Zenith Blueprint: The Fastest Unified Path to ISO 27001, NIS2, and DORA Compliance
When Compliance Can’t Wait: Inside the 90-Day, Multi-Framework Mandate
At 2AM, your phone buzzes. The board needs ISO 27001:2022 certification in just three months, or your critical European partnership falls apart. At the same time, new NIS2 and DORA regulatory deadlines loom, their requirements stacking on top of already stretched resources. The compliance manager is sprinting, IT leaders express doubts, and the business owner demands proof of real resilience, on paper and in the trenches, well before next quarter’s deal closure.
Meanwhile, in offices across Europe, CISOs like Anya from a scaling FinTech stare at whiteboards littered with three columns: ISO/IEC 27001:2022, NIS2, and DORA. Three control sets, conflicting consultant advice, and budgets at breaking point threaten to fragment every security initiative. How can teams avoid duplicated effort, policy sprawl, and audit fatigue, let alone ensure genuine protection and pass every scrutiny?
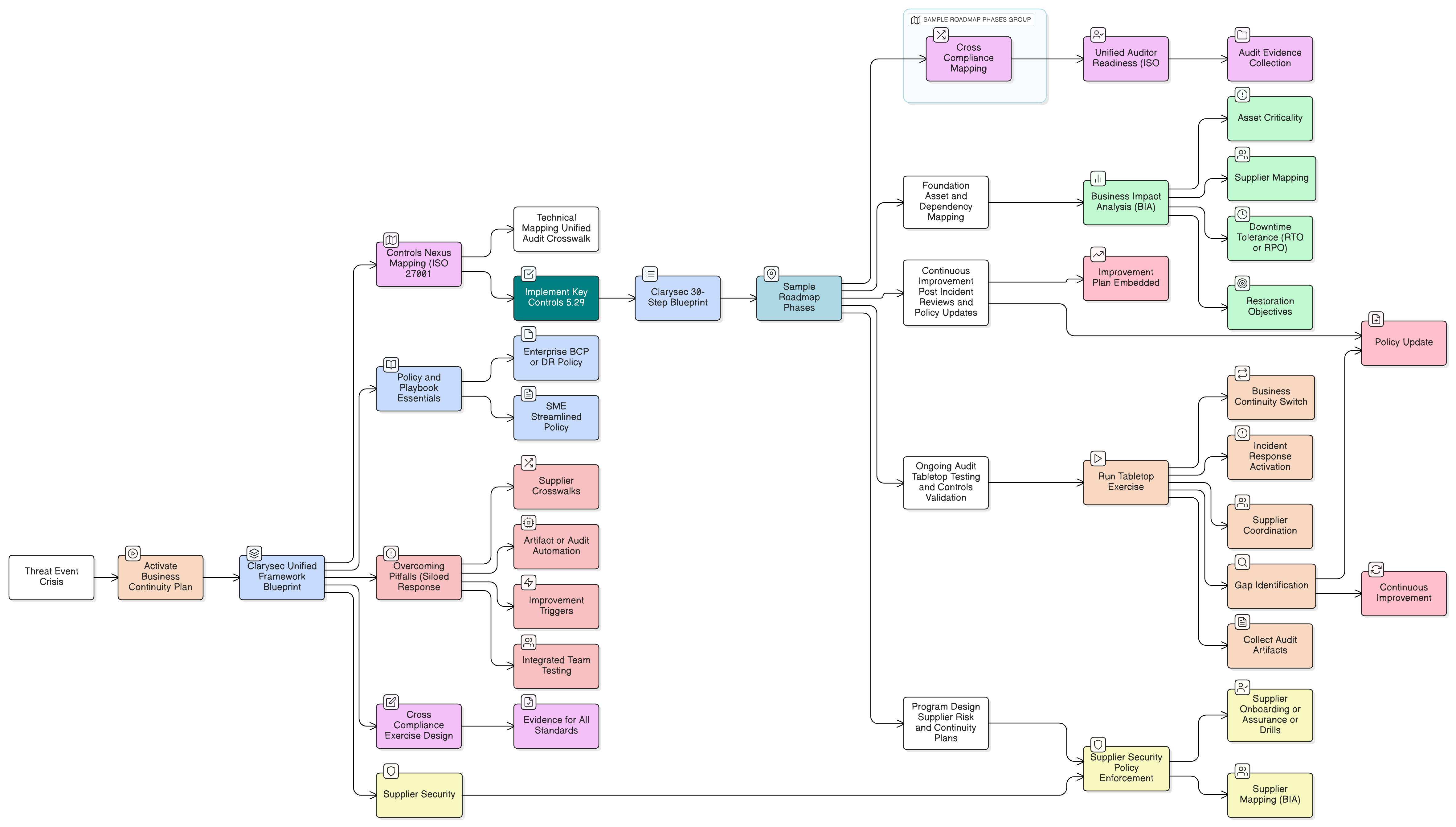
This mounting pressure is now the new normal. The convergence of these frameworks, a true compliance trifecta, demands a smarter approach. It calls for a strategy that blends speed with rigor, aligning not just documents but operational evidence, policy, and controls. This is where Clarysec’s Zenith Blueprint steps in: a 30-step, cross-mapped methodology born from auditor expertise, mapped in real time to Zenith Controls and policy kits that stand up to any audit, regulatory, or client test.
