEC 27002:2022 Control 5.26, supported by Clarysec’s Zenith Blueprint: An Auditor’s 30-Step Roadmap and Zenith Controls, demands that preparation be detailed, operationalized, and owned.
Clarysec’s Zenith Blueprint, especially Phase 4 and 5, mandates:
“Implement incident management procedures: define roles, responsibilities, and communication channels so every stakeholder, from SOC analyst to CEO, knows their part. Document and validate capabilities through comprehensive tabletop exercises.”
This means:
- Documenting authority and escalation paths
- Pre-defining thresholds for regulatory notification
- Mapping who drafts and delivers crisis communications
- Ensuring forensic evidence is preserved without impeding recovery
- Testing and iterating plans via structured exercises
Preparation is not a one-time event. It is a cycle, plan, test, review, improve. The Zenith Blueprint provides detailed steps to ensure all these points are covered, evidenced, and ready for audit.
Architecting the Incident Response Team: Roles, Responsibilities, and Capability
Responding well, at 3:17 AM or anytime, depends on clarity of roles. Clarysec’s Incident Management Policy and ISO/IEC 27035-1:2023 define best-practice teams and charters:
| Role | Primary Responsibility | Key Skills & Authority |
|---|---|---|
| Incident Commander | Overall coordination, decision authority, executive communication | Decisive leadership, crisis management, authority over major changes |
| Technical Lead | Investigation, forensics, containment, remediation | Network forensics, malware analysis, infrastructure expertise |
| Communications Lead | Internal/external messaging, regulator/public liaison | Crisis comms, legal knowledge, clarity in business impact |
| Legal & Compliance | Legal, contractual, regulatory guidance | Data protection law, cyber law, NIS2/DORA/GDPR expertise |
| Business Liaison | Ensuring operational priorities remain central | Business process knowledge, risk management |
Documenting these roles, and aligning them with both primary and secondary personnel, prevents the most common crisis failure: confusion and miscommunication.
The Incident Lifecycle: Controls Must Work Together
A mature incident response plan weaves together multiple controls and standards, never seen in isolation. Clarysec’s Zenith Controls shows how 5.26 (planning and preparation) links directly with other incident management controls:
- Preparation and Planning (5.26): Define IRT, create playbooks, draft communication plans, simulate scenarios.
- Event Assessment (5.25): Decide if an incident is real, based on preset criteria, ensuring decisive action, not analysis paralysis.
- Technical Response (5.27): Carry out containment, eradication, and recovery, guided by detailed playbooks and mapped responsibilities.
This lifecycle isn’t just theoretical, it is the backbone of a response capable of satisfying both operational need and regulatory scrutiny.
Tabletop Testing: The Final Exam Before Disaster
The “tabletop” exercise transforms planning into proven readiness. Clarysec’s policies require:
“The incident response plan shall be tested at least annually or upon major changes to infrastructure. Scenarios should reflect realistic threats: ransomware, denial-of-service, supply chain breach, or data leak.”
A tabletop example for our airport:
Facilitator: “It is 3:17 AM. The baggage system is unresponsive. A ransom note appears on a shared admin drive. What next?”
The IRT:
- Incident Commander convenes the team.
- Technical Lead initiates network segmentation.
- Legal/Compliance tracks the 24-hour NIS2 notification deadline.
- Communications Lead drafts statements for partners and media, balancing clarity and caution.
- Contact lists are tested, outdated supplier info triggers an immediate improvement loop.
Outcomes are documented, gaps identified, and policies updated. Every test iteration, every log, and every change is real, auditable evidence.
Evidence Generation and Audit Readiness: Your Proof Is Your Plan
Passing an audit means showing more than just a policy, auditors want operating evidence.
