#ISMS
Articles tagged with "ISMS"
26 articles
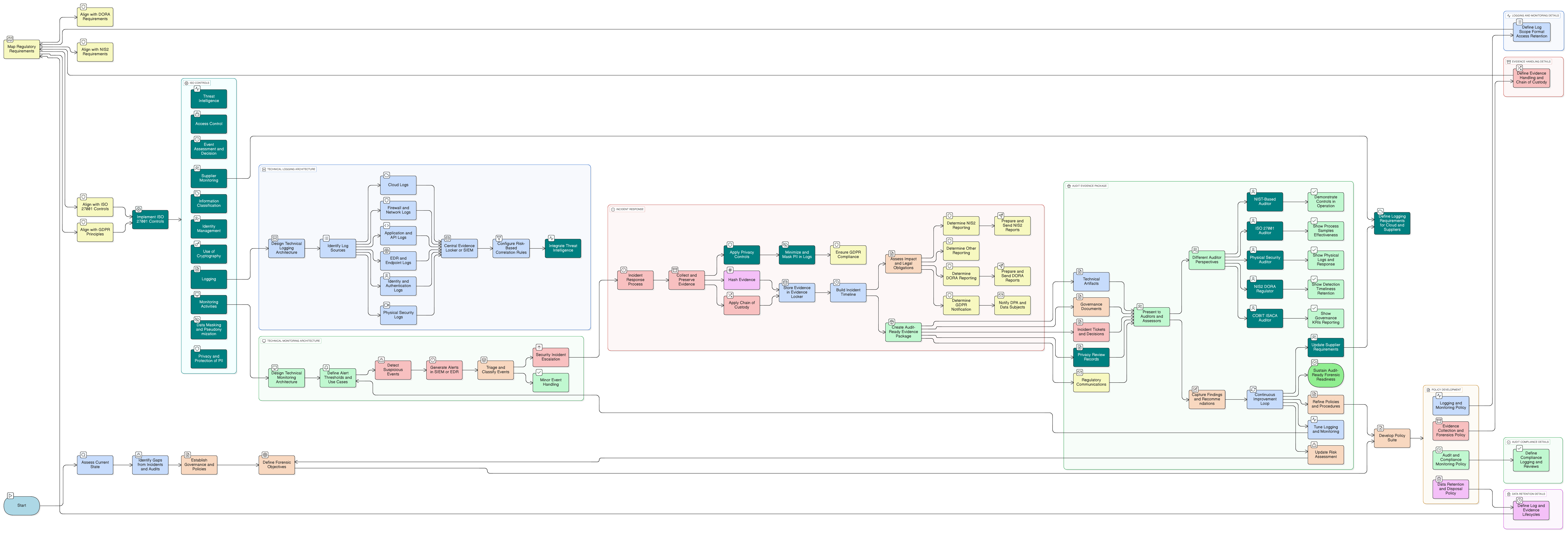
This comprehensive article provides a scenario-driven guide for CISOs on establishing a forensic readiness capability that meets stringent regulatory and audit demands across NIS2, DORA, ISO 27001, and GDPR.
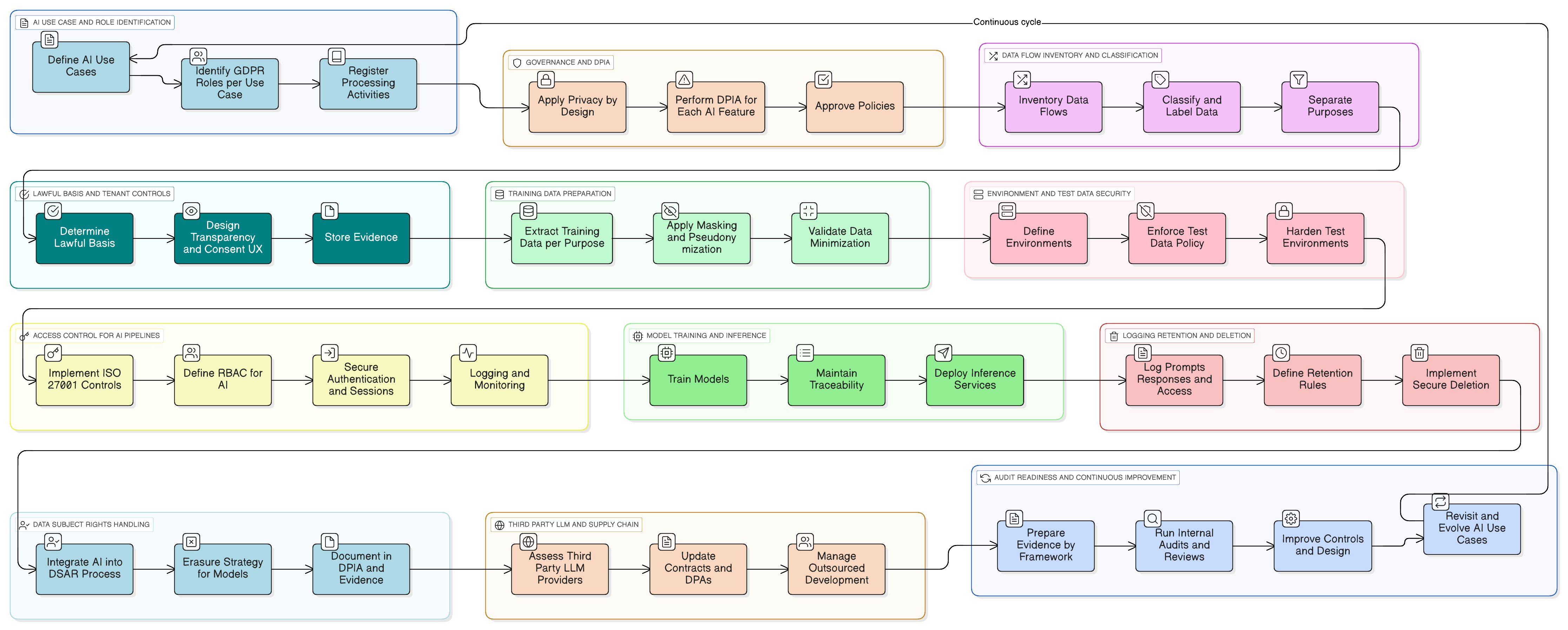
This article provides a practical playbook for CISOs to navigate the complex intersection of GDPR and AI. We offer a scenario-driven walkthrough for making SaaS products with