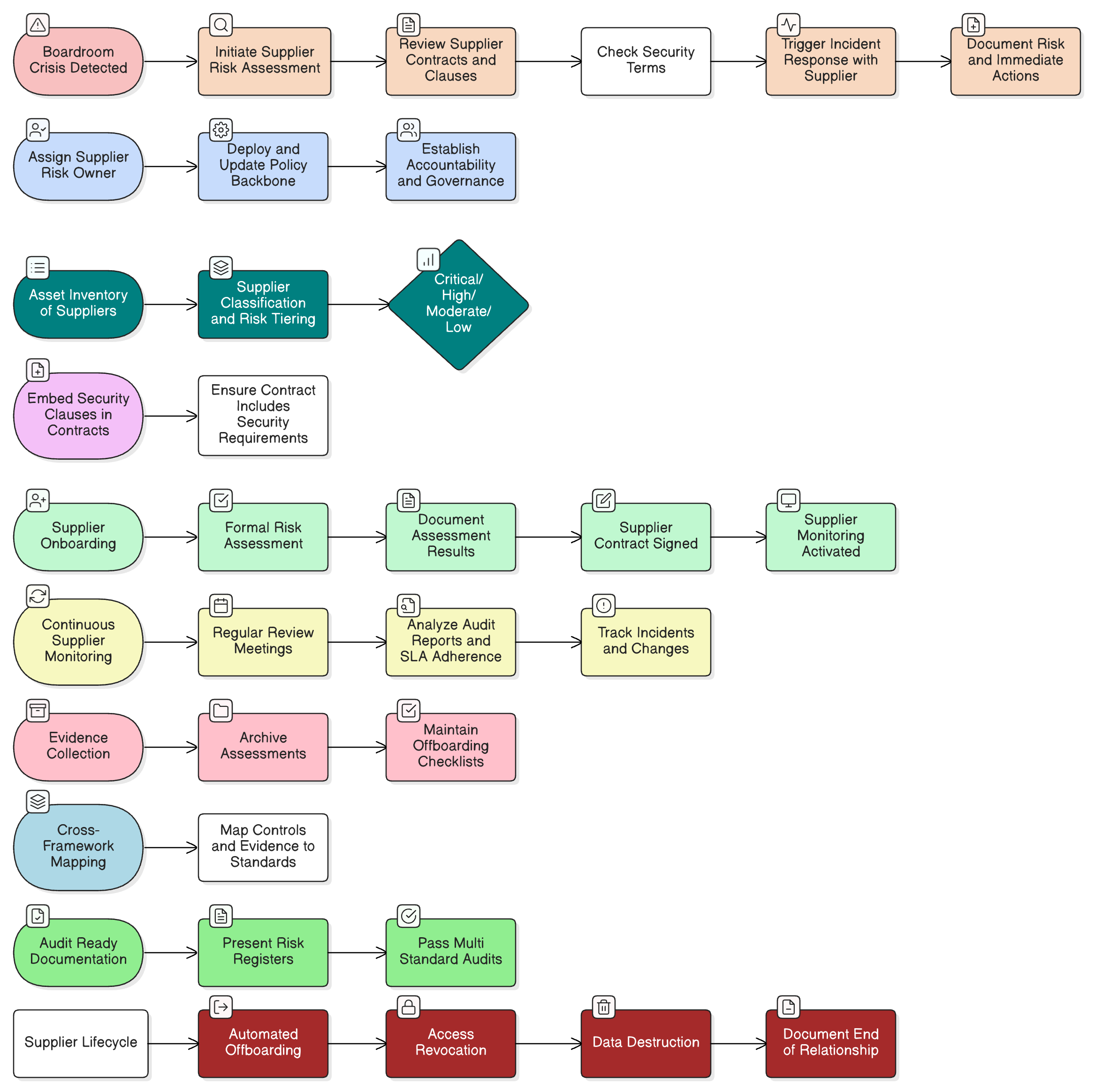
Building a Resilient and Audit-Proof Supplier Risk Program: ISO/IEC 27001:2022 and the Cross-Compliance Roadmap
A comprehensive guide to operationalizing supplier risk management, from boardroom crises to cross-framework audit triumphs, using real-world scenarios, Clarysec’s Zenith toolkits, and actionable blueprints that secure the supply chain throughout its entire lifecycle.