The NIS2 24-Hour Test: Building an Incident Response Plan That Survives Breaches and Audits
The CISO’s 2:13 a.m. Nightmare: When the NIS2 Clock Starts Ticking
It’s 2:13 a.m. in your European Security Operations Center. The phone rings, fracturing the uneasy silence. An automated system has flagged abnormal traffic leaving a critical database. Moments later, a string of “account locked” messages floods the helpdesk dashboard. For Maria, the CISO, the cold reality of the NIS2 Directive hits home. The clock has started. She has 24 hours to provide an early warning notification to the national CSIRT.
Her on-call manager scrambles through the incident response procedure, only to find inconsistent escalation paths between IT and business units. Panic is a luxury she can’t afford. Who needs to be on the emergency call? Is this a “significant” incident under the directive’s definition? Where is the playbook for data exfiltration containment? Communications lag, response actions stumble amid confusion, and the critical 24-hour reporting window ticks relentlessly forward.
This scenario is not an isolated tale-it’s the lived reality for organizations that treat incident response as a paperwork exercise. As NIS2 takes full effect, the stakes skyrocket: explosive regulatory liability, deep reputational harm, and a burning question from the board-“How did this happen?” A dusty plan on a shelf is no longer enough. You need a living, breathing capability that is practical, tested, and understood by everyone from the helpdesk to the boardroom.
Clarysec has helped dozens of organizations transform their incident response plans (IRPs) from static documents into living, auditable systems that stand the pressure test of both breach and boardroom. In this guide, we go beyond theory to show how to construct, audit, and mature a NIS2-compliant IRP, mapping every move to ISO/IEC 27001:2022, DORA, GDPR, and other critical frameworks.
What NIS2 Demands: Precision, Speed, and Operational Clarity
The NIS2 Directive reshapes the regulatory terrain for incident response, demanding evidence of a mature, structured approach. It isn’t satisfied with vague policies or simple notification templates. Here’s what NIS2 expects of your organization:
- Documented, Actionable Procedures: Your IRP must show clear, repeatable steps for containment, eradication, and recovery. Generic policies are insufficient. Activities must be logged, tested at planned intervals, and all evidence recorded.
- A Multi-Stage Reporting Process: Article 23 is unequivocal. You must provide an “early warning” to regulators within 24 hours of becoming aware of a significant incident, followed by a more detailed notification within 72 hours, and a final report within one month. Fumbling here is a direct compliance failure.
- Integration with Business Continuity: Incident handling is not an isolated IT function. It must be synchronized with broader business continuity and disaster recovery plans, ensuring that roles, communications, and recovery objectives are harmonized.
- Predefined Criteria for Incident Analysis: Every reported event must be assessed against established thresholds for impact, scope, and severity. This ensures that neither overreaction nor dangerous underestimation occurs, and it provides a defensible basis for deciding when to start the 24-hour clock.
- A Continuous Improvement Loop: After an incident, entities are expected to conduct post-mortems to identify root causes, document lessons learned, and improve future incident handling capabilities. NIS2’s real legacy is relentless accountability.
At Clarysec, we see this not as a burden, but as an opportunity to build genuine cyber resilience. Our Incident Response Policy (Incident Response Policy) formalizes this by stating:
The organization shall maintain a centralized and tiered Incident Response Framework aligned with ISO/IEC 27035, consisting of defined response phases.
This framework is the bedrock of a compliant and effective program, moving your team from reactive firefighting to a coordinated, predictable response.
The Decisive Moment: Turning Events into Incidents
In Maria’s crisis, the first critical question was, “Is this a reportable incident?” The flood of alerts from a modern security stack can be overwhelming. Without a clear method to distinguish routine events from genuine incidents, teams either overreact to everything or miss the critical signals. This is where analytical discipline, as defined by ISO/IEC 27002:2022 control 5.25 - Assessment and decision on information security events, becomes paramount.
This control ensures your organization doesn’t just monitor; it understands and decides. It is the decision point that determines when an event crosses the threshold into a security incident, triggering formal response procedures. The Zenith Blueprint: An Auditor’s 30-Step Roadmap (Zenith Blueprint) highlights this, noting that an effective process “must take into account the organization’s classification model, risk tolerance, and regulatory environment.”
