From Blueprint to Audit-Ready: Mastering Application Security Requirements for ISO 27001, DORA, and NIS2
The pre-audit jitters were palpable. For Maria, the CISO of a mid-sized fintech firm, the upcoming DORA compliance assessment felt less like a review and more like a reckoning. Her team was sharp, her infrastructure hardened, but a nagging vulnerability kept her awake at night: the sprawling, chaotic world of their applications.
The latest concern was a new customer-facing payment portal, rushed to market to meet quarterly targets. The development team, working under an aggressive agile model, had checked all the functional boxes. But when Maria’s team ran a preliminary scan, the results confirmed her fears.
The portal lacked robust session timeout rules, its input fields were susceptible to basic injection attacks, and error messages were leaking sensitive system information. These were not sophisticated zero-day exploits; they were fundamental design flaws. The root cause was painfully clear. Security requirements were never formally defined, documented, or integrated into the development sprints. The team had a vague mandate to “make it secure,” but without a concrete blueprint, security remained an ambiguous and often-ignored afterthought.
This scenario is not unique. It highlights the critical gap many CISOs and compliance leaders face: turning the intention of “we do security” into explicit, testable application security requirements that align with foundational standards like ISO/IEC 27001:2022 and major regulations like NIS2, DORA, and GDPR.
The High Cost of Ambiguity: What Compliance Actually Expects
The core of Maria’s problem lies in a common organizational failure: treating security as a quality attribute rather than a set of non-negotiable requirements. An effective security requirement is specific, measurable, and testable. “The application must be secure” is a wish. “The application must enforce 15-minute idle session timeouts, validate all user-supplied input against a predefined character set, and encrypt all data in transit using TLS 1.3” is a requirement. This clarity is what auditors look for and what developers need to build secure software.
Without it, you invite a cascade of failures:
- Inconsistent Implementation: Different developers interpret “secure” differently, leading to a patchwork of controls with unpredictable gaps.
- Increased Remediation Costs: Finding and fixing a design flaw in production is exponentially more expensive than addressing it in the design phase.
- Audit Non-Conformities: Auditors will quickly identify the absence of a structured process for defining security requirements, leading to major findings.
- Business Risk: Each undefined requirement is a potential attack vector, exposing the organization to data breaches, financial loss, and reputational damage.
Across modern standards, the expectation is consistent: security must be defined as requirements, early, and tied to risk and law. ISO/IEC 27002:2022 guidance on control 8.26, Application security requirements, expects organizations to systematically determine, document, and approve security requirements based on formal risk assessment and regulatory demands.
This single principle is the linchpin for a wide array of compliance mandates. Clarysec’s cross-compliance mapping within the Zenith Controls: The Cross-Compliance Guide Zenith Controls shows how this concept appears everywhere:
- GDPR Articles 25 and 32 expect “data protection by design” and “security of processing”.
- NIS2 Article 21(2)(d)-(e) emphasizes secure development and supply chain security.
- DORA Articles 6(4), 8, 10, and 11 require ICT risk management and security by design for financial entities.
- NIST SP 800-53 Rev.5 in controls SA-4 and SA-15 demands defined system security requirements and secure development practices.
- COBIT 2019 in processes BAI03 and DSS05 requires security-related requirements to be aligned to business and compliance before a solution is built.
The goal is to define, in the words of the Zenith Blueprint: An Auditor’s 30-Step Roadmap Zenith Blueprint, “what security means for your applications, before a single line of code is written.”
Why Traditional Approaches Fail: Checklists, Late Testing, and Security Theatre
Most organizations already do some form of application security. The problem is that it is rarely structured in a way that stands up under ISO/IEC 27001:2022 certification or regulatory scrutiny.
Common failure patterns include:
- Generic Checklists: Teams reuse a one-page “secure coding checklist” for every project. It is not tied to the application’s specific risks, data sensitivity, or regulatory context. When an auditor asks how the checklist maps to GDPR Article 25, there is no clear answer.
