#Data Protection
Articles tagged with "Data Protection"
14 articles
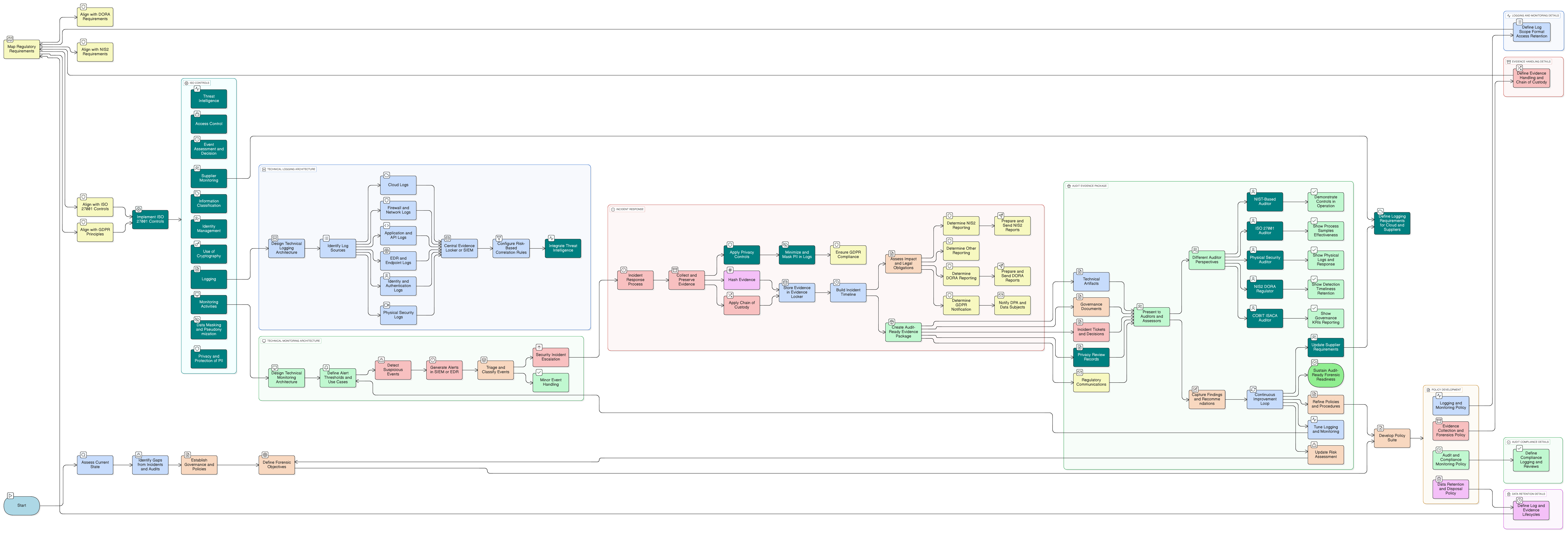
This comprehensive article provides a scenario-driven guide for CISOs on establishing a forensic readiness capability that meets stringent regulatory and audit demands across NIS2, DORA, ISO 27001, and GDPR.
