#Incident Response
Articles tagged with "Incident Response"
15 articles
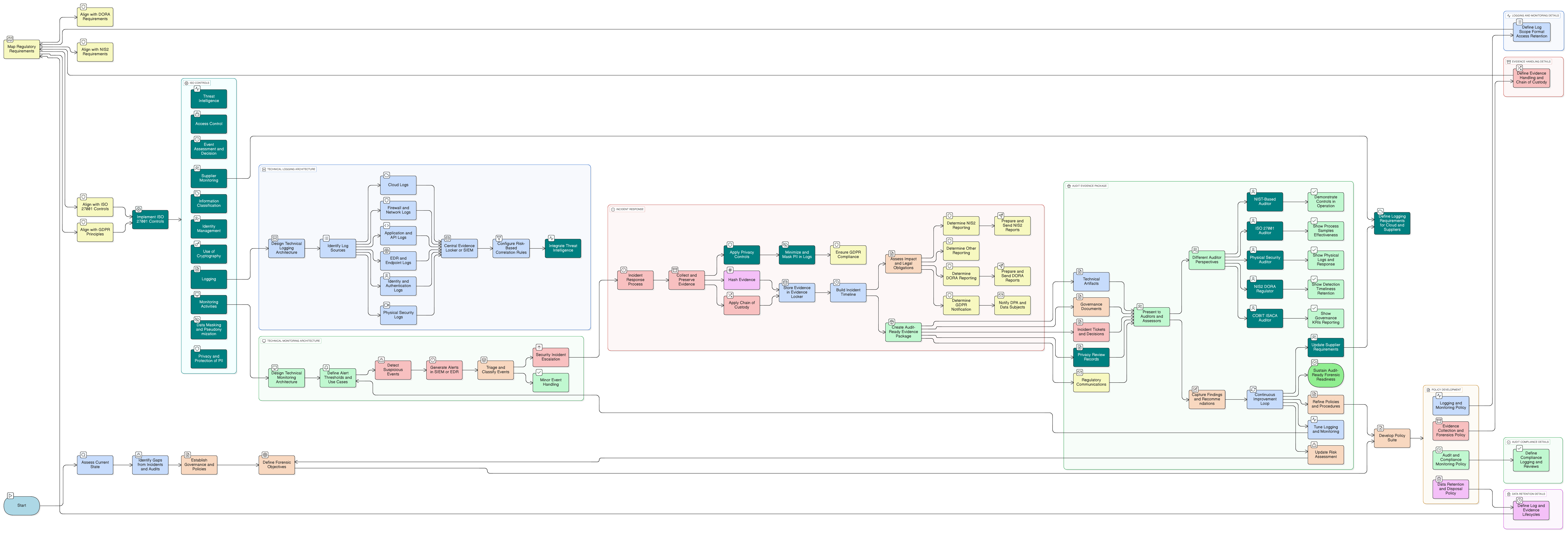
This comprehensive article provides a scenario-driven guide for CISOs on establishing a forensic readiness capability that meets stringent regulatory and audit demands across NIS2, DORA, ISO 27001, and GDPR.