- Security as a Late Gate: Security requirements are not embedded in design or user stories. They appear at the end as a request for a penetration test. The Zenith Blueprint warns that “relying on a security checklist at the end of the project doesn’t work, those requirements must shape the architecture, influence library choices, and guide feature prioritization from day one.”
- No Traceability from Requirement to Test: A requirement might exist to “encrypt data in transit,” but there is no linked test case verifying TLS version enforcement, certificate validity, and cipher strength. The Zenith Blueprint insists that expectations must be measurable and testable, with security tests mapped directly to their corresponding requirements.
- Ad Hoc Handling of Third-Party Code: Modern applications are often “stitched together from internal code, third-party libraries, APIs, and cloud-native services,” as noted in the Zenith Blueprint. Without explicit requirements for suppliers and open-source components, supply chain risk remains a massive, uncontrolled blind spot.
The result is security theatre: documents exist and tests are run, but when a serious auditor or regulator looks for a coherent requirements story, the entire process falls apart.
Building the Foundation: From Policy to Practice
A disciplined approach to application security starts with clear governance. Policy is not just bureaucracy; it is the official source of truth that empowers teams and provides auditors with a clear statement of intent. At Clarysec, we design policies that are both authoritative and practical.
Our Application Security Requirements Policy Application Security Requirements Policy establishes non-negotiable ground rules. For example, clause 5.2 under ‘Governance Requirements’ mandates:
All applications must undergo security requirements validation during planning or procurement, with documented approval from the Application Security team.
This simple directive prevents the “build first, secure later” mentality. The policy also assigns clear accountability. Clause 4.3.1 under ‘Roles and Responsibilities’ states that developers are expected to:
Implement applications in compliance with defined security requirements and standards.
This shifts the onus of security from a separate, often adversarial, security team to the creators of the software themselves. Furthermore, the policy connects the dots between different security domains. Clause 10.2 references its integration with other key controls:
P4 – Access Control Policy. Defines the identity and session management standards that must be enforced by all applications, including strong authentication, least privilege, and access review requirements.