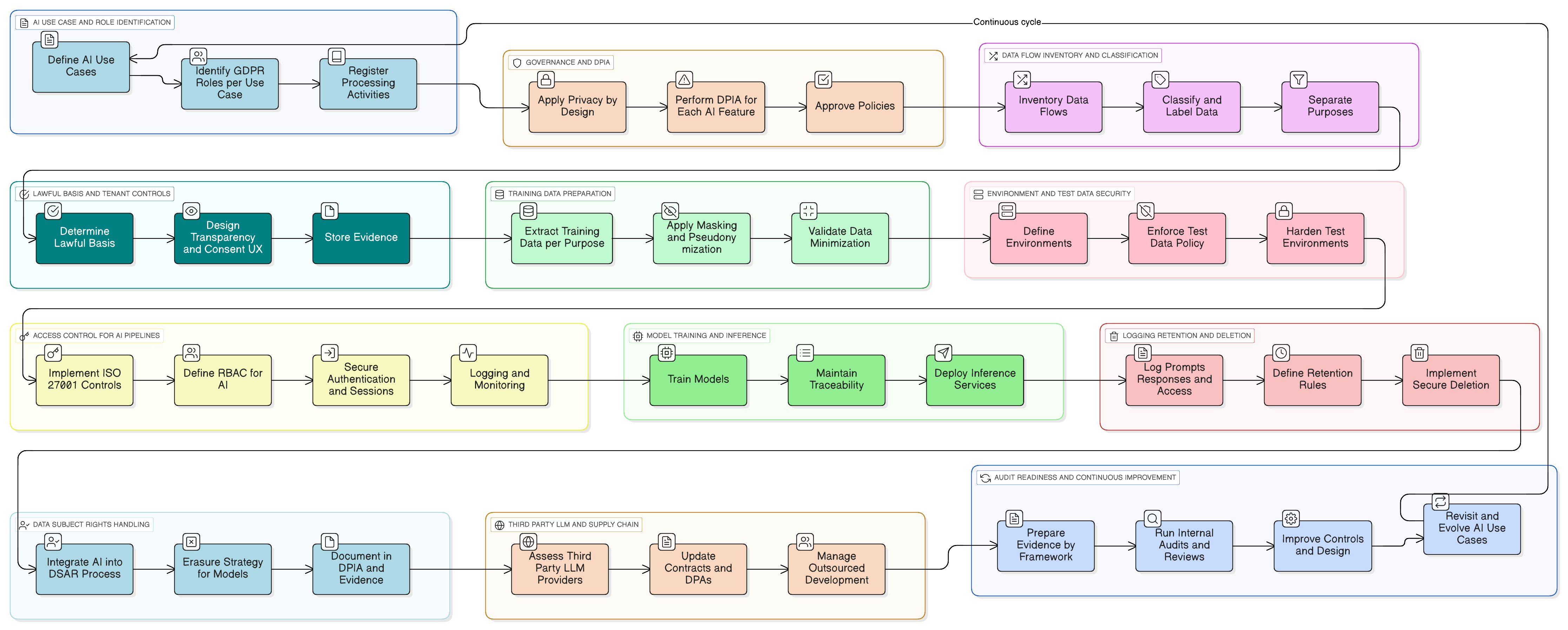
This article provides a practical playbook for CISOs to navigate the complex intersection of GDPR and AI. We offer a scenario-driven walkthrough for making SaaS products with LLMs compliant, focusing on training data, access controls, data subject rights, and multi-framework audit readiness.
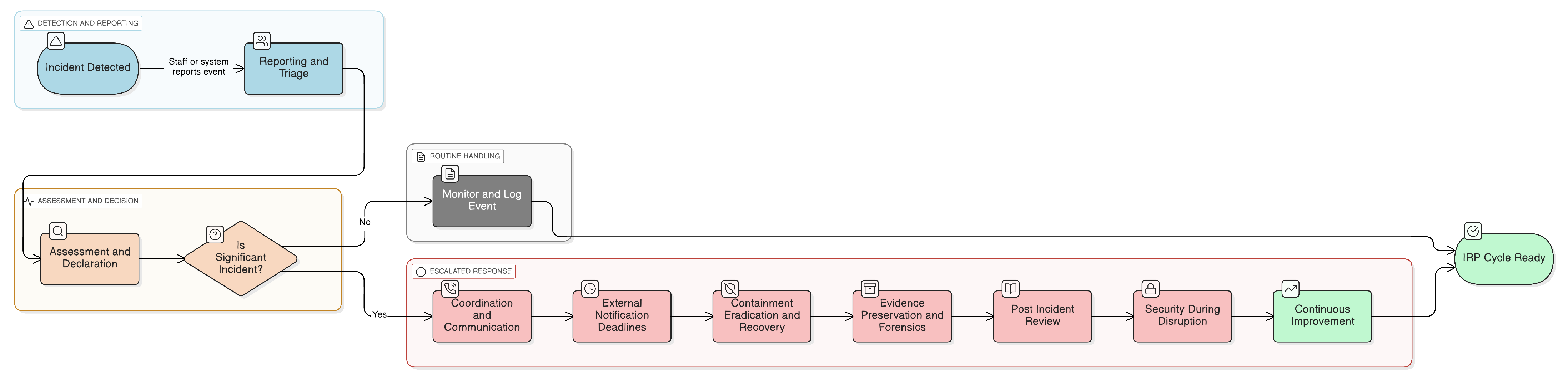
The NIS2 Directive’s 24-hour notification rule is a game-changer. This definitive guide shows CISOs and auditors how to engineer a resilient, compliant incident response plan that stands up to regulatory scrutiny and real-world attacks, using Clarysec’s policies and cross-compliance toolkits.