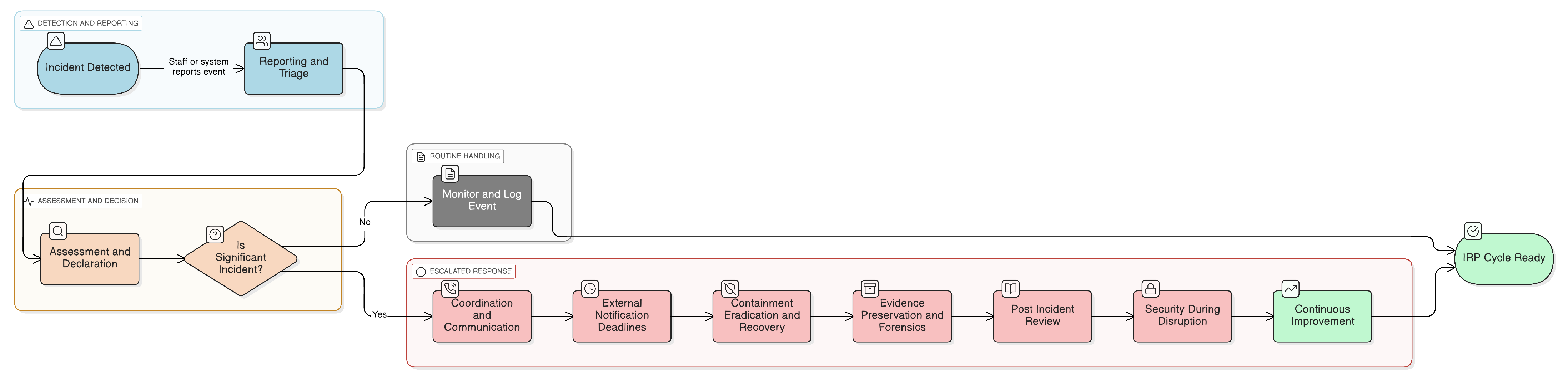
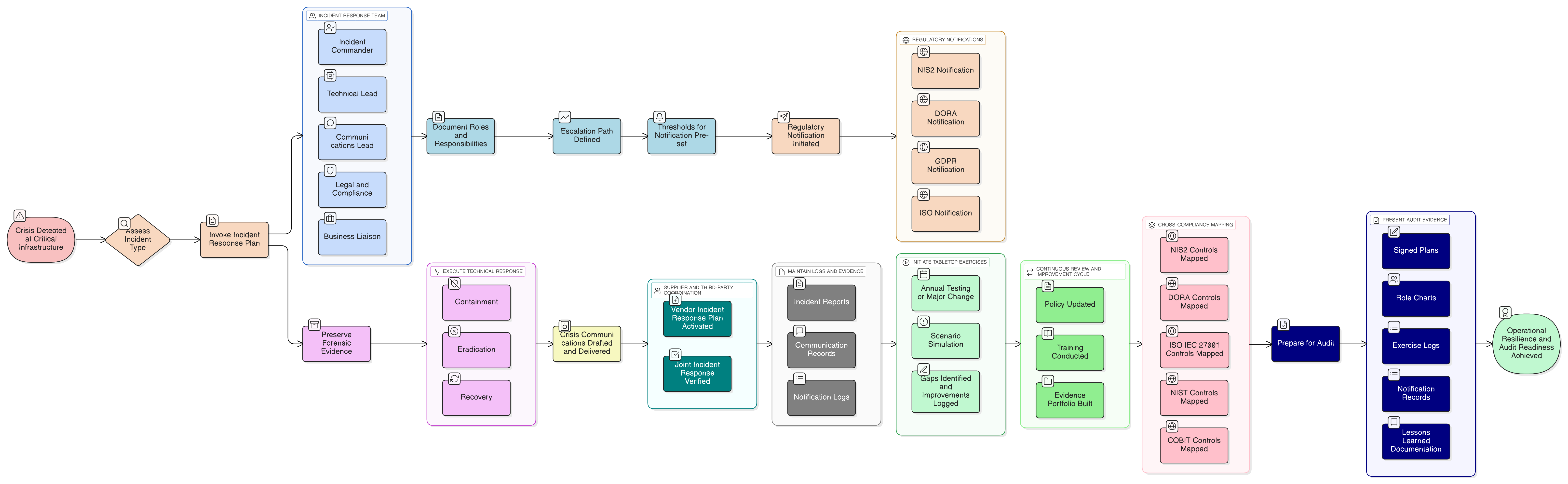
The NIS2 Directive’s 24-hour notification rule is a game-changer. This definitive guide shows CISOs and auditors how to engineer a resilient, compliant incident response plan that stands up to regulatory scrutiny and real-world attacks, using Clarysec’s policies and cross-compliance toolkits.