LLMs compliant, focusing on training data, access controls, data subject rights, and multi-framework audit readiness.
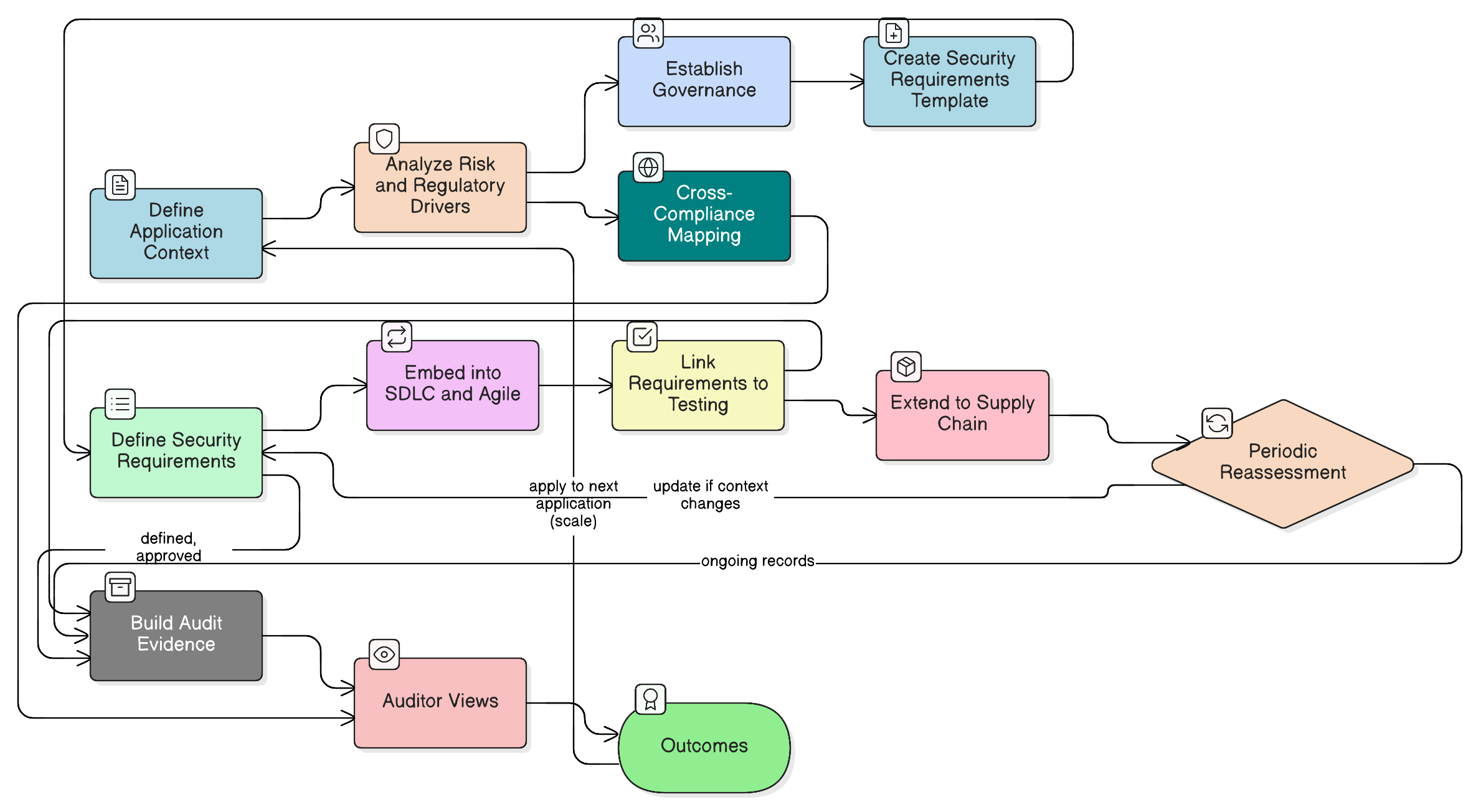
This comprehensive guide walks CISOs and security leaders through a proven methodology for mastering application security requirements. Learn to move from reactive fixes to a proactive, ‘security-by-design’ model that satisfies auditors, protects the business, and aligns with major compliance frameworks using Clarysec’s proven policies and toolkits.