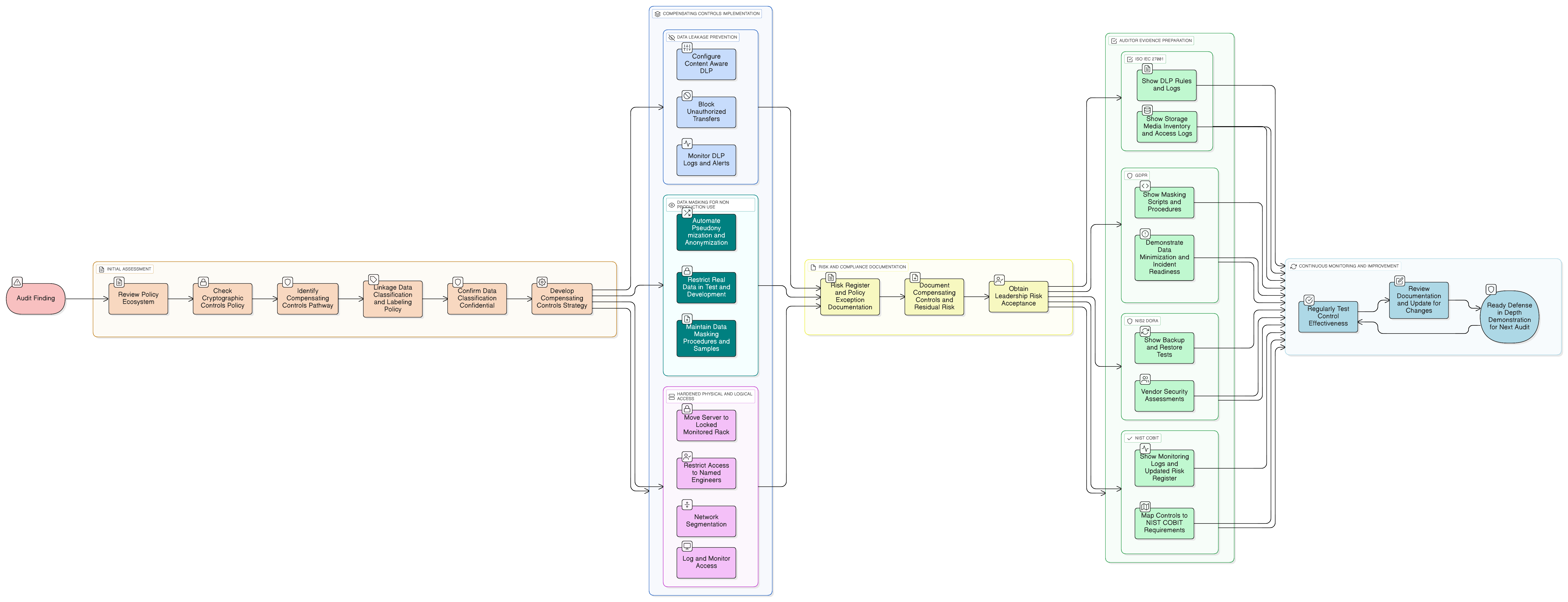
A practical guide for CISOs on implementing and documenting compensating controls for data at rest when encryption isn’t feasible. We walk through a real-world audit scenario, mapping layered defenses to ISO/IEC 27001:2022, GDPR, NIS2, DORA, and NIST frameworks.