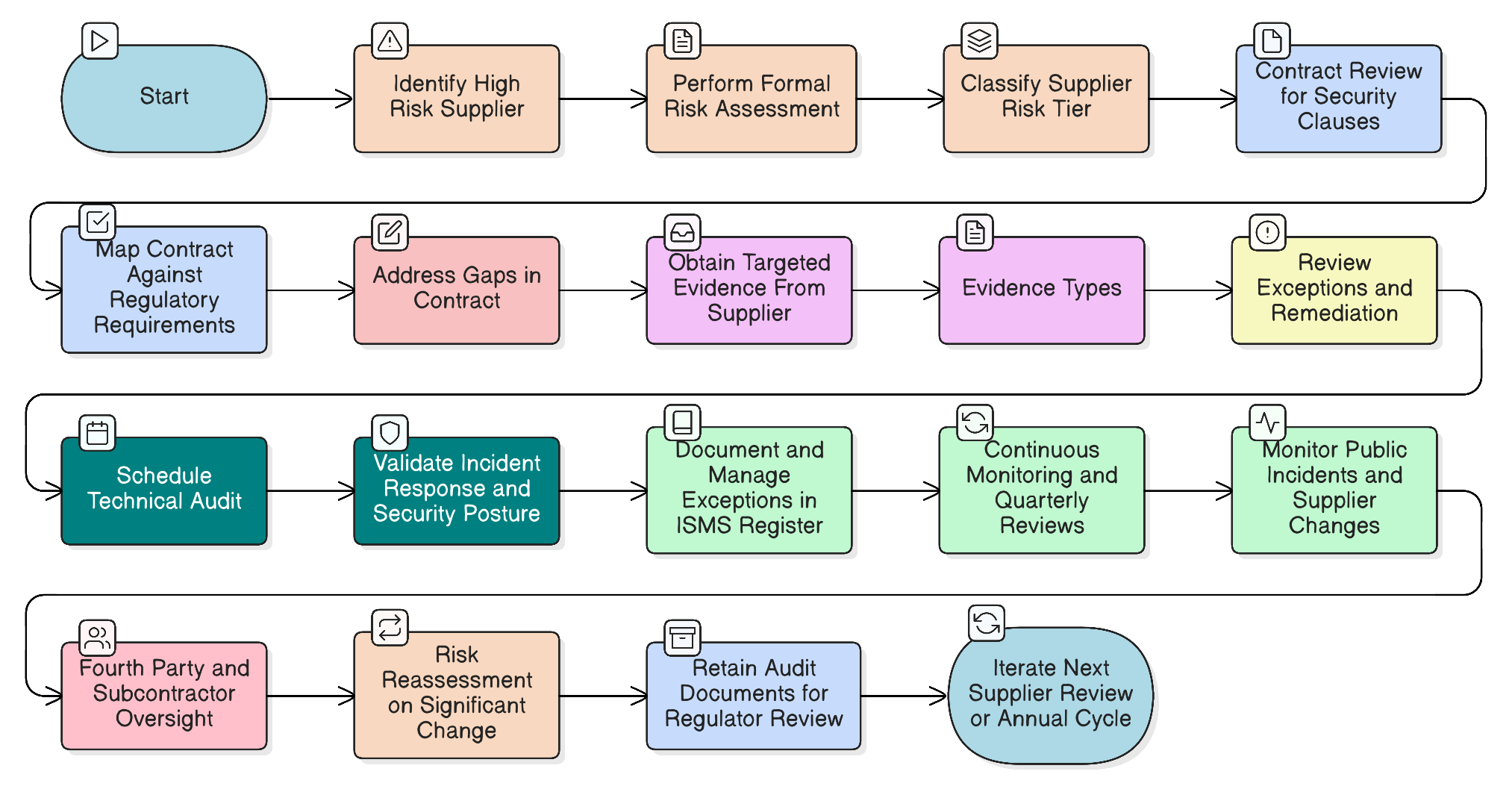
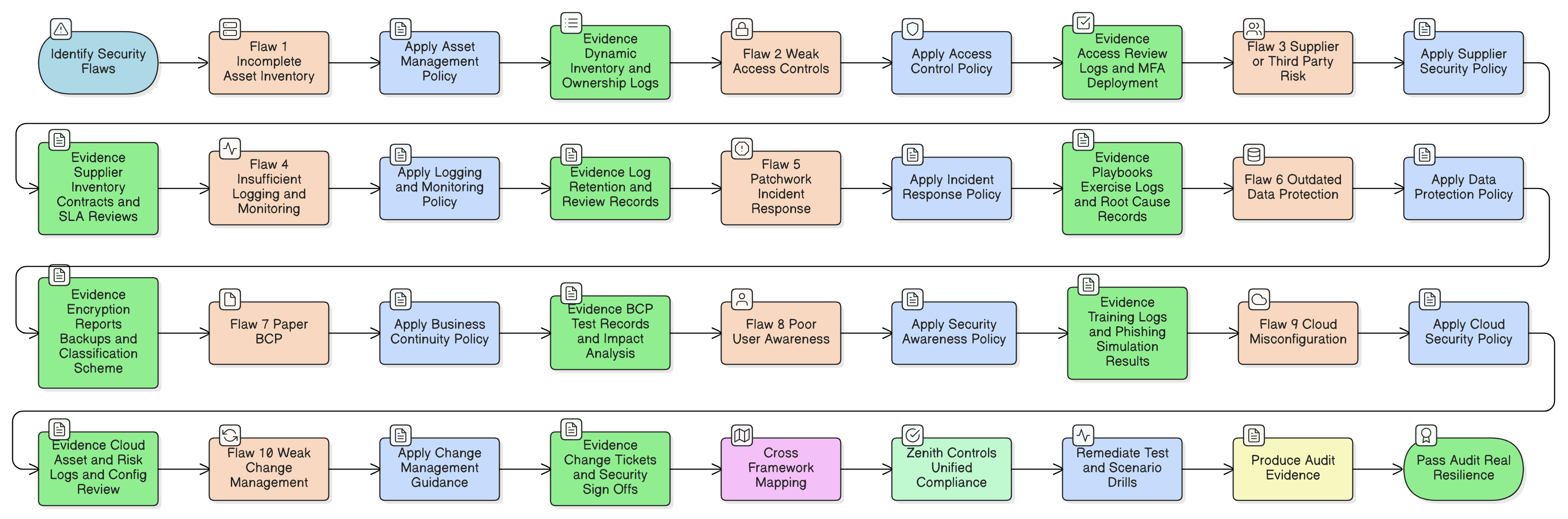
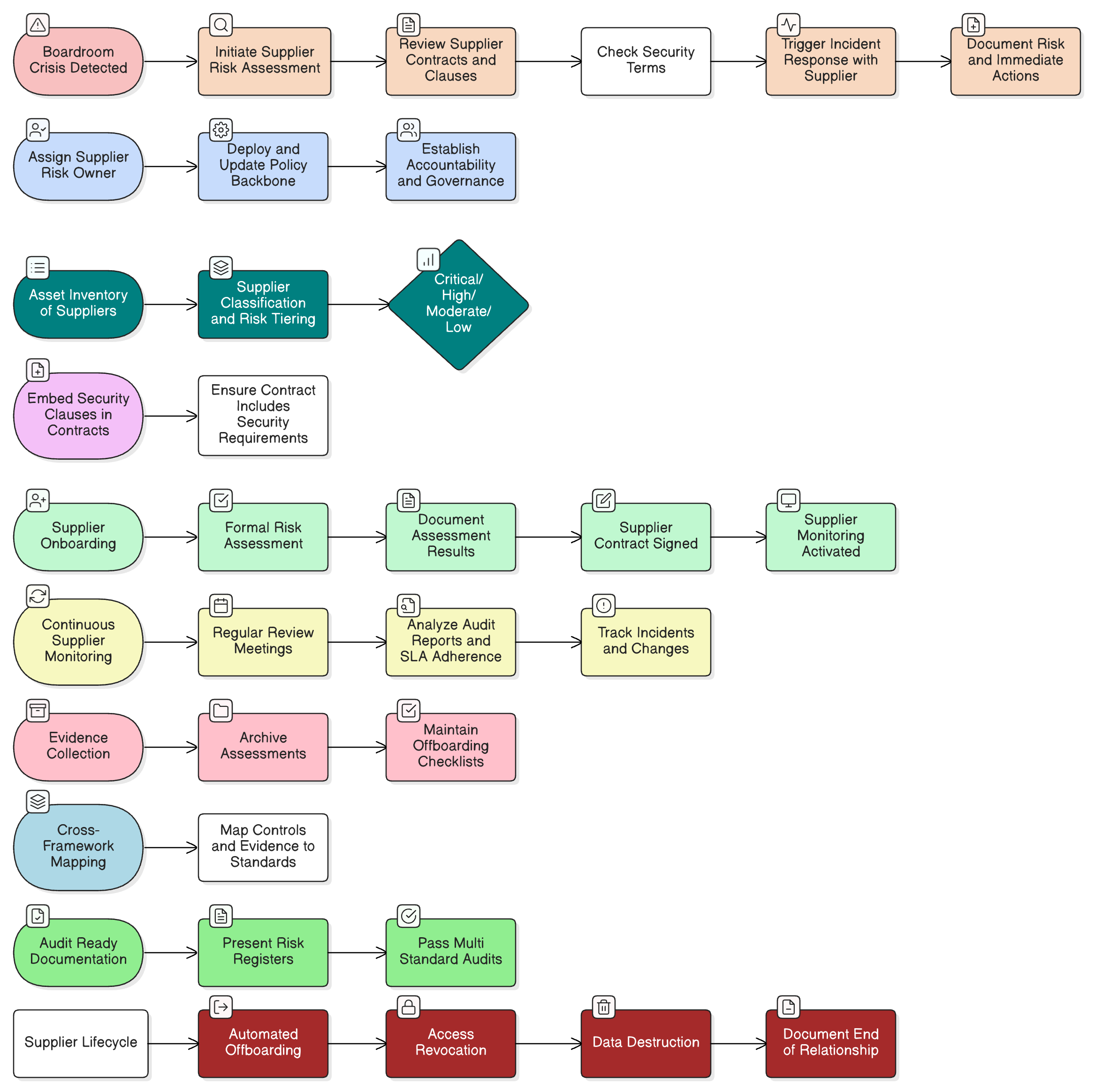
Our flagship article for CISOs on mastering high-risk supplier audits for NIS2 and DORA. Learn how to implement a risk-based, continuous audit strategy leveraging proven frameworks, policy mandates, and actionable checklists to satisfy stringent regulatory demands.
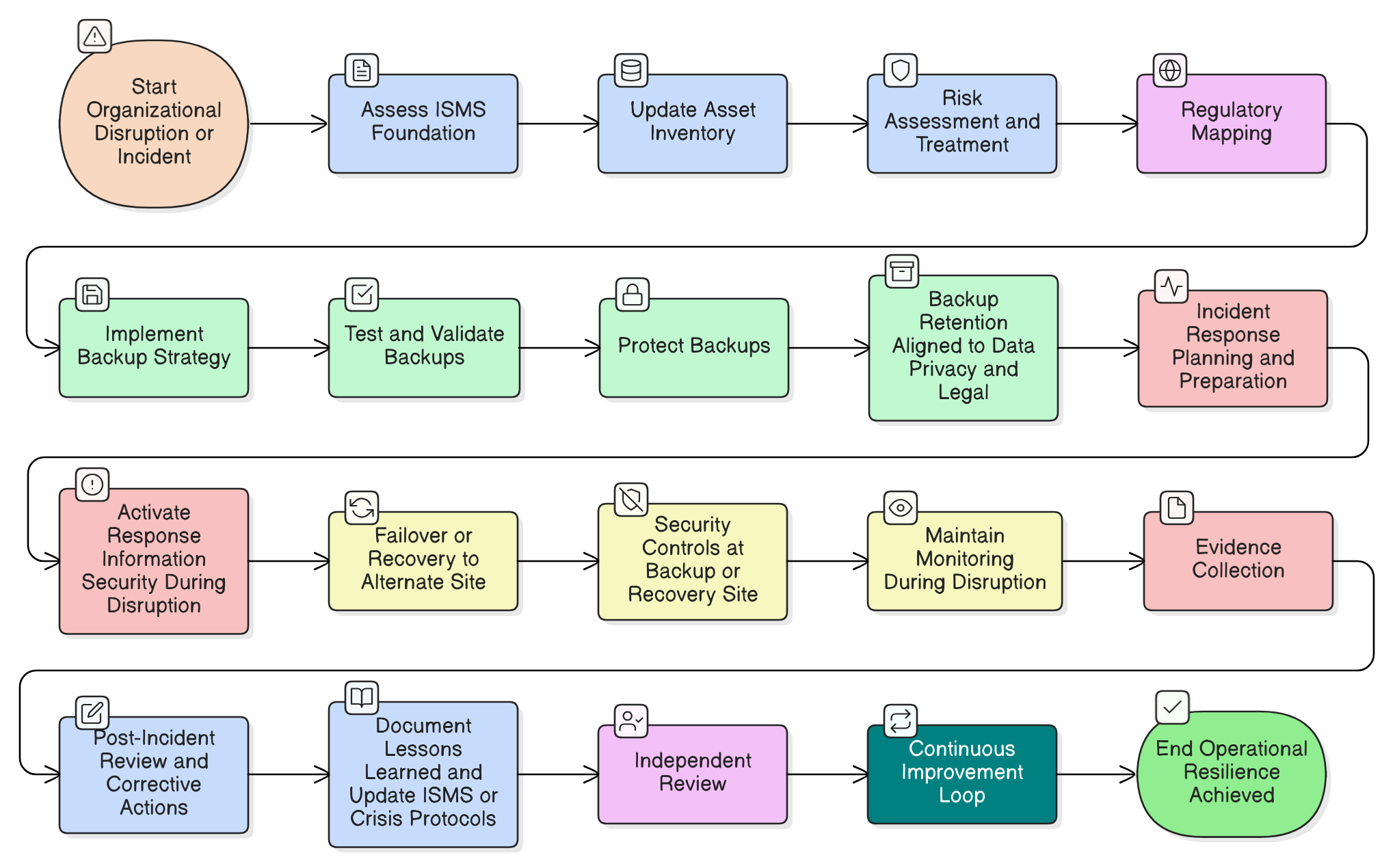
