Beyond Recovery: A CISO's Guide to Building True Operational Resilience with ISO 27001:2022
Maria, CISO at a growing fintech firm, is presenting Q3 risk metrics to the board. Her slides are crisp, showing declining vulnerability counts and successful phishing simulations. Suddenly, her phone buzzes insistently. A priority alert from the SOC lead: “Ransomware detected. Spreading laterally. Core banking services impacted.”
The room’s atmosphere shifts from confident to tense. The CEO asks the inevitable question: “How quickly can we restore from backup?”
Maria knows they have backups. They test them quarterly. But as her team scrambles to failover, a dozen other questions flood her mind. Are the recovery environments secure, or are they just re-infecting restored systems? Is our incident logging still functional on the backup site, or are we flying blind? Who has emergency admin access, and are their actions being tracked? In the rush to get services back online, is someone about to email sensitive customer data from a personal account?
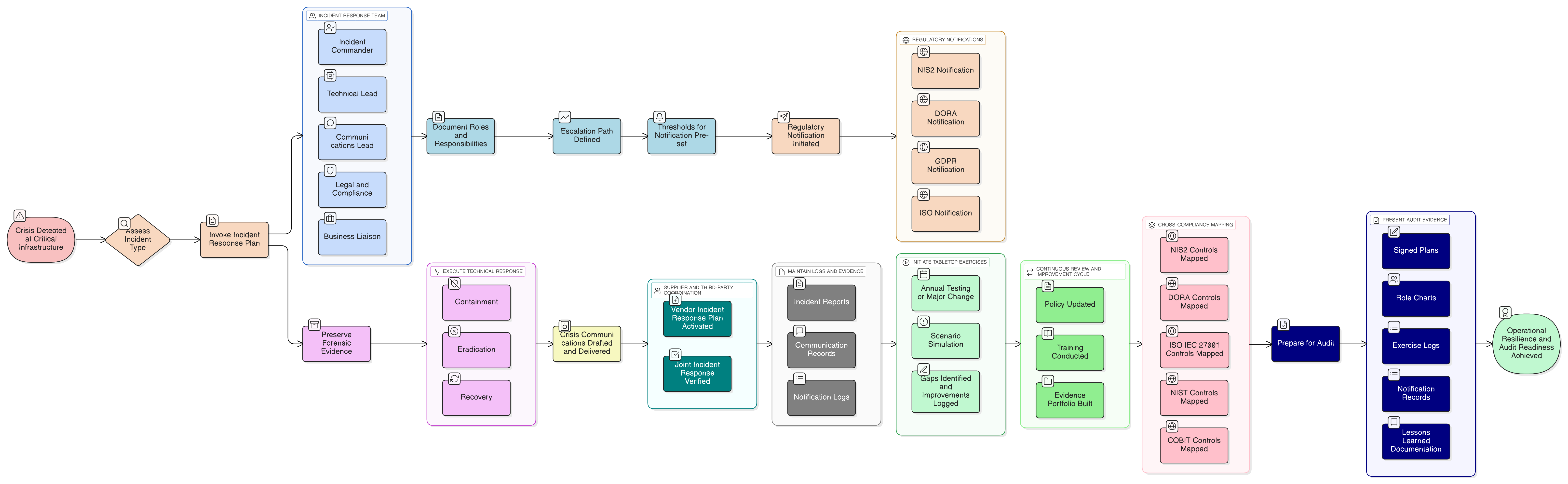