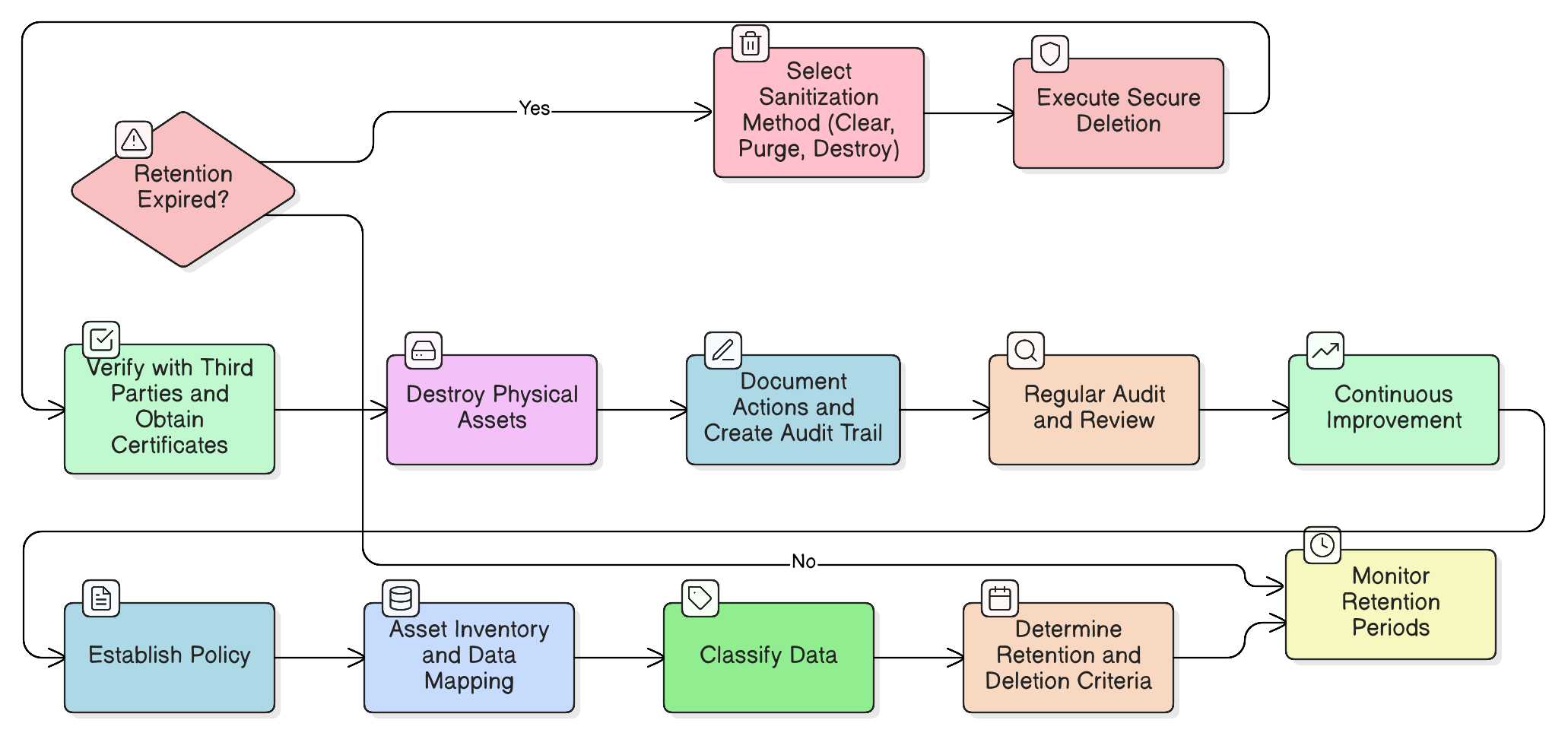
Transform your legacy data risk into a strategic advantage. This in-depth guide covers everything from policy creation and media sanitization to building an audit-proof trail for data disposal, combining Clarysec’s expert roadmaps and policy toolkits.