Let’s walk through the complete playbook, woven from the best field stories, hard-won lessons, and actionable guidance from real-world implementations.
The Business Problem: Siloed Compliance Projects Are a Recipe for Failure
When multiple mandates collide, the knee-jerk response is to run parallel projects. One stream for ISO 27001, another for NIS2, yet another for DORA, each with its own spreadsheets, risk registers, and policy libraries. What follows is wasteful redundancy:
- Redundant risk assessments producing conflicting results.
- Duplicate controls laboriously re-implemented for every framework.
- Policy chaos, contradictory docs impossible to maintain or evidence.
- Audit fatigue, multiple cycles draining resources from real operations.
This approach burns budgets and morale, and ultimately risks failed audits and missed business opportunities.
Clarysec’s Zenith Blueprint was created to solve this, enabling leaders to navigate the maze as a single, unified journey toward organizational resilience. It’s not just a checklist; it’s a visually mapped, rigorously referenced operational framework that aligns every requirement, eliminates busywork, and translates security into business advantage.
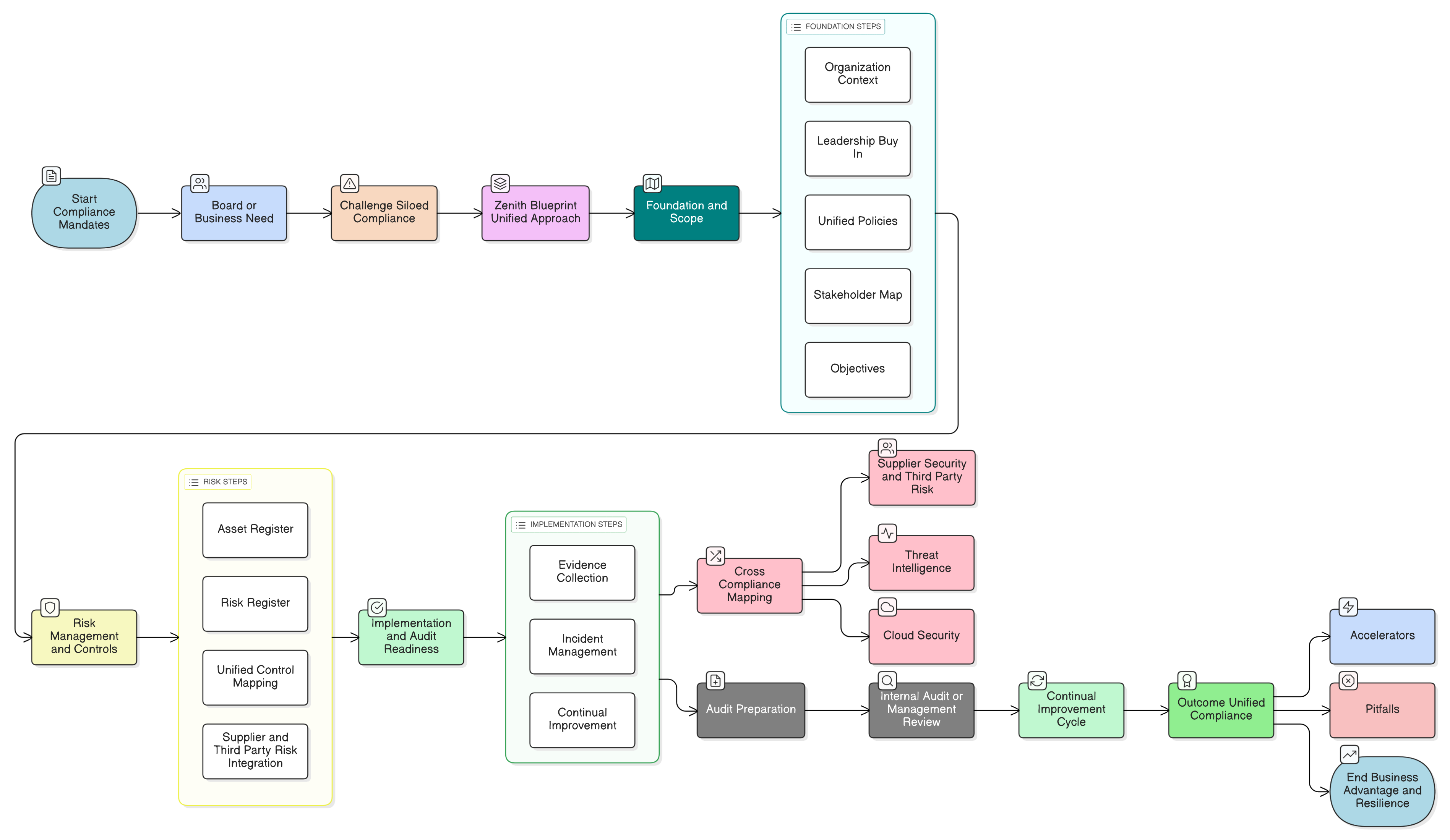
The Zenith Blueprint: A Unified Roadmap
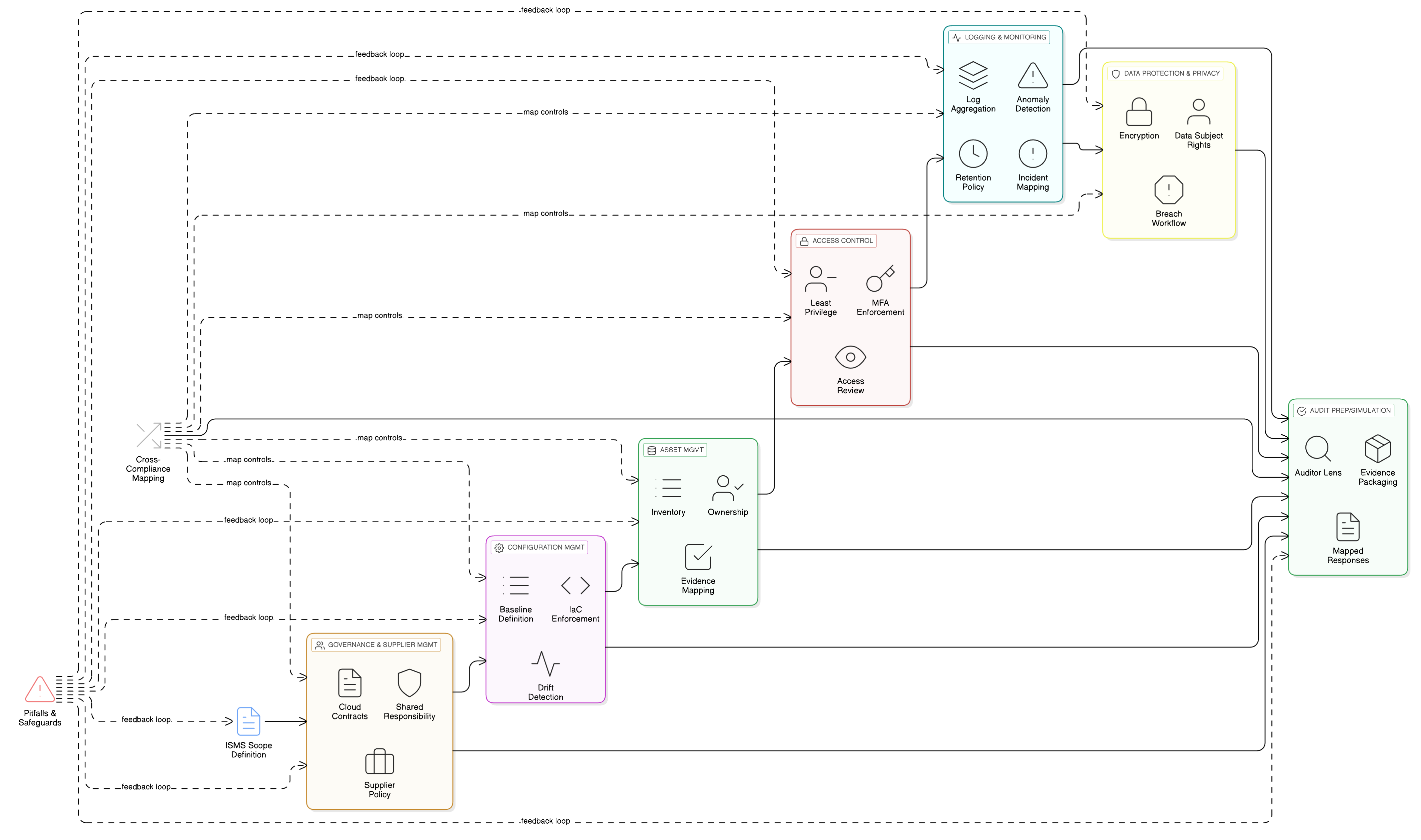
Achieving unified compliance starts with solid foundations and clear, actionable phases. The Zenith Blueprint guides teams through a proven sequence, each step mapped directly to ISO/IEC 27001:2022, NIS2, and DORA requirements, with overlays for GDPR, NIST, and COBIT to future-proof your compliance journey.