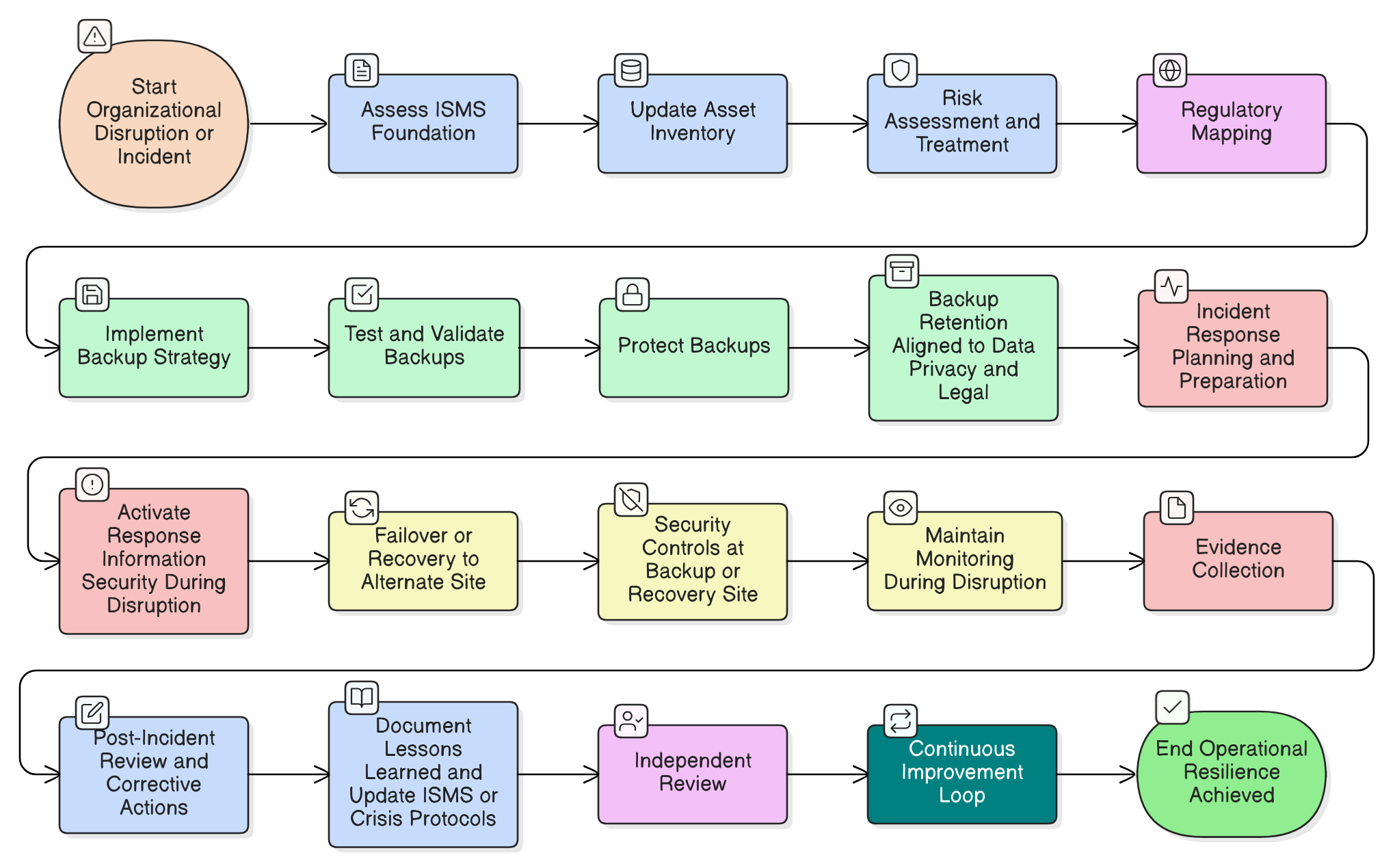
This is the critical moment where a traditional disaster recovery plan fails and true operational resilience is tested. It’s not just about bouncing back; it’s about bouncing back with integrity. This is the fundamental shift in mindset demanded by ISO/IEC 27001:2022, a shift from mere recovery to maintaining a holistic, unbroken security posture, even in the heart of chaos.
The Modern Definition of Resilience: Security Never Pauses
For years, business continuity planning focused heavily on Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs). While essential, these metrics only tell part of the story. They measure speed and data loss, but they don’t measure security posture during the crisis itself.
ISO/IEC 27001:2022, particularly through its Annex A controls, elevates the conversation. It recognizes that a disruption is not a pause button for information security. In fact, the chaos of a crisis is precisely when security controls are most vital. Attackers thrive on confusion, exploiting the very workarounds and emergency procedures designed to restore service.