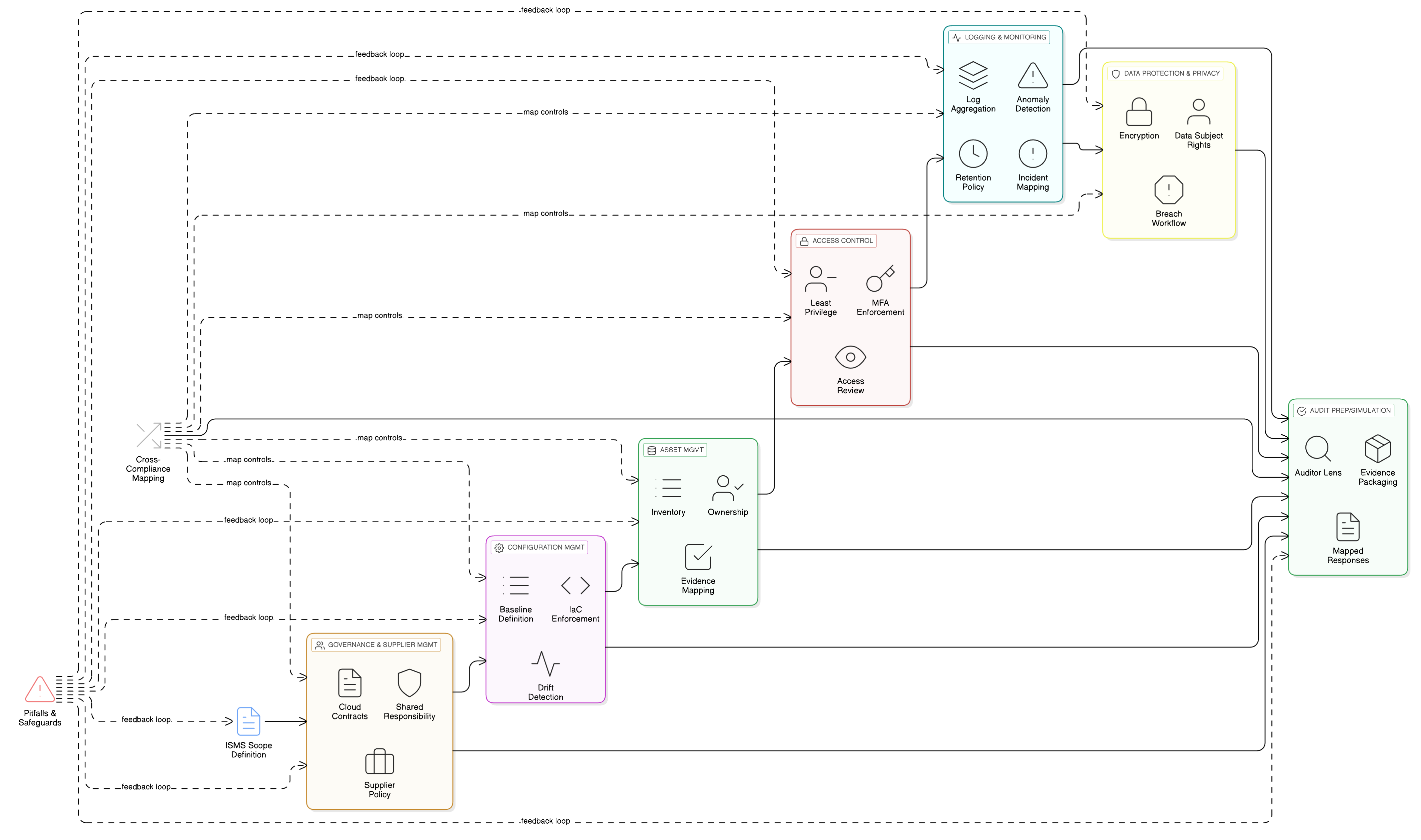
CISOs, compliance managers, and cloud architects: discover how to operationalize ISO 27001:2022 cloud controls for perpetual compliance. Real-world stories, technical mapping tables, and actionable blueprints from Clarysec unite security, governance, and audit-readiness across frameworks.
