#Compliance
Articles tagged with "Compliance"
8 articles
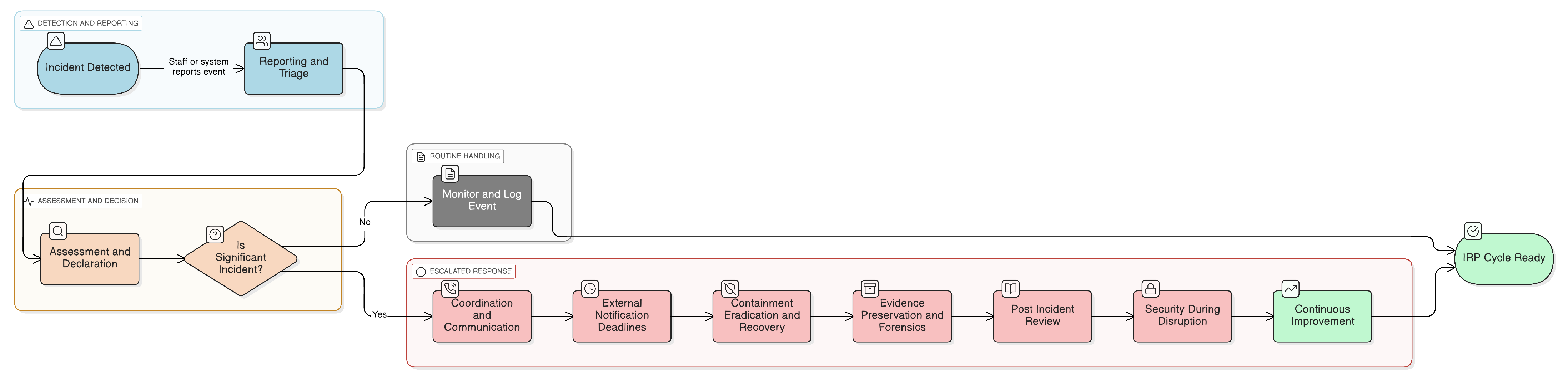
The NIS2 Directive’s 24-hour notification rule is a game-changer. This definitive guide shows CISOs and auditors how to engineer a resilient, compliant incident response plan that stands up to regulatory scrutiny and real-world attacks, using Clarysec’s policies and cross-compliance toolkits.
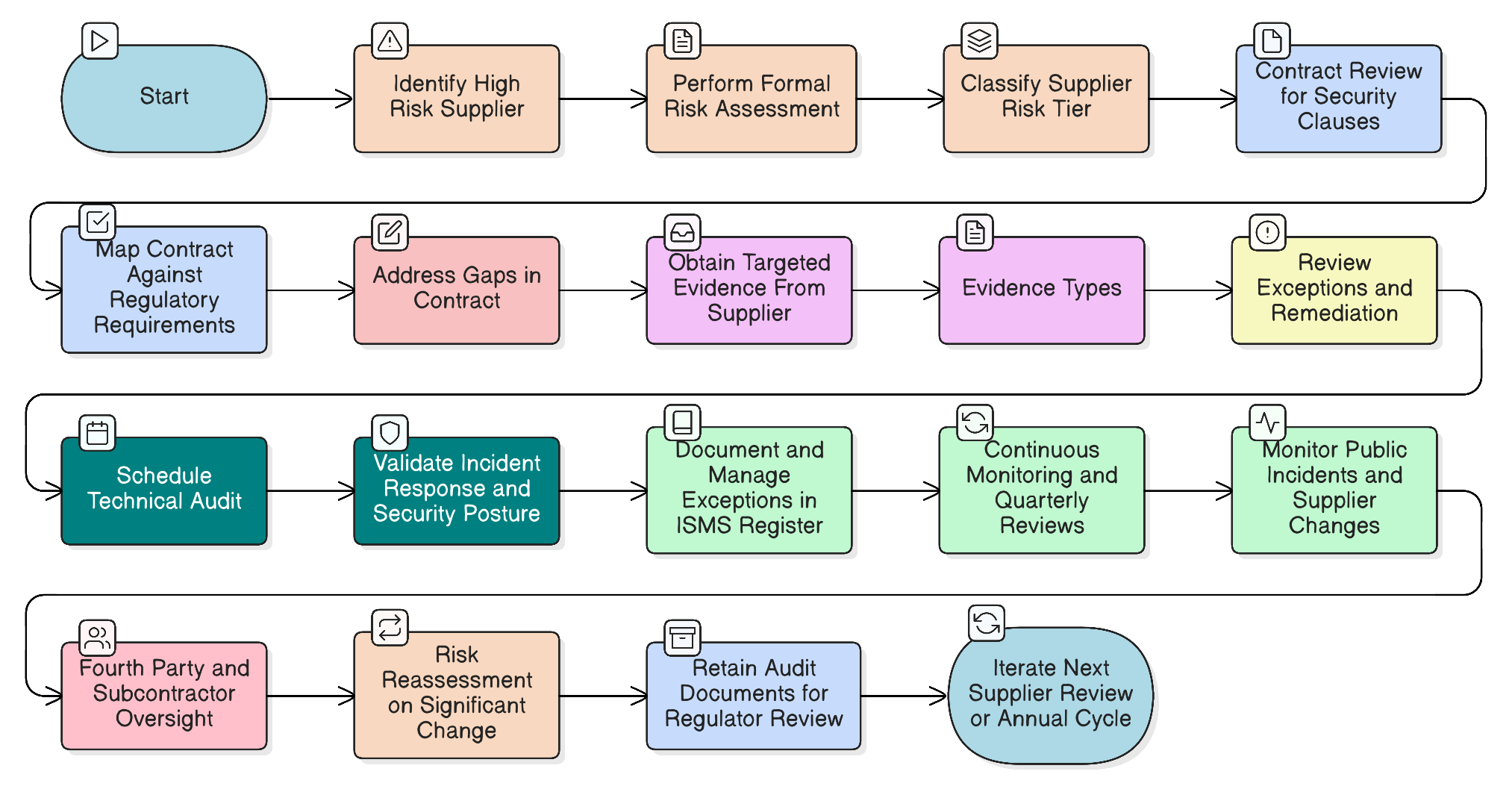
Our flagship article for CISOs on mastering high-risk supplier audits for NIS2 and DORA. Learn how to implement a risk-based, continuous audit strategy leveraging proven frameworks, policy mandates, and actionable checklists to satisfy stringent regulatory demands.