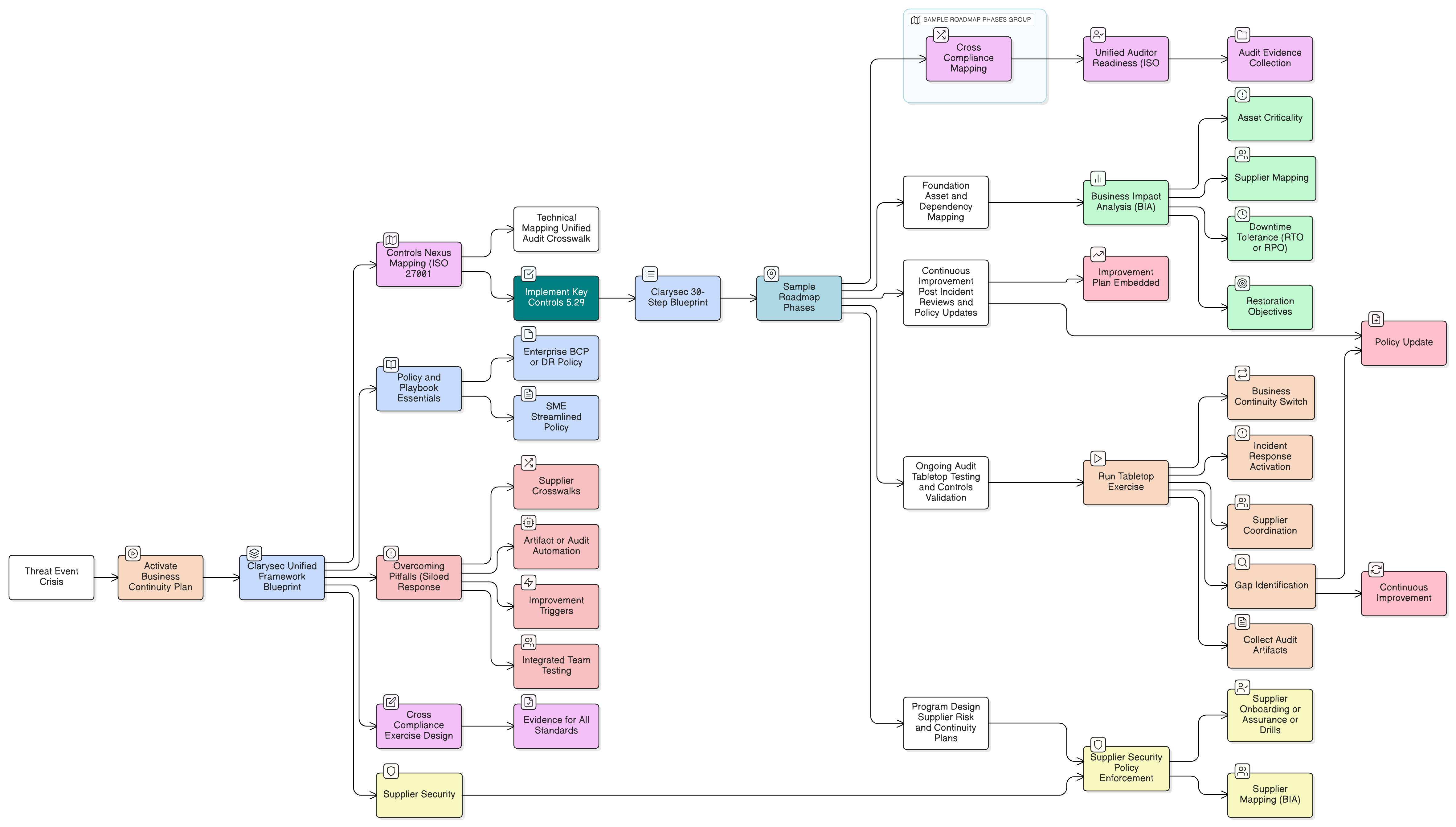
Resilience in ISO/IEC 27001:2022 means maintaining information security during disruption (Annex A control 5.29), robust ICT readiness for business continuity (5.30), and dependable information backup (8.13). The goal is to ensure your response doesn’t create new, more dangerous vulnerabilities. As described in the Clarysec Zenith Blueprint: An Auditor’s 30-Step Roadmap Zenith Blueprint, “auditors will seek alignment, not only with policy, but with reality.” This is where most organizations fall short-they plan for uptime but not for maintaining compliance through the chaos.
The Foundation: Why Resilience Starts with Context, Not Controls
Before you can effectively implement specific resilience controls, you must build a solid Information Security Management System (ISMS). Many organizations falter here, jumping straight to Annex A without laying the proper groundwork.
The Zenith Blueprint emphasizes starting with the core ISMS clauses, as this foundational work is the bedrock of resilience. The process begins with understanding your organization’s unique environment:
- Clause 4: Context of the Organization: Understanding your organization’s context, including internal and external issues and stakeholder requirements, and defining the scope of the ISMS.