For smaller organizations, a tailored policy like our Application Security Requirements Policy - sme Application Security Requirements Policy-sme ensures these principles are scalable. It recognizes that while the risks are similar, the implementation must be pragmatic. Both versions ultimately aim for the same outcome, ensuring application security is fully integrated into the ISMS and audit-ready.
A Practical Roadmap: Building Audit-Ready Application Security Requirements
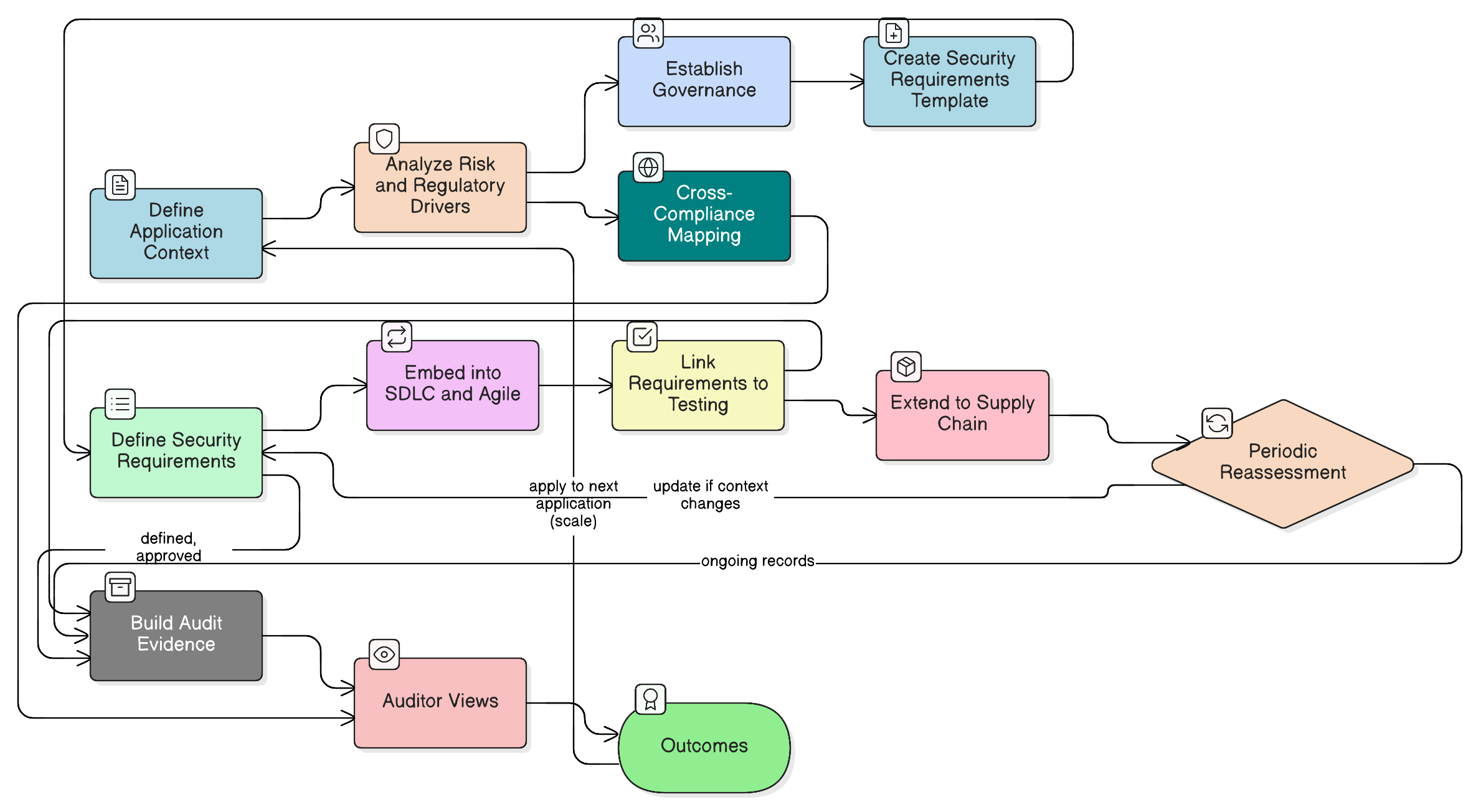
Policy sets the “what” and “why,” but developers and project managers need the “how.” A structured implementation guide is indispensable for translating high-level controls into actionable steps. Step 21 of the Zenith Blueprint, which focuses on ISO/IEC 27002:2022 control 8.26, provides a clear, six-step methodology.
Let’s walk through this process, using Maria’s payment portal as our example.
Step 1: Start from Risk and Regulatory Context
Using risk assessment output aligned with ISO/IEC 27005:2024 (risk treatment), you first identify the context:
- Application: Customer self-service payment portal.
- Data: PII, credentials, payment tokens.
- Jurisdictions: EU, financial services, cloud-hosted.
- Regulations: GDPR, DORA, PCI DSS.
Based on the guidance for control 8.26 in Zenith Controls and its related ISO standards (27034-1, 27017, 27701), your starting requirements categories must include identification and authentication, authorization, data classification, input validation, logging, and data protection in transit and at rest.
Step 2: Create or Adopt a Security Requirements Template
The Zenith Blueprint recommends creating a standardized template to ensure every project answers the same fundamental security questions. This document should become part of your project kickoff toolkit.
Minimum sections should include:
- Application name, owner, and criticality.
- Data categories and sensitivity levels.
- Applicable regulatory and contractual obligations (GDPR, DORA, etc.).
- Threat landscape inputs (derived from control 5.7 Threat intelligence).
- Specific security requirements by category (authentication, logging, etc.).
- Linkages to user stories and acceptance criteria.
- Linkages to test cases (functional, security, penetration).
- Supplier and third-party component requirements.
Step 3: Embed Requirements into Agile Artifacts
Security requirements must be embedded directly into user stories and acceptance criteria. For the “customer registration” epic in Maria’s portal project, this means transforming a simple functional story into a security-aware one.
- Original User Story: “As a new user, I can create an account.”
- Secure User Story: “As a new customer, I want to create a secure account so that my payment information is protected.”