This flagship article walks CISOs and compliance leaders through a real-world approach to building a NIS2-compliant supply chain risk program. It combines regulatory insights, actionable controls, and Clarysec’s expert guidance to turn your supply chain from a critical vulnerability into a resilient, auditable asset.
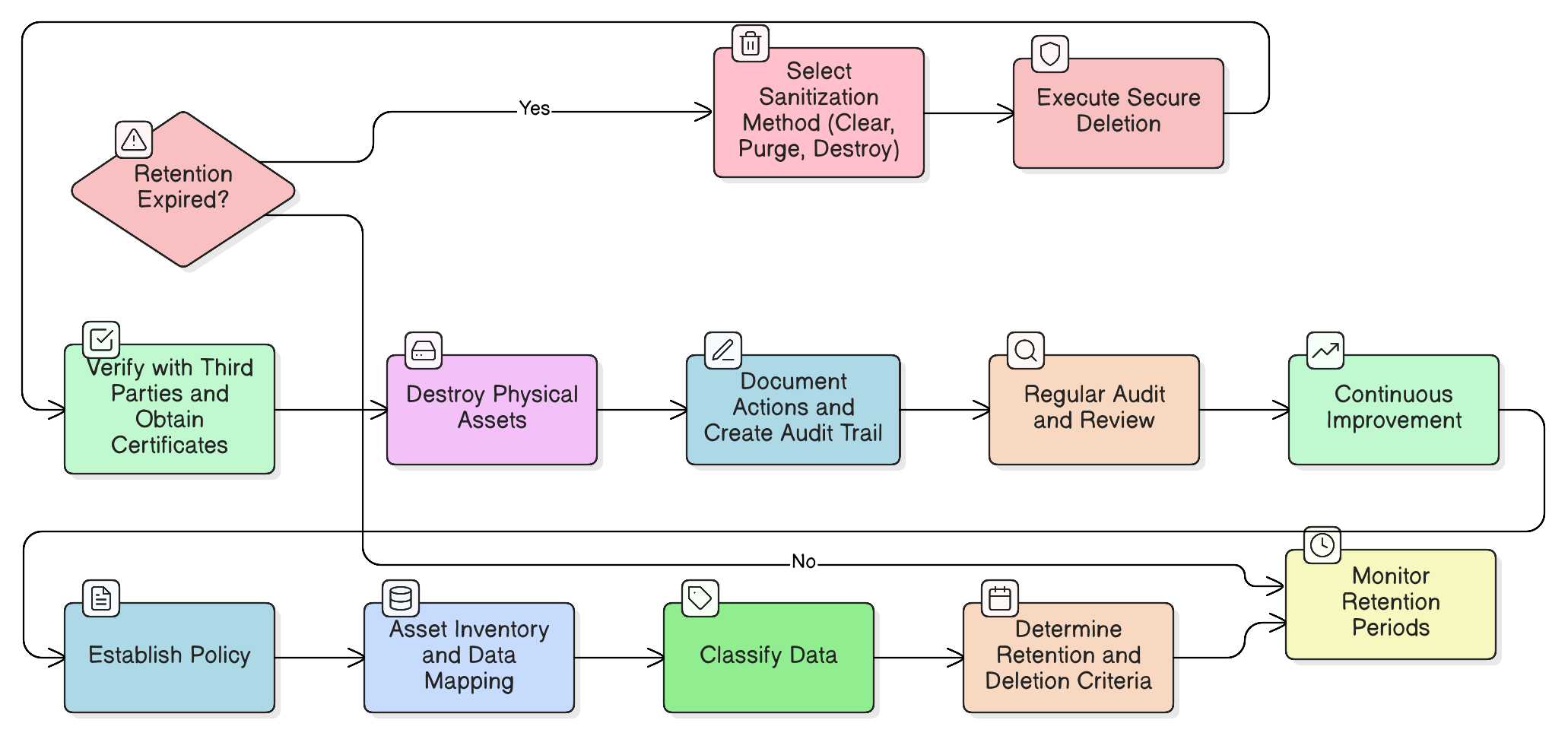
Transform your legacy data risk into a strategic advantage. This in-depth guide covers everything from policy creation and media sanitization to building an audit-proof trail for data disposal, combining Clarysec’s expert roadmaps and policy toolkits.
The EU’s NIS2 Directive and DORA Regulation are transforming cybersecurity compliance. This guide breaks down their impact and provides a practical path to readiness.
A practical guide for CISOs and SME owners on building a robust phishing resilience program aligned with ISO 27001:2022, NIS2, and DORA requirements.
Learn how implementing an ISO/IEC 27001:2022 ISMS provides a robust framework that directly addresses the core cybersecurity requirements of the NIS2 Directive.
Learn how to build a measurable phishing resilience program using ISO 27001:2022 controls A.6.3 and A.6.4 to reduce human risk and prove compliance.