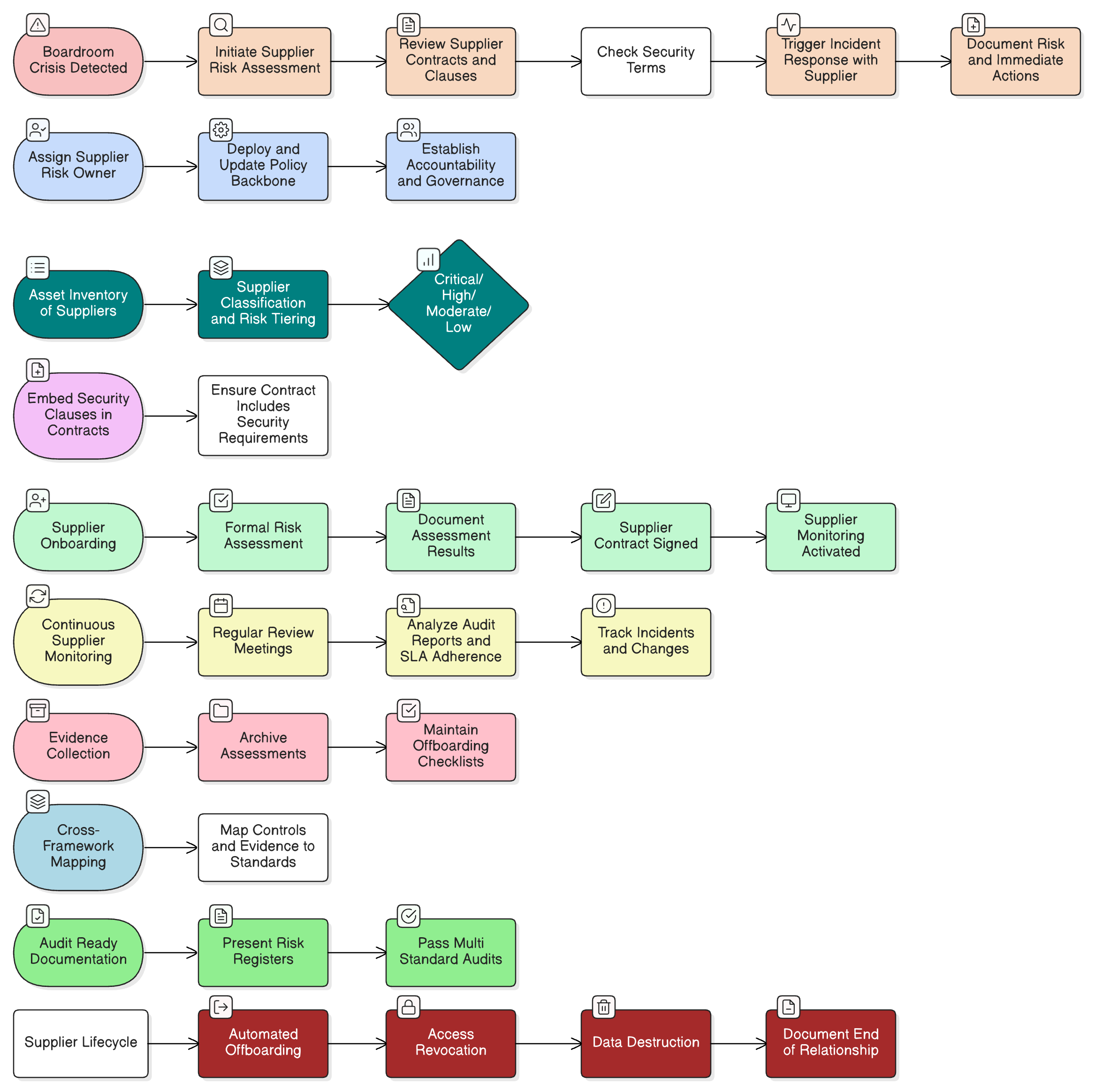
A comprehensive guide to operationalizing supplier risk management, from boardroom crises to cross-framework audit triumphs, using real-world scenarios, Clarysec’s Zenith toolkits, and actionable blueprints that secure the supply chain throughout its entire lifecycle.
Uncover the truth behind the top 7 GDPR myths of 2025. Our expert guide debunks common misconceptions about consent, data breaches, and compliance.
A practical guide for CISOs and SME owners on building a robust phishing resilience program aligned with ISO 27001:2022, NIS2, and DORA requirements.