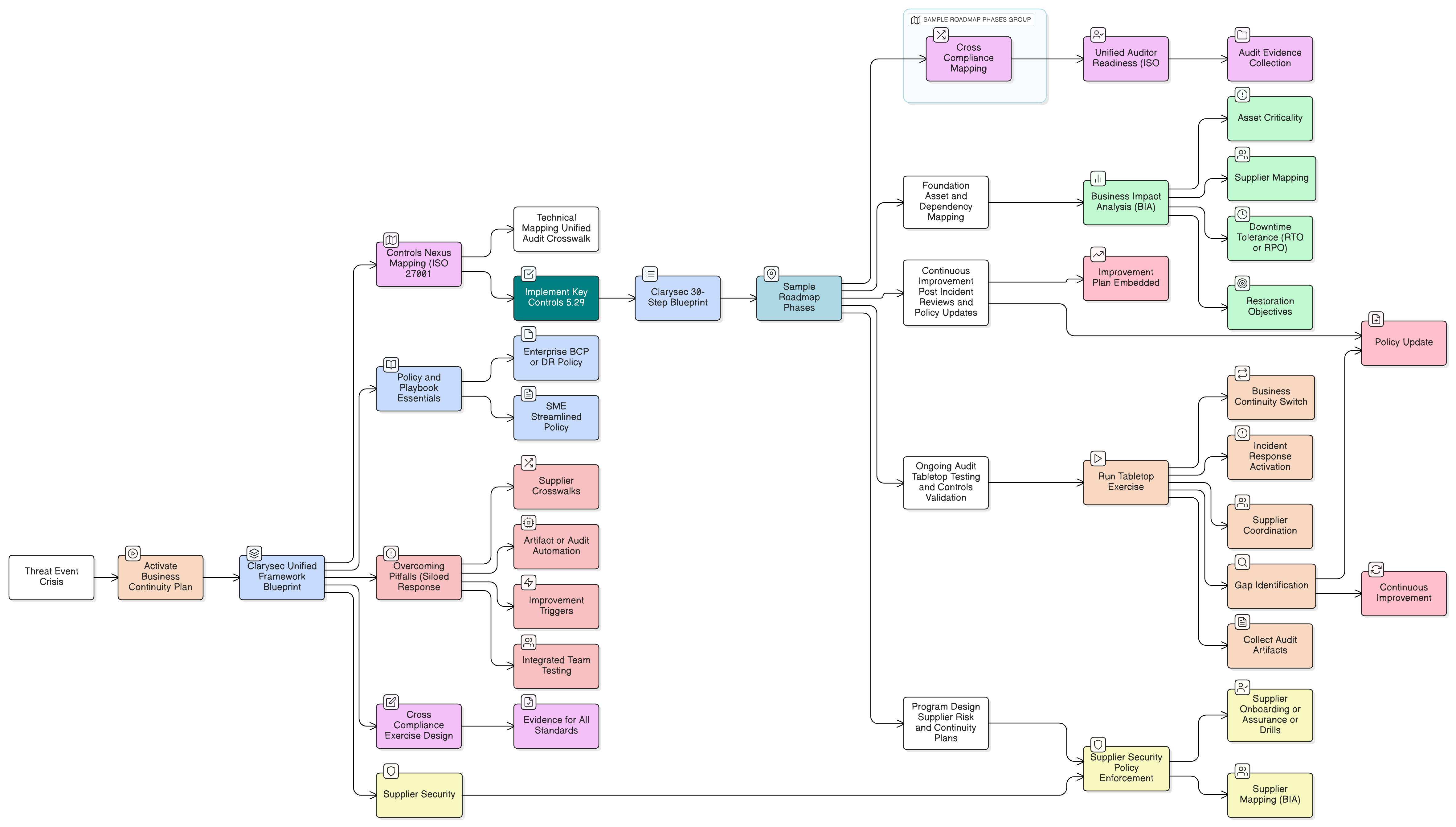
A ransomware attack hits during a board meeting. Your backups are working, but is your security? Discover how to implement ISO/IEC 27001:2022’s resilience controls to maintain security under pressure, satisfy auditors, and meet stringent DORA and NIS2 requirements with Clarysec’s expert roadmap.
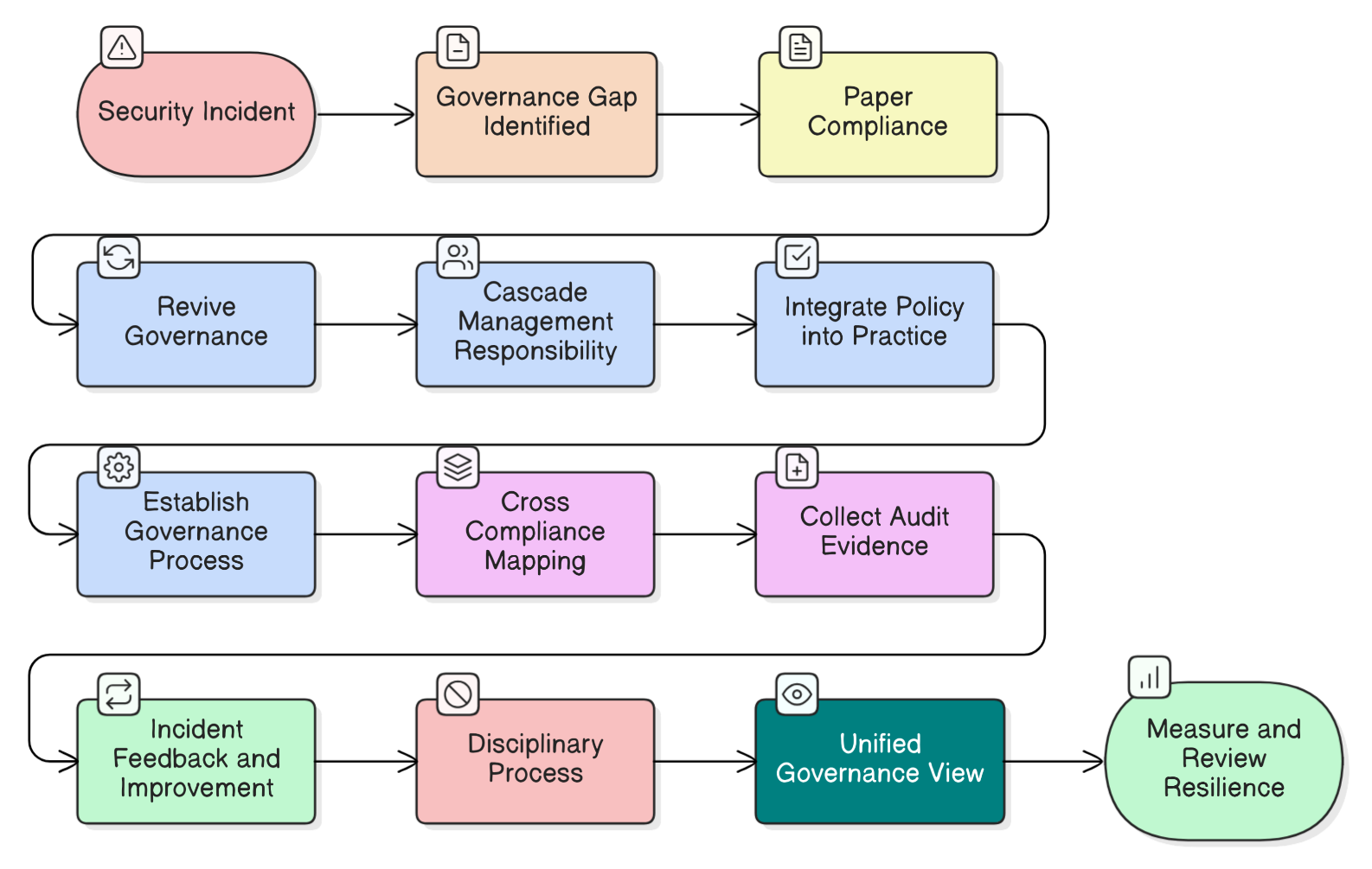