Phase 1: Foundation and Scope, No More Siloed Starts
Steps 1-5: Organizational context, leadership buy-in, unified policy framework, stakeholder mapping, objective setting.
Rather than defining the ISMS scope narrowly for ISO alone, the Zenith Blueprint demands up-front inclusion of NIS2’s critical services and DORA’s ICT systems. The kickoff is not just a formality; it secures explicit management commitment to integrated compliance. The result is a single source of truth and a unified project plan your entire organization can rally behind.
Reference: See Clause 4.1 in Clarysec’s Information security policy:
“To protect the organization’s information assets from all threats, whether internal or external, deliberate or accidental.”
Supporting policies then address DORA and NIS2 specifics, all anchored to this master policy.
Phase 2: Risk Management and Controls, One Engine, Multiple Outcomes
Steps 6-15: Asset and risk registers, unified control mapping, supplier and third-party risk integration.
Instead of redundant risk processes, Zenith Blueprint overlays compliance obligations, ensuring the risk methodology satisfies ISO’s rigor, NIS2’s operational requirements, and DORA’s ICT risk specificity. Tools like asset registries and supplier risk matrices are designed once, mapped everywhere.
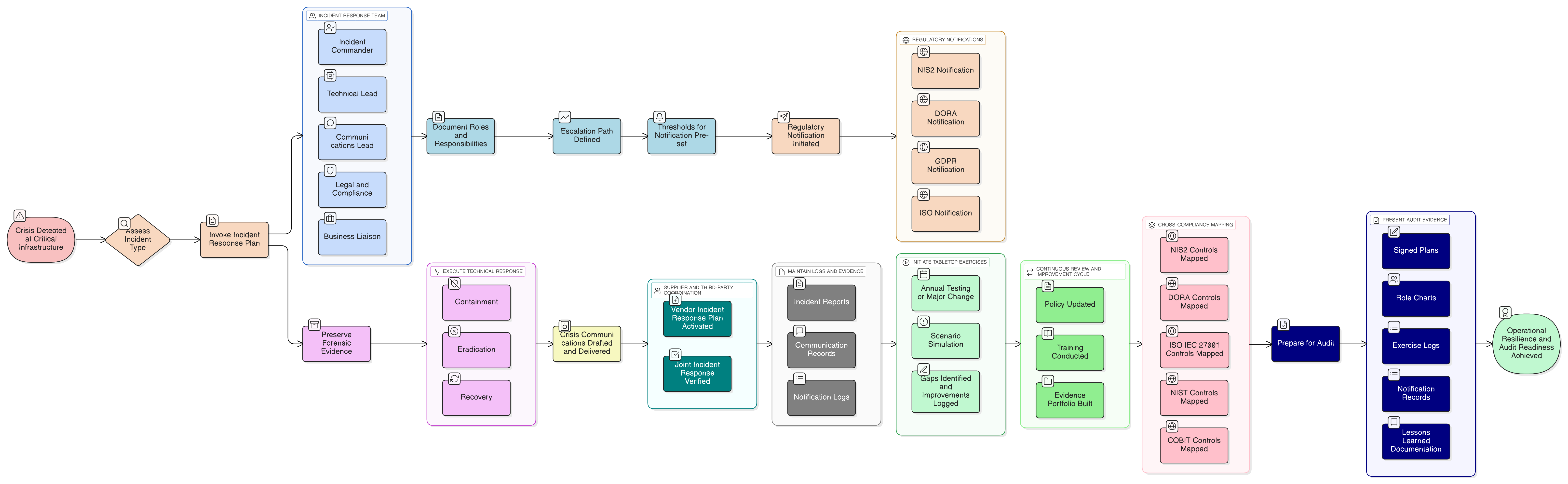
Phase 3: Implementation, Evidence, and Audit Readiness, Proof Beyond Paper
Steps 16-30: Implementation tracking, control operation, incident management, evidence preparation, continual improvement.