Example Evidence Table:
| Requirement | Clarysec Resource | How Evidence Is Generated |
|---|---|---|
| IR Plan Exists | Zenith Controls, 30-Step Blueprint | Signed, accessible, versioned plan |
| Roles & Responsibilities | IR Policy, Supplier Policy | Organization charts, role matrices, contract inclusions |
| Tabletop Exercise Log | Zenith Controls, Blueprint Step | Timestamped exercise reports, minutes, lessons-learned |
| Notification Records | Communication templates, Blueprint | Email trails, regulator forms, response logs |
| Improvement Cycle Proof | Post-mortem, Blueprint Steps | Updated plans, training logs, evidence of continuous update |
Cross-Compliance Mapping: NIS2, DORA, NIST, COBIT, ISO/IEC 27001:2022
Clarysec’s Zenith Controls uniquely maps major standards for unified assurance. Incident response controls sit at the intersection:
| Control Number | Control Name | Description | Supporting Standards | Mapped Frameworks |
|---|---|---|---|---|
| 5.24 | Incident Management Controls | Detection, reporting, evidence logging, review | ISO/IEC 27035:2023, ISO/IEC 22301:2019, ISO/IEC 27031:2021 | NIS2, DORA, NIST SP 800-61, COBIT |
| 5.25 | Incident Response Plan | Response team design, notification paths, regular testing/improvement | ISO/IEC 22301:2019, ISO/IEC 27031:2021, ISO/IEC 27035:2023 | NIS2, DORA, NIST, COBIT, GDPR |
| 5.26 | Planning & Preparation | IRT definition, playbooks, communication plans, scenario mapping | ISO/IEC 27001:2022, ISO/IEC 27035:2023, ISO/IEC 22301:2019 | NIS2, DORA, NIST, COBIT |
| 5.27 | Technical Response | Containment, eradication, recovery playbooks, operational logs | ISO/IEC 27001:2022, ISO/IEC 27031:2021 | NIS2, DORA, NIST, COBIT |
Supporting standards reinforce resilience:
- ISO/IEC 22301:2019: Business continuity, triggers alignment between incident handling and disaster recovery.
- ISO/IEC 27035:2023: Incident lifecycle, vital for lessons-learned and audit review.
- ISO/IEC 27031:2021: ICT readiness for technical incident containment and recovery.
Framework Guidance
- DORA: Demands rapid regulatory notification and integration with business continuity and technical plans.
- NIST CSF: Direct alignment with “Respond” function, emphasizing immediate, documented action.
- COBIT 2019: Focus on governance, integrating incident response with enterprise risk and performance metrics.
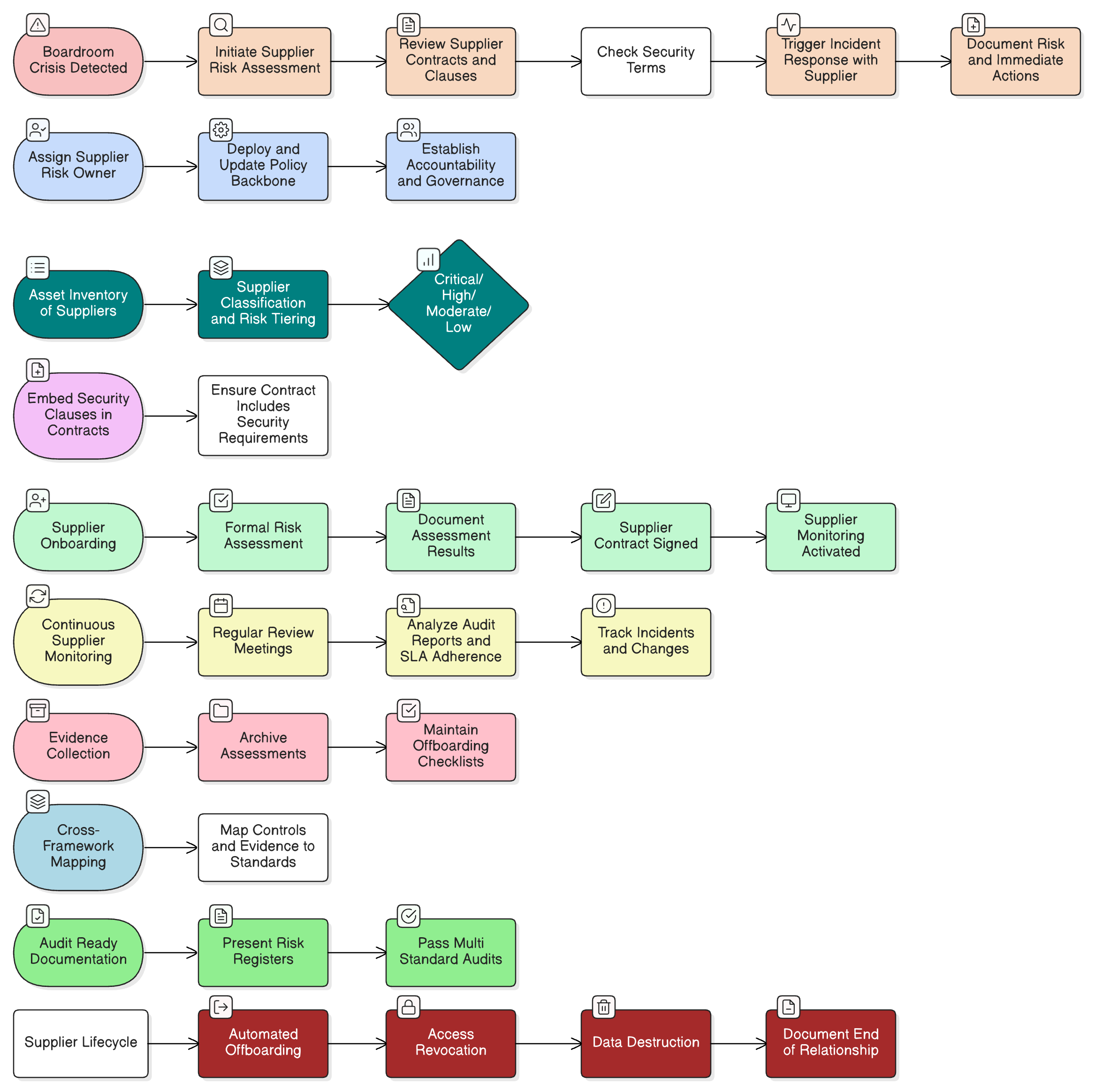
Supplier & Third-Party Integration: Securing the Extended Perimeter
Critical infrastructure is only as strong as its weakest vendor or partner. Clarysec’s Third-party and Supplier Security Policy sets clear obligations.