- Clause 5: Leadership: Securing top management’s commitment, establishing an information security policy, and defining organizational roles and responsibilities.
- Clause 6: Planning: Conducting thorough risk assessment and treatment planning, and setting clear information security objectives.
For Maria’s fintech, a thorough analysis under Clause 4 would have identified regulatory pressures from DORA and NIS2 as key external issues. A risk assessment under Clause 6 would have modeled the exact ransomware scenario she’s now facing, highlighting the risk of compromised recovery environments and inadequate logging during an incident. Without this context, any resilience plan is just a shot in the dark.
The Twin Pillars of Operational Resilience in ISO/IEC 27001:2022
Within the ISO/IEC 27001:2022 framework, two Annex A controls stand out as the pillars of operational resilience: Information Backup (8.13) and Information security during disruption (5.29).
Control 8.13: Information Backup - The Essential Safety Net
This is the control everyone thinks they have covered. But a truly effective backup strategy is more than just copying files. It’s a corrective control focused on integrity and availability, and it is deeply interconnected with numerous other controls.
Attributes: Corrective; Integrity, Availability; Recover; Continuity; Protection.
Operational Capability: Continuity.
Security Domain: Protection.
Audit Insight: An auditor will require more than a “yes” to the question “Do you have backups?”. They will demand logs to prove recent backups exist, evidence that restore tests succeeded, and proof that backup media were encrypted, stored securely, and covered all critical assets defined in your inventory.
Scenario: A system is wiped by ransomware or a critical configuration error. Your ability to recover with integrity depends on a mature backup strategy. Auditors will verify that this strategy is not an island but is linked to other critical controls:
- 5.9 Inventory of information and other associated assets: You can’t back up what you don’t know you have. A comprehensive inventory is non-negotiable.
- 8.7 Protection against malware: Backups must be isolated and protected from the very ransomware they are meant to defeat. This includes using immutable storage or air-gapped copies.
- 5.31 Legal, statutory, regulatory and contractual requirements: Do your backup retention schedules and storage locations comply with data residency laws and contractual obligations?
- 5.33 Protection of records: Do your backups meet retention and privacy requirements for PII, financial records, or other regulated data?
Control 5.29: Information Security During Disruption - The Integrity Keeper
This is the control that separates a compliant ISMS from a resilient one. It directly addresses the critical questions haunting Maria during her crisis: how do we maintain security when our primary tools and processes are unavailable? Control 5.29 demands that security measures remain planned for and effective throughout a disruptive event.
Attributes: Preventive, Corrective; Protect, Respond; Confidentiality, Integrity, Availability.
Operational Capability: Continuity.
Security Domain: Protection, Resilience.
Audit Insight: Auditors review Business Continuity and Disaster Recovery plans specifically to find evidence of security considerations. They check alternate site security configurations, verify that logging and access controls are maintained, and scrutinize any fallback processes for security weaknesses, not just their ability to restore service.
Scenario: Your primary data center is offline, and you move operations to a backup site. Auditors expect to see evidence-site visit reports, configuration files, access logs-that the secondary site meets your primary security requirements. Did your emergency shift to remote work extend endpoint protection and secure access to all devices? Did you document decisions to temporarily relax and later reinstate any controls?
The Zenith Blueprint captures its essence perfectly: “What’s essential is that security doesn’t pause while systems are being restored. Controls may shift form, but the objective remains: keep information protected, even under duress.” This control forces you to plan for the messy reality of a crisis, and it is tightly woven with other controls:
- 5.30 ICT readiness for business continuity: Ensures the technical recovery plan doesn’t ignore the security plan.
- 8.16 Monitoring activities: Mandates that you have a way to maintain visibility even when primary monitoring tools are offline.
- 5.24 Information security incident management planning and preparation: Crisis and continuity teams must run concurrently, ensuring incident response awareness is maintained during the disruption.
- 5.28 Collection of evidence: Ensures that in the rush to restore, you don’t destroy crucial forensic evidence needed for investigation and regulatory reporting.
A Practical Guide to Implementing Auditable Resilience
Translating these controls from theory into practice requires clear, actionable policies and procedures. Clarysec’s policy templates are designed to embed these principles directly into your ISMS. For example, our Backup and Restore Policy Backup and Restore Policy provides a framework that goes beyond simple backup schedules:
“The policy enforces ISO/IEC 27001:2022 controls related to collection of evidence (5.28), resilience during disruption (5.29), operational recovery (8.13), and information deletion (8.10), and maps to best practices from ISO/IEC 27002:2022, NIST SP 800-53 Rev.5, GDPR, DORA, and NIS2.”