This is where the Blueprint’s true value emerges: audit-ready templates, mapped policies, and evidence required by ISO, NIS2, and DORA, cross-referenced so nothing falls through the cracks, no matter the audit lens.
Cross-Compliance Mapping: Zeroing in on Overlapping Controls
Clarysec’s Zenith Controls is not just a control list, it is a deep, relational mapping engine aligning every control to regulatory clauses, supporting standards, and practical audits.
Let’s break down how this works for the most demanding areas:
1. Supplier Security and Third-Party Risk
ISO 27001:2022 addresses supplier security under Annex A and Clause 6.1.
NIS2 presses on supply chain resilience.
DORA imposes explicit ICT third-party oversight.
Zenith Controls Mapping:
- Links to ISO/IEC 27036 (supplier procedures), ISO/IEC 27701 (privacy contract clauses), and ISO/IEC 27019 (sector supply chain controls).
- Directs you to operational monitoring and resilience checks needed for NIS2/DORA compliance.
- Cites audit methodologies: ISO wants documented supplier evaluation; NIS2 expects capability verification; DORA demands continuous monitoring and aggregation analysis.
Clarysec Third-party and supplier security policy, Section 5.1.2:
“Supplier risk shall be assessed prior to any engagement, documented for evidence, and reviewed at least annually…”
Supplier Compliance Table:
| Requirement | ISO/IEC 27001:2022 | NIS2 | DORA | Clarysec Solution |
|---|---|---|---|---|
| Supplier Evaluation | Document due diligence | Capability assessment | ICT risk analysis, concentration | Zenith Blueprint Steps 8, 12 |
| Contract Clauses | Incident, audit, compliance requirements | Resilience and security terms | Critical dependency, operational terms | Policy templates, Zenith Controls |
| Monitoring | Annual review, incident response | Ongoing performance and logs | Continuous monitoring, incident readiness | Evidence packs, audit prep guide |
2. Threat Intelligence, Mandatory and Cross-Cutting
ISO/IEC 27002:2022 Control 5.7: Collect and analyze threat intelligence. DORA: Article 26 requires threat-led penetration testing (TLPT), informed by real-world threat intelligence. NIS2: Article 21 demands technical and organizational measures, where knowledge of threat landscape is key.
Zenith Controls Insights:
- Integrates this control with incident management planning, monitoring activities, and web filtering.
- Ensures threat intelligence is both a standalone process and a driver of related controls, feeding real-life IoCs into monitoring systems and risk processes.
| Auditor Type | Primary Focus | Key Questions for Threat Intelligence Evidence |
|---|---|---|
| ISO/IEC 27001 Auditor | Process maturity, integration | Show process, connections to risk assessment |
| DORA Auditor | Operational resilience, testing | Show threat data in scenario-based TLPT |
| NIS2 Auditor | Proportional risk management | Show threat-led selection/implementation of controls |
| COBIT/ISACA Auditor | Governance, metrics | Governance structures, effectiveness measurement |
3. Cloud Security, One Policy to Rule Them All
ISO/IEC 27002:2022 Control 5.23: Whole lifecycle cloud security. DORA: Enforces contract, risk, and audit requirements for cloud/ICT providers (Articles 28-30). NIS2: Requires thorough supplier and supply chain security.
Example from Cloud services policy Clause 5.1:
“Before the acquisition or use of any cloud service, the organization shall define and document its specific information security requirements…”
This clause:
- Satisfies the ISO requirement for risk-based use of cloud services.
- Incorporates DORA data location/resilience and audit rights.
- Meets NIS2’s supply chain security demands.
Audit-Ready from Day One: Multi-Lens Audit Preparation
Clarysec’s approach does not just map technical controls, it aligns your entire evidence landscape for different audit and regulatory “lenses”:
- ISO/IEC 27001:2022 auditors: Seek documents, risk records, and process evidence.
- NIS2 reviewers: Focus on operational resilience, incident logs, and supply chain effectiveness.
- DORA auditors: Demand ongoing ICT risk monitoring, concentration analysis, and scenario-based testing.