Key requirements include:
“Suppliers must develop, maintain, and test their own incident response plans matching our standards. Responsibilities, channels, and exercise evidence must be documented.” (Section 9)
This is not optional. Contracts must specify IR integration, third-party notifications, and audit trails. The SME-focused variant adapts these for smaller suppliers, so compliance spans your entire ecosystem.
Supplier Tabletop Example:
- Outage traced to external baggage system vendor.
- Vendor’s IR plan activated, coordinated according to joint exercise protocols.
- Failures, such as outdated contact information, are documented, triggering corrective action before real disaster strikes.
Auditor Perspectives: Surviving Multi-Framework Scrutiny
Auditors use different lenses. Clarysec’s Zenith Controls prepares organizations for each perspective:
ISO/IEC 27001:2022 auditors:
- Demand documented, tested incident response plans.
- Audit for role clarity, evidence of tabletop tests, and integration with business continuity.
NIS2/DORA Auditors:
- Require scenario-based results.
- Check timing and sequence of regulatory notifications.
- Look for seamless supplier integration and improvement cycles.
NIST/COBIT Auditors:
- Scrutinize operation of incident lifecycle controls.
- Seek evidence of risk integration, process improvement, and lessons-learned documentation.
Critical Challenges and Clarysec’s Countermeasures
Common pitfalls, addressed directly by Clarysec’s tools:
- Role confusion or communication gaps: Zenith Blueprint’s role matrices, mapped to notifications and actions.
- Supplier IR incompleteness: Mandatory audits, contract requirements, and joint exercises per Third-party policy.
- Evidence gaps: Automated logs, post-mortem templates, improvement tracking in policy and practice.
How to Build, Test, and Evidence Your Incident Response
A Five-Point Checklist for NIS2 Audit-Readiness
- Assess and Map Your Current IR Plan: Use Zenith Blueprint’s 30 steps for comprehensive gap analysis.
- Implement Zenith Controls and Crosswalks: Ensure mapping to ISO/IEC 27001:2022 controls, DORA, NIS2, NIST, and COBIT. Address supplier contracts and supporting standards.
- Conduct Realistic Tabletop Exercises: Document evidence (logs, communications, supplier coordination, improvement actions).
- Enforce Third-Party Policy: Apply Clarysec’s Third-party and Supplier Security Policy and SME variant, ensuring all vendors are compliant.
- Prepare Evidence Portfolio: Include signed plans, role charts, exercise logs, notification reports, and documented lessons-learned.
Your Path: From Tarmac to Tabletop, From Anxiety to Assurance
In today’s regulated, interconnected world, an incident response plan must not only exist but be proven in practice through evidence, cross-compliance, and real readiness. Clarysec’s integrated toolkit, Zenith Blueprint, Zenith Controls, and robust policies, provides the architecture for true operational resilience.
Every step is mapped, tested, and audit-ready, so whether the crisis starts at 3:17 AM or in the boardroom, your organization excels. Building a battle-ready, NIS2-compliant incident response capability means more than peace of mind, it is regulatory defense and operational excellence in one.
Next Steps: Secure Your Assurance with Clarysec
The journey from tarmac to tabletop begins now:
- Download Clarysec’s Zenith Blueprint and Zenith Controls.
- Schedule your tabletop simulation with our team.
- Review and upgrade your Third-party and Supplier Security Policy, covering every partner, big or small.
Do not wait for the next 3 AM alert to discover the gaps in your plan. Contact Clarysec to arm your organization with proven, tested, and evidenced incident response.
Clarysec: Your Partner in Compliance, Resilience, and Real-World Incident Response.
Zenith Controls | Zenith Blueprint | Third-party and supplier security policy | Incident Management Policy
Explore more case studies and toolkits at the Clarysec blog. Schedule a tailored workshop or audit-readiness assessment today.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council