A gut decision is not a defensible position for auditors or regulators. In practice, this means:
- Establishing Criteria: Defining what constitutes a significant incident based on impact to service delivery, data sensitivity, system criticality, and specific NIS2 thresholds.
- Triage and Analysis: Using the criteria to assess incoming events, correlating data from multiple sources like logs, endpoint detection, and threat intelligence.
- Documenting the Decision: Recording who assessed the event, what criteria were used, and why a particular course of action was chosen. This traceability is non-negotiable for an audit.
Our Zenith Controls: The Cross-Compliance Guide (Zenith Controls) details how control 5.25 is the lynchpin connecting monitoring activities with formal incident response. It operationalizes your preparedness, ensuring that the right alarms are sounded for the right reasons. Without a structured assessment process, Maria’s team would lose precious hours debating severity. With one, they can quickly classify the event, trigger the appropriate playbook, and start the formal notification process with confidence.
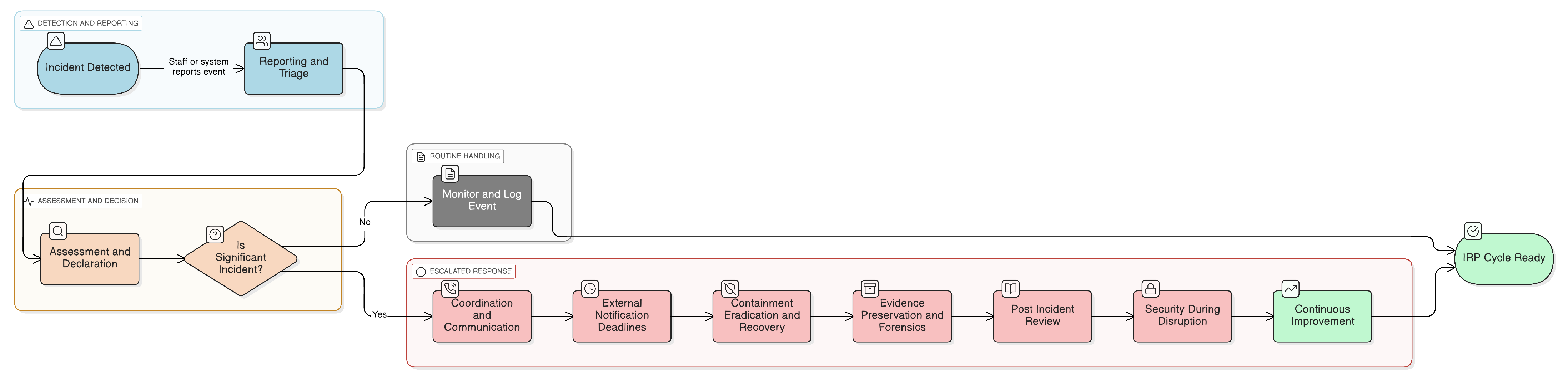
The Engine Room of Response: A Step-by-Step Blueprint
A world-class incident response plan operationalizes every phase of a crisis, from the first alert to the final lesson learned. This sequence maps directly to ISO/IEC 27001:2022 and the expectations of NIS2 regulators.
1. Reporting and Triage
A robust IRP starts with clear, accessible reporting channels for both humans and machines.
“Staff must report any suspicious activity or confirmed incident to incident@[company] or verbally to the GM or IT provider.”
Incident Response Policy-sme, Policy Implementation Requirements, clause 6.2.1. (Incident Response Policy-sme)
For larger enterprises, this is supplemented by automated SIEM alerts and well-defined escalation paths. The Incident Response Policy makes this mandatory:
“Incident response roles and escalation paths must be documented in the Incident Response Plan (IRP) and exercised through periodic tabletop and live drills.”
Governance Requirements, clause 5.4.
2. Assessment and Declaration
This is where control 5.25 comes to life. The response team assesses the event against the predefined matrix. Is customer data involved? Does it affect a critical service? Does it meet the NIS2 definition of “significant”? Once the threshold is crossed, an incident is formally declared, and the clock for external notification officially starts. This decision must be logged with a timestamp and rationale.