- COBIT/ISACA: Look for metrics, governance cycles, and continuous improvement.
Zenith Blueprint steps and supporting policy toolkits make it possible to assemble evidence packets that satisfy every type of reviewer, eliminating the scramble, the stress, and the dreaded “find more evidence” requests.
Real-World Scenario: 90 Days to Triple Compliance
Picture a European fintech scaling for critical infrastructure clients. Using Zenith Blueprint, these are the milestones:
- Weeks 1-2: Unified ISMS context (Steps 1-5), including business-critical NIS2 assets and DORA ICT systems.
- Weeks 3-4: Map and update policies using tagged templates: Third-party and supplier security policy, Asset classification and management policy, and Cloud services policy.
- Weeks 5-6: Run comprehensive, cross-standard risk and asset assessments using Zenith Controls guides.
- Weeks 7-8: Operationalize controls, track implementation, and log real evidence.
- Weeks 9-10: Conduct audit-readiness review, aligning packets for ISO, NIS2, and DORA audits.
- Weeks 11-12: Hold mock audits and workshops, refine evidence, and get final stakeholder buy-in.
Result: Certification and regulatory confidence, on paper, in systems, and in executive meetings.
Closing Gaps: Pitfalls and Accelerators
Pitfalls to Avoid:
- Incomplete asset or supplier registers.
- Policies with no living operational evidence or logs.
- Missing or mismatched contract clauses for supplier risk.
- Controls mapped only for ISO, not NIS2/DORA resilience needs.
- Stakeholder disengagement or confusion around roles.
Zenith Blueprint Accelerators:
- Integrated tracking for assets, suppliers, contracts, and evidence.
- Policy repositories tagged to every control and standard.
- Audit packets that anticipate and fulfill multi-regulatory demands.
- Continual monitoring and improvement embedded in workflows.
Continual Improvement: Keeping Compliance Living
With the Zenith Blueprint and Zenith Controls, unified compliance is not a one-off chore; it’s a living cycle. Internal audits and management reviews are designed to check against every active regulatory requirement, not just ISO. As frameworks evolve (NIS3, DORA updates), Clarysec’s methodology flexes with them, so your ISMS evolves too.
Clarysec’s continual improvement phases ensure:
- Every review incorporates DORA resilience tests, NIS2 incident analytics, and new audit findings.
- Leadership always sees the holistic risk and compliance picture.
- Your ISMS never gets stuck or outdated.
Your Next Steps: Turn Compliance Headaches Into Business Advantage
Anya’s initial panic transforms to clarity as her team adopts a cross-mapped, unified approach. Your organization can do the same, no more disconnected compliance projects, broken policies, or endless audits. Clarysec’s Zenith Blueprint, Zenith Controls, and policy kits offer the fastest, most repeatable path to full, audit-ready resilience.
Action Items:
- Download and Review: Explore the full Zenith Blueprint: An Auditor’s 30-Step Roadmap.
- Cross-Map Your Controls: Leverage Zenith Controls: The Cross-Compliance Guide.
- Accelerate with Policy Kits: Deploy internal controls and policies like Information security policy, Third-party and supplier security policy, and Cloud services policy.
Ready to make compliance a force multiplier for security, revenue, and resilience? Contact Clarysec for a tailored walk-through, policy demo, or audit prep session. Unlock the fastest, most unified route to ISO 27001:2022, NIS2, and DORA compliance.
References
- Zenith Blueprint: An Auditor’s 30-Step Roadmap
- Zenith Controls: The Cross-Compliance Guide
- Third-party and supplier security policy
- Asset classification and management policy
- Cloud services policy
- Information security policy
- ISO/IEC 27001:2022
- NIS2 Directive
- DORA Regulation
- GDPR
- COBIT 19
- BS EN ISO-IEC 27006-1:2024
Clarysec: Where unified compliance drives true resilience, and every audit fuels your next competitive leap.
Frequently Asked Questions
About the Author

Igor Petreski
Compliance Systems Architect, Clarysec LLC
Igor Petreski is a cybersecurity leader with over 30 years of experience in information technology and a dedicated decade specializing in global Governance, Risk, and Compliance (GRC).Core Credentials & Qualifications:• MSc in Cyber Security from Royal Holloway, University of London• PECB-Certified ISO/IEC 27001 Lead Auditor & Trainer• Certified Information Systems Auditor (CISA) from ISACA• Certified Information Security Manager (CISM) from ISACA • Certified Ethical Hacker from EC-Council