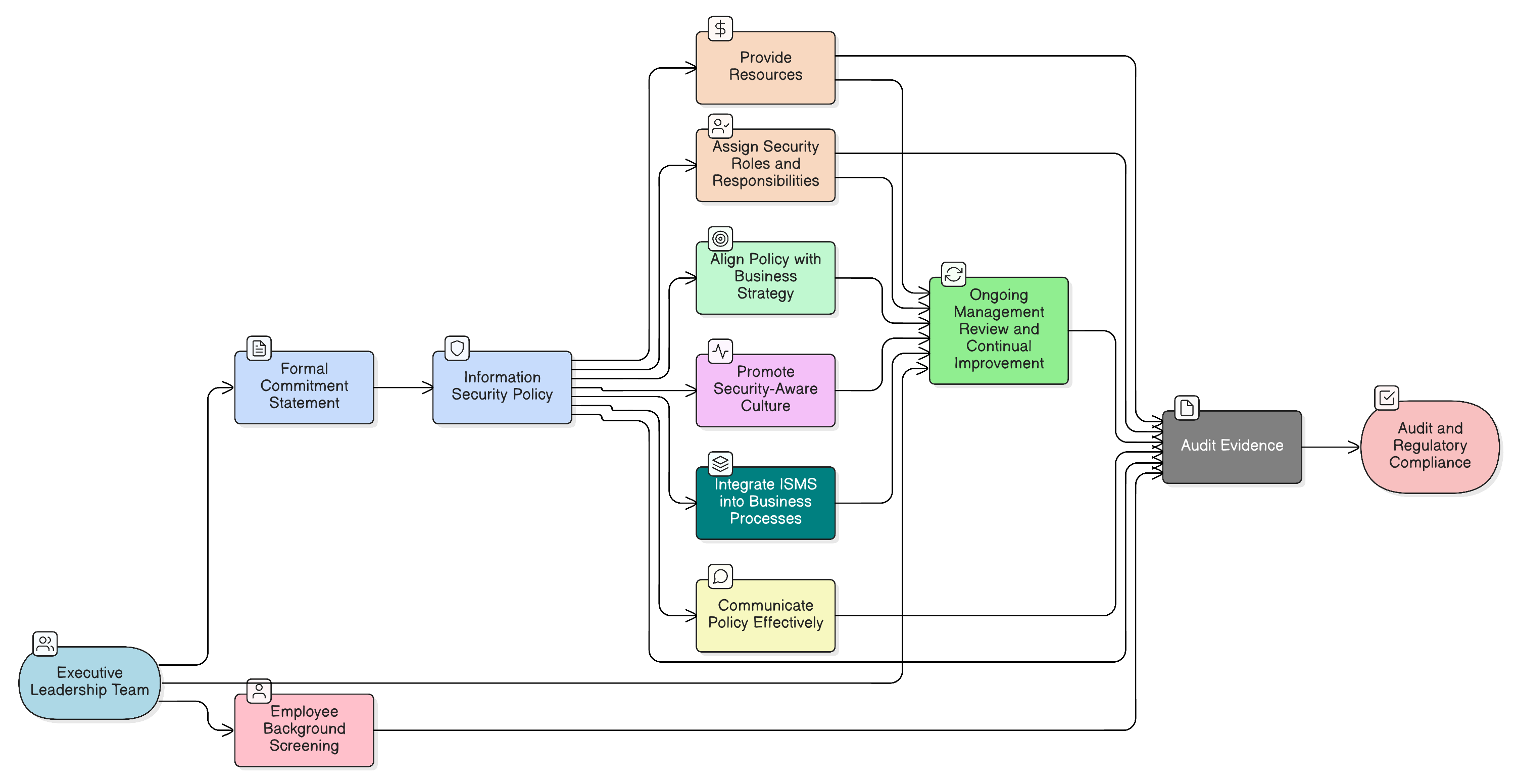
A signature on a policy is not enough. Discover how to transform executive leadership into your most powerful security asset, with actionable steps, policy examples, and cross-compliance mappings for ISO 27001:2022, NIS2, DORA, and more.