3. Coordination and Communication
Once an incident is declared, chaos is the enemy. A pre-defined communication plan prevents confusion and ensures stakeholders act as one.
“All incident-related communications must follow the Communications and Escalation Matrix…”
Governance Requirements, clause 5.5. (Incident Response Policy)
Your plan must clearly define:
- Internal Roles: The core incident response team, executive sponsors, legal counsel, and HR.
- External Contacts: The national CSIRT, data protection authorities, key customers, and PR or crisis communications firms.
- Notification Timelines: Explicitly state the 24-hour NIS2 early warning, 72-hour GDPR notification, and any other contractual or regulatory deadlines.
4. Containment, Eradication, and Recovery
These are the technical phases of the response, guided by ISO/IEC 27002:2022 control 5.26 - Response to information security incidents. Actions must be timely, logged, and designed to preserve evidence. This can include isolating affected systems, disabling compromised accounts, blocking malicious IP addresses, removing malware, and restoring clean data from backups. Each action must be documented to provide a clear timeline for auditors and regulators.
5. Evidence Preservation and Forensics
Regulators and auditors fixate here. Can you demonstrate the integrity of logs and records? This is the domain of ISO/IEC 27002:2022 control 5.28 - Collection of evidence. The Zenith Blueprint makes this an explicit audit checkpoint:
“Confirm that procedures are in place to preserve forensic evidence (5.28), including log snapshots, backups, and secure isolation of impacted systems.”
From ‘Audit & Improvement’ phase, Step 24.
Procedures must ensure a clear chain of custody for all digital evidence, which is critical for root cause analysis and potential legal action.
6. Post-Incident Review and Lessons Learned
NIS2 demands improvement, not repetition of failure. ISO/IEC 27002:2022 control 5.27 - Learning from information security incidents codifies this. After the incident is resolved, a formal review must be conducted to analyze what went well, what failed, and what needs to change.
The Zenith Blueprint reinforces this:
“Capture and log all decisions, roles, and communications, and update the plan with lessons learned (5.27).”
This creates a feedback loop that strengthens your policies, playbooks, and technical controls, turning every crisis into a strategic capability improvement.
The Unseen Challenge: Maintaining Security During Disruption
One of the most overlooked aspects of incident response is maintaining security while your organization is in a degraded state. Attackers often strike when you are most vulnerable: during recovery. This is the focus of ISO/IEC 27002:2022 control 5.29 - Information security during disruption. It bridges the gap between business continuity and information security, ensuring recovery efforts don’t bypass essential safeguards.
As the Zenith Controls guide explains, this control works alongside incident response planning to ensure security is not compromised while responding to incidents. For example, if you activate a disaster recovery site, control 5.29 ensures its security configurations are current. If you resort to manual processes, it ensures sensitive data is still handled securely. This has direct relevance for NIS2 compliance, which mandates measures for “business continuity, such as backup management and disaster recovery, and crisis management.”
An auditor will check for this by asking:
- How do you verify backups are free from malware before restoration?
- Is your recovery environment securely configured and monitored?
- How is emergency access controlled and logged?
Integrating security into your continuity plans prevents your team from making a bad situation worse.
An Auditor’s Perspective: Your Plan Under the Microscope
Auditors cut through jargon to find the truth. They won’t just ask to see your plan; they’ll ask, “What happened the last time something went wrong?” They expect a coherent story backed by evidence. A mature program provides consistent answers, regardless of the auditor’s framework.