This holistic approach transforms resilience from an abstract concept into a set of auditable, operational tasks.
Actionable Checklist: Auditing Your Backup and Resilience Strategy
Use this checklist, guided by a comprehensive policy, to prepare the evidence an auditor will demand.
| Audit Question | Control Reference | Clarysec Policy Guidance | Evidence to Prepare |
|---|---|---|---|
| Is your backup scope aligned with your BIA and asset inventory? | 8.13, 5.9 | The policy requires linking the backup schedule to the criticality classification of information assets. | Asset inventory with criticality ratings; backup configuration showing prioritized systems. |
| Are restore tests conducted regularly, and are results documented? | 8.13, 9.2 | The policy defines a minimum testing frequency and mandates the creation of a test report, including time-to-restore metrics and data integrity checks. | Restore test plans and reports from the last 12 months; records of any corrective actions taken. |
| How are backups protected from ransomware? | 8.13, 8.7 | The policy specifies requirements for immutable storage, air-gapped copies, or isolated backup networks, aligning with malware protection controls. | Network diagrams; configuration details of backup storage; vulnerability scans of the backup environment. |
| Are security controls maintained during a restore operation? | 5.29, 8.16 | The policy references the need for secure recovery environments and continued logging, ensuring alignment with the organization’s incident response plan. | Incident response plan; documentation of the secure “sandbox” for restores; logs from a recent restore test. |
| Do backup retention schedules align with data protection laws? | 8.13, 5.34, 8.10 | The policy mandates that backup retention rules must comply with the Data Retention Schedule to avoid indefinite storage of PII, supporting GDPR’s Right to Erasure. | Data Retention Schedule; backup job configurations showing retention periods; procedures for deleting data from backups. |
The Cross-Compliance Imperative: Mapping Resilience to DORA, NIS2, and Beyond
For organizations in critical sectors, resilience is not just an ISO/IEC 27001:2022 best practice; it’s a legal mandate. Regulations like the Digital Operational Resilience Act (DORA) and the NIS2 Directive place enormous emphasis on the ability to withstand and recover from ICT disruptions.
Fortunately, the work you do for ISO/IEC 27001:2022 provides a powerful head start. Clarysec’s Zenith Controls: The Cross-Compliance Guide Zenith Controls is designed to create explicit mapping tables that demonstrate this alignment to auditors and regulators. Proactive documentation shows you are managing security in its full legal context.
Our policies are built with this in mind. The Data Protection and Privacy Policy Data Protection and Privacy Policy, for instance, explicitly states its role in reinforcing compliance with DORA and NIS2 alongside ISO/IEC 27001:2022.
This mapping table illustrates how core resilience controls satisfy requirements across multiple major frameworks.
| Framework | Key Clauses/Articles | How Resilience Controls (5.29, 8.13) Map | Audit Expectations |
|---|---|---|---|
| GDPR | Art. 32, 34, 5(1)(f), 17(1) | Data protection continues under duress; backup systems must support restoration and erasure rights; breach notification is required for vulnerabilities arising during crises. | Review of backup logs, restore tests, evidence of data erasure from backups, and incident logs during disruption. |
| NIS2 | Art. 21(2)(d), 21(2)(f), 21(2)(h), 23 | Operational resilience is non-negotiable; controls must ensure business continuity and backup validity; crisis management must keep information protected. | Scrutiny of business continuity plans, backup schedules, evidence that backup controls work as required, and incident handling reports. |
| DORA | Art. 10(1), 11(1), 15(3), 17, 18 | Mandatory resilience testing is required, with a cross-reference of incident handling, restoring from backup, and supplier controls for ICT services. | Audit of resilience drills, backup restore logs, supplier data recovery clauses, and incident reports. |
| COBIT 2019 | DSS04.02, DSS04, DSS01, APO12 | Business continuity and risk management must be intertwined; backup and restore capabilities are proven via metrics, logs, and continual improvement cycles. | Audit of continuity reviews, backup performance measures, logs, and records of remediation and improvement. |
| NIST SP 800-53 | CP-9, CP-10, MP-5, SI-12 | Backup solutions and incident response are cornerstone controls for recovery; logging and restore tests are mandatory to demonstrate capability. | Verification of restore capabilities, backup security, retention management, and incident handling procedures. |
By building your ISMS around the robust framework of ISO/IEC 27001:2022, you are simultaneously building a defensible position for these other stringent regulations.