Compliance checklists don’t prevent breaches, active governance does. We break down the CISO’s biggest governance myths using a real-world incident, providing a roadmap to build true enterprise resilience with actionable steps, policy examples, and cross-compliance mappings for ISO 27001:2022, NIS2, DORA, and more.
When Simulation Meets Reality: The Crisis That Exposed Security Blind Spots
It was 2:00 PM on a Tuesday when Alex, the CISO at a fast-growing FinTech firm, was forced to stop their ransomware simulation. Sparks were flying on Slack, the board watched with growing alarm, and the DORA compliance deadline hovered menacingly. The simulation, intended to be routine, had snowballed into a showcase of vulnerabilities: entry points went undetected, critical assets weren’t prioritized, the communication plan failed, and supplier risk was murky at best.
Unify your incident response strategy for NIS2, DORA, and ISO/IEC 27001:2022 compliance with Clarysec’s tested practices, actionable mappings, and robust policies. Includes real-world scenarios, practical checklists, and evidence-generation steps for audit readiness.
CISOs and compliance leaders face new urgency from DORA and NIS2. This flagship Clarysec guide demonstrates how to build robust operational resilience, across plans, controls, supplier management, and audits, by unifying global standards with tested action steps.
A comprehensive guide to operationalizing supplier risk management, from boardroom crises to cross-framework audit triumphs, using real-world scenarios, Clarysec’s Zenith toolkits, and actionable blueprints that secure the supply chain throughout its entire lifecycle.