- Acceptance Criteria (with embedded security):
- The system must enforce a strong password policy in line with the P4 – Access Control Policy.
- The system must require email verification via a one-time link before the account is activated.
- The account creation form must be protected by CAPTCHA to prevent bot attacks.
- All registration attempts must be logged with source IP and device fingerprint.
- All data submitted via the form must be sanitized to prevent cross-site scripting (XSS).
These are not separate security tasks; they are integral to the feature’s definition of “done.”
Step 4: Link Requirements to Security Testing
Using control 8.29 Security testing from Zenith Controls, you ensure each requirement has an associated test case. This closes the loop and provides auditable evidence of control effectiveness.
- Requirement: Encryption in transit with TLS 1.3. → Test: Automated scan to verify TLS enforcement, certificate validity, and approved cipher suites.
- Requirement: Input validation to prevent SQL injection. → Test: Automated SAST/DAST scanning and manual fuzzing during QA.
- Requirement: 15-minute idle session timeout. → Test: Automated and manual tests to confirm session invalidation on the server side after 15 minutes of inactivity.
Step 5: Extend Requirements to the Supply Chain
Because ISO control 8.26 is tied to supplier security (5.19, 5.20) and outsourced development (8.30) in Zenith Controls, your process must account for third-party code. For SMEs heavily reliant on external libraries, the policy clause from the Application Security Requirements Policy - sme is critical:
Any third-party tool, plugin, or external code library used in an application must be recorded and reviewed annually for security impact and patch status.
This simple, pragmatic requirement forces a software bill of materials (SBOM) mindset, which is a key expectation under regulations like NIS2. For major suppliers, the same application security requirements must be included in contracts, referencing ISO/IEC 27036-1 (ICT supply chain security).
Step 6: Institute Periodic Reassessment
As applications evolve, so do their risks. The Zenith Blueprint guidance on periodic reassessment is crucial. When you integrate a new API or move to a different cloud service, the risk context changes. This must trigger a review of the existing security requirements to ensure they are still adequate. This aligns with ISO/IEC 27005:2024 (ongoing risk treatment) and turns application security into a continuous practice, not a one-time project.
Deconstructing the Control Ecosystem
An ISO control never exists in a vacuum. Effective security relies on an interconnected web of measures. The true power of control 8.26 is unlocked when you understand its relationship with other controls, a perspective detailed in Zenith Controls.
Control 8.26 is classified as a preventive control, but it acts as the central hub for the entire secure development process, connecting to:
- 8.25 - Secure development life cycle: This is the overarching framework. Control 8.26 provides the specific what (the requirements) that must be integrated into the how (the SDLC process).
- 8.27 - Secure system architecture and engineering principles: Requirements drive architectural decisions, ensuring security is foundational.
- 8.28 - Secure coding: Once requirements are defined (e.g., “prevent SQL injection”), secure coding standards provide developers with the techniques to meet that requirement.
- 8.29 - Security testing in development and acceptance: This control validates that the requirements defined in 8.26 were correctly implemented.
- 5.34 - Privacy and protection of PII: When an application handles personal data, the requirements from 8.26 must incorporate the principles of privacy by design.
- 5.19 & 5.20 - Information security in supplier relationships: For acquired or outsourced applications, control 8.26 dictates that your security requirements must extend into the supply chain.
Viewing these controls as an ecosystem rather than a checklist allows you to build a multi-layered, defensible security posture.
The Auditor’s Lens: Preparing for Scrutiny
Auditors think in terms of evidence. To prepare, you must understand the different perspectives an auditor might bring. The audit methodology section in Zenith Controls anticipates these varied approaches.