Through the Auditor’s Eyes: How Your Resilience Will Be Tested
Auditors are trained to look past policies and search for proof of implementation. When it comes to resilience, they want to see evidence of discipline under pressure. An audit of your resilience capabilities will be multifaceted, with different auditors focusing on different types of evidence.
| Auditor’s Lens (Framework) | Key Focus Area | Types of Evidence Requested |
|---|---|---|
| ISO/IEC 27001:2022 / 19011 | Integration of Security into BC/DR Plans | Review of BC/DR documentation to confirm security considerations are embedded, not just tacked on. Verification that alternate sites have equivalent security controls. |
| COBIT 2019 (DSS04) | Continuous Improvement and Post-Incident Review | Examination of after-action reports from real disruptions or drills. The focus is on whether security gaps identified during the event were documented and remediated. |
| NIST SP 800-53A (CP-10) | Validation of Recovery and Reconstitution | Scenario-based testing, either through tabletop exercises or live drills. Auditors assess the organization’s ability to maintain security controls during the recovery process. |
| ISACA ITAF | Documented Risk Acceptance | Documentation and review of risk acceptances made during a disruption. Evidence must be in the risk register or BC plan, with clear authorization. |
Common Pitfalls: Where Resilience Plans Often Fail in Reality
Clarysec’s audit findings show recurring weaknesses that undermine even the best-written plans. Avoid these common pitfalls:
- Manual fallback processes lack security. When systems go down, employees revert to spreadsheets and email. These manual processes often lack the physical or logical security of the primary systems.
- Fix: Integrate physical protection (locked cabinets, access logs) and logical controls (encrypted files, secure communication channels) into your crisis protocols for manual workarounds.
- Alternate sites are not fully configured. The backup data center has servers and data but may lack equivalent firewall rules, logging agents, or access control integrations.
- Fix: Document security control equivalence between primary and secondary sites. Conduct regular technical audits of the backup site and include security representatives in all failover drills.
- Restore tests are incomplete or ad-hoc. Organizations test if a server can be restored but fail to test if the restored application is secure, logged, and performs correctly under load.
- Fix: Make comprehensive backup restore tests, including security validation, a mandatory part of incident drills and annual audit reviews.
- Data privacy in backups is overlooked. Backups can become a compliance liability, holding data that should have been deleted under GDPR’s Right to Erasure.