Here is how different auditors will probe your NIS2 incident response capabilities:
| Framework / Standard | Auditor’s Focus | Example Questions & Evidence Required | How Your NIS2 Plan Responds |
|---|---|---|---|
| ISO/IEC 27001:2022 | ISMS Integration | “Show me how your incident response plan (5.24) is supported by logging and monitoring controls (8.15, 8.16) and how lessons learned (5.27) feed back into your risk assessment.” | The IRP is a formal ISMS document, with incident logs and post-incident reports serving as auditable records of the Plan-Do-Check-Act cycle. |
| NIS2 Directive | Regulatory Timeliness & Reporting | “Provide records for the last significant incident. How did you determine it was reportable? Show me the timestamp of discovery and the timestamp of the 24-hour early warning submission.” | The plan includes a specific NIS2 reporting playbook with CSIRT contact details, predefined report templates, and a decision log for classifying incident significance. |
| COBIT 2019 | Governance & Continuous Improvement | “Provide after-action reports from your last two drills. How were findings tracked (DSS04.07)? Show me how you updated the continuity plan based on lessons learned.” | The post-incident review process is formalized, with findings tracked in a risk register or GRC tool, ensuring accountability for improvement actions. |
| NIST Cybersecurity Framework | Operational Capability | “Walk me through your process for analyzing and triaging events (DE.AE). How do you validate an anomaly is a confirmed incident requiring a response (RS.AN)?” | Triage procedures are documented in runbooks, referencing the classification matrix (control 5.25) and showing clear steps from detection to response. |
| ISACA (ITAF) | Legal & Compliance | “How do you ensure evidence is preserved for legal and regulatory purposes (control 5.28)? Show me the documented risk acceptance for scenarios where timely reporting is challenging.” | Evidence collection procedures are part of the IRP, with guidelines on chain of custody. Risk acceptance for known gaps is formally documented and approved. |
Using Zenith Controls allows you to map these requirements transparently, ensuring you have a single, defensible narrative for every audit flavor.
Cross-Compliance: Mapping NIS2 to DORA, GDPR, and Beyond
NIS2 rarely stands alone. It intersects with privacy, financial, and operational requirements. A unified approach is not just efficient; it’s essential for avoiding contradictory processes during a crisis.
The Zenith Blueprint notes:
“NIS2 requires a range of security measures and a risk-based approach. By doing… ISO 27001 risk management, you are inherently satisfying the NIS2 expectation… NIS2 also mandates incident reporting within specific timelines, ensure you have an incident response plan… to cover that compliance aspect.”
Zenith Controls connects the dots for you:
- NIS2: Article 23 (Incident Notification) is directly addressed by the decision points in control 5.25 and the communication matrix in your IRP.
- GDPR: The breach notification workflow (Art. 33/34) is tied to the same assessment and escalation process, ensuring the Data Protection Officer is engaged immediately if personal data is affected.
- DORA: Major ICT-related incident classification and reporting (Article 18) for the financial sector converges with the structures built for NIS2, using a harmonized severity matrix.
By building your IRP on the foundation of ISO/IEC 27001:2022, you create a single, robust framework that can satisfy multiple regulators simultaneously.
Your Next Steps to a Battle-Tested, NIS2-Ready IRP
The 24-hour test is coming. Waiting for an incident to discover the gaps in your plan is a risk no business can afford. Take these steps now to build resilience and confidence.
- Benchmark Your Current Plan: Use the auditor questions in the table above as a self-assessment checklist. Is your plan practical and understood by those who must execute it? Identify your blind spots now.
- Formalize Your Framework: If you don’t have one, establish a formal Incident Response Framework using a proven foundation. Our policy templates, including the Incident Response Policy and Incident Response Policy-sme, provide a starting point aligned with ISO standards and regulatory requirements.
- Map Your Compliance Obligations: Use a tool like Zenith Controls to understand how controls like 5.25 and 5.29 map across NIS2, DORA, and GDPR. This ensures you build a plan that is efficient and satisfies multiple requirements.
- Test, Test, and Test Again: Conduct regular tabletop exercises. Start with simple scenarios like a phishing report and work your way up to a full-blown ransomware simulation. Use the insights to refine your playbooks, update your contact lists, and train your team.
- Book a Clarysec Maturity Assessment: Audit your plan against the latest NIS2 and ISO/IEC 27001:2022 guidance with our experts. Find and fix the gaps before a real incident forces your hand.
Conclusion: From Regulatory Burden to Strategic Asset
The best incident response plan does more than check a regulatory box. It knits together law, technology, and clear human processes into a capability that is proven, tested, and understood at all levels. It transforms a reactive, stressful event into a predictable, manageable process.
With Clarysec’s toolkits, including the Zenith Controls and Zenith Blueprint, your IRP evolves from a paper exercise to a living defense-one that can confidently answer the board, the auditor, and, when lightning strikes, the regulator’s call at 2:13 a.m.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council