| Auditor Background | Primary Focus | Likely Evidence Requests |
|---|---|---|
| ISO/IEC 27007 Auditor | ISMS Process Integration: Is the process for defining requirements integrated into the ISMS? Is it subject to internal audit and management review? | - Records of security requirements for a sample of recent projects. - Evidence linking requirements to risk assessments. - Meeting minutes where security requirements were discussed and approved. |
| COBIT 2019 Auditor | Business Alignment & Governance: Are security requirements aligned with business objectives (BAI02) and part of the solutions build process (BAI03)? | - Governance documentation defining the requirements process. - Traceability matrix from business needs to security requirements. - Evidence of stakeholder (business, IT, security) sign-off. |
| NIST SP 800-53A Assessor | Control Implementation & Effectiveness: Can you demonstrate that procedures for SA-4 (Acquisition Process) and SA-15 (Development Process) are implemented and effective? | - System security plans (SSPs) documenting the application’s requirements. - Test results from assessments that validate the implementation. - Change records showing requirements are reassessed upon modification. |
| ISACA (ITAF) Auditor | Evidence & Testing: Is the evidence sufficient, reliable, and relevant? | - Walkthrough of the JIRA/Azure DevOps workflow showing how security user stories are tracked and tested. - Sample of code review checklists. - Output from SAST/DAST tools configured to check for policy violations. |
Understanding these lenses allows you to prepare a comprehensive evidence portfolio that demonstrates a living, breathing process embedded in your organization.
The Cross-Compliance Compass: One Process, Many Frameworks
For a firm like Maria’s, satisfying DORA, GDPR, and NIS2 is mandatory. Manually mapping controls is a recipe for duplicated effort and compliance gaps. A centralized, cross-compliance approach provides immense value. Defining application security requirements is the practical implementation of the “security by design” principle that underpins all these modern regulations.
| Framework | Relevant Clause/Article | How It Connects to Application Security Requirements |
|---|---|---|
| EU DORA | Articles 6(4), 8, 10, 11 | Mandates that ICT risk management includes security-by-design principles and requires secure development processes. Defining requirements is the first step. |
| EU NIS2 | Article 21(2)(d)-(e) | Requires entities to implement policies on secure acquisition, development, and maintenance. This begins with clear, risk-based requirements. |
| EU GDPR | Articles 25 and 32 | Article 25, “Data protection by design and by default,” directly mandates that data protection measures are built into processing activities from the start. |
| NIST SP 800-53 Rev.5 | SA-4, SA-15 | These control families cover acquisition and development processes, explicitly calling for the definition and management of security requirements throughout the lifecycle. |
| COBIT 2019 | BAI03, DSS05 | Requires that security requirements are defined upfront to align with enterprise goals before solutions are built or acquired. |
By implementing a robust process for application security requirements based on ISO/IEC 27002:2022, you are simultaneously building evidence to satisfy a significant portion of these other regulations. You are not just “doing ISO”; you are building a universally compliant security program.
From Chaos to Control: Your Path Forward
Maria’s story has a positive outcome. She used the incident with the payment portal as a catalyst for change. Armed with a clear policy framework from Clarysec and a practical implementation guide, she brought her development, security, and product teams together. They used the Zenith Blueprint methodology to retrospectively define requirements for the portal, prioritizing remediation based on risk.
More importantly, they established a new way of working. The “security checklist” was replaced by collaborative design sessions. When the DORA auditors arrived, Maria could not only show them a secure application but also demonstrate a mature, repeatable process for ensuring all future applications would be built on a foundation of security.
Transforming your application security posture begins with a single, structured step. Your path forward is clear:
- Establish Governance: Implement a formal policy for defining application security requirements. Our templates, like the Application Security Requirements Policy, provide an audit-ready starting point.
- Adopt a Practical Framework: Use the Zenith Blueprint to integrate security requirements directly into your development lifecycle, making them actionable, testable, and traceable.
- Understand the Full Context: Leverage Zenith Controls to see how this critical control connects to the broader security ecosystem and maps across DORA, NIS2, GDPR, and more.
- Scale to Your Portfolio: Once the approach works for one application, scale it across your portfolio by integrating your Security Requirements Template into standard project kickoff checklists, agile templates, and procurement processes.
If you want to accelerate this transformation, Clarysec provides the pre-built policies, implementation roadmaps, and cross-compliance mappings to move you from fragmented efforts to a demonstrably mature and audit-ready program. Stop treating application security as a final-gate inspection. Start building it into the blueprint of everything you create.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council