- Fix: Align backup retention and deletion procedures with your data privacy policies. Ensure you have a documented process for erasing specific data from backup sets when legally required.
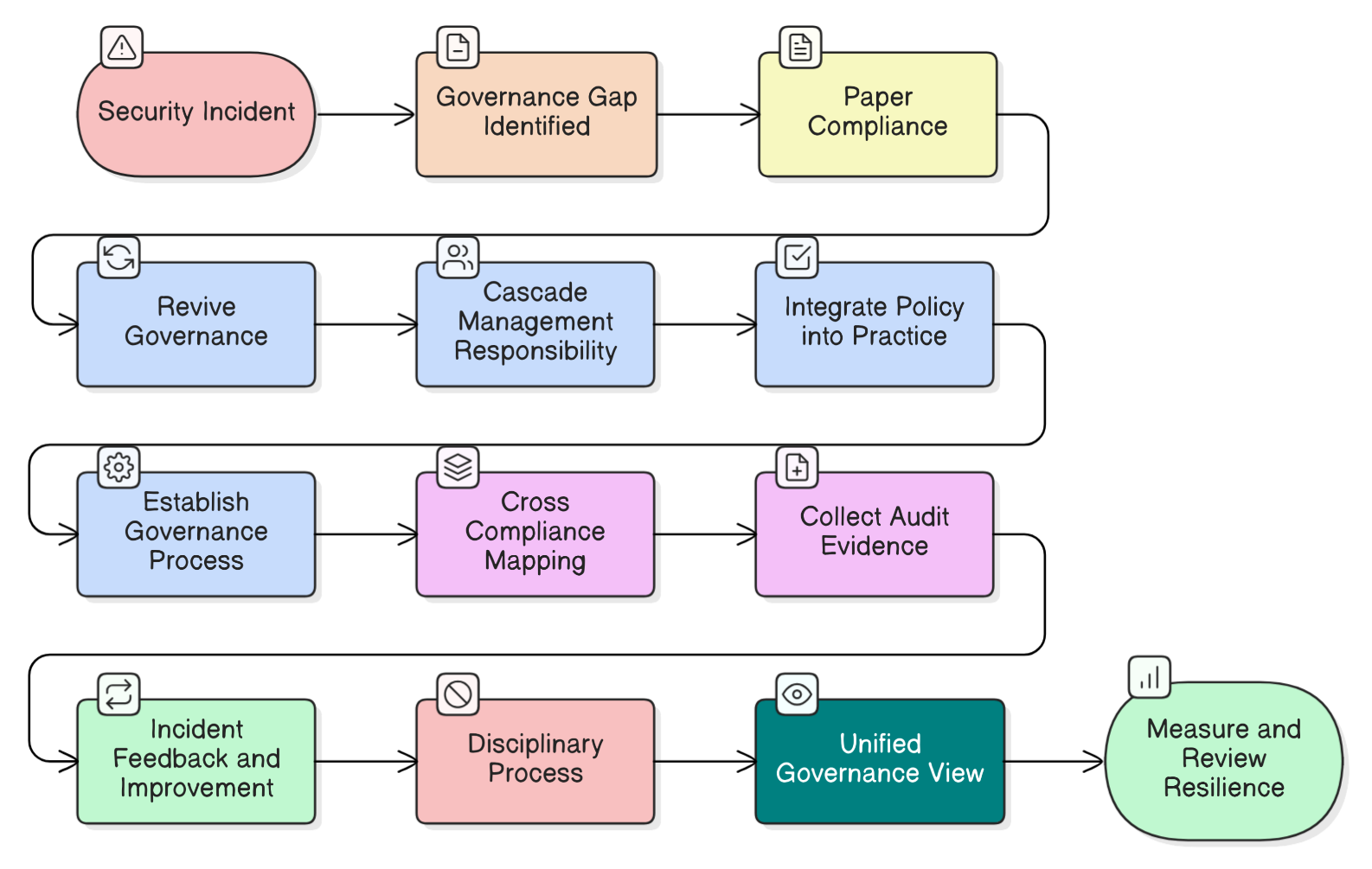
From Compliant to Resilient: Fostering a Culture of Continual Improvement
Achieving resilience is not a one-time project that ends with certification. It is an ongoing commitment to improvement, enshrined in Clause 10 of ISO/IEC 27001:2022. A truly resilient organization is one that learns from every incident, every near-miss, and every audit finding.
This requires moving beyond reactive fixes. The Zenith Blueprint suggests embedding continual improvement into the organizational culture by establishing channels for employees to suggest security improvements, conducting proactive risk assessments when significant changes occur, and performing rigorous post-incident reviews to capture lessons learned.
Furthermore, Control 5.35 (Independent review of information security) plays a crucial role. Inviting an independent party to review your ISMS provides an unbiased perspective that can uncover blind spots your internal team might miss. As the Zenith Blueprint powerfully states: “…what separates a compliant ISMS from a truly resilient one is this: the willingness to ask hard questions, and to listen when the answers are uncomfortable.”
Your Next Step: Building an Unbreakable ISMS
Maria’s crisis highlights a universal truth: disruption is inevitable. Whether it’s ransomware, a natural disaster, or a critical supplier failure, your organization will be tested. The question is not if, but how you will respond. Will you simply recover, or will you respond with resilience?
Building an ISMS that maintains integrity under pressure requires a strategic, holistic approach. It starts with a solid foundation, incorporates deeply interconnected controls, and is nurtured by a culture of continuous improvement. Don’t wait for a real-world disruption to reveal the gaps in your strategy.
Ready to build an ISMS that is not just compliant, but truly unbreakable?
- Download Clarysec’s Zenith Blueprint: An Auditor’s 30-Step Roadmap to guide your implementation from start to finish.
- Leverage our comprehensive policy templates, like the Backup and Restore Policy, to translate standards into concrete, auditable action.
- Use the Zenith Controls: The Cross-Compliance Guide to ensure your efforts meet the stringent demands of ISO/IEC 27001:2022, DORA, and NIS2.
Get in touch today for a free resilience assessment and let Clarysec’s experts help you build an ISMS that thrives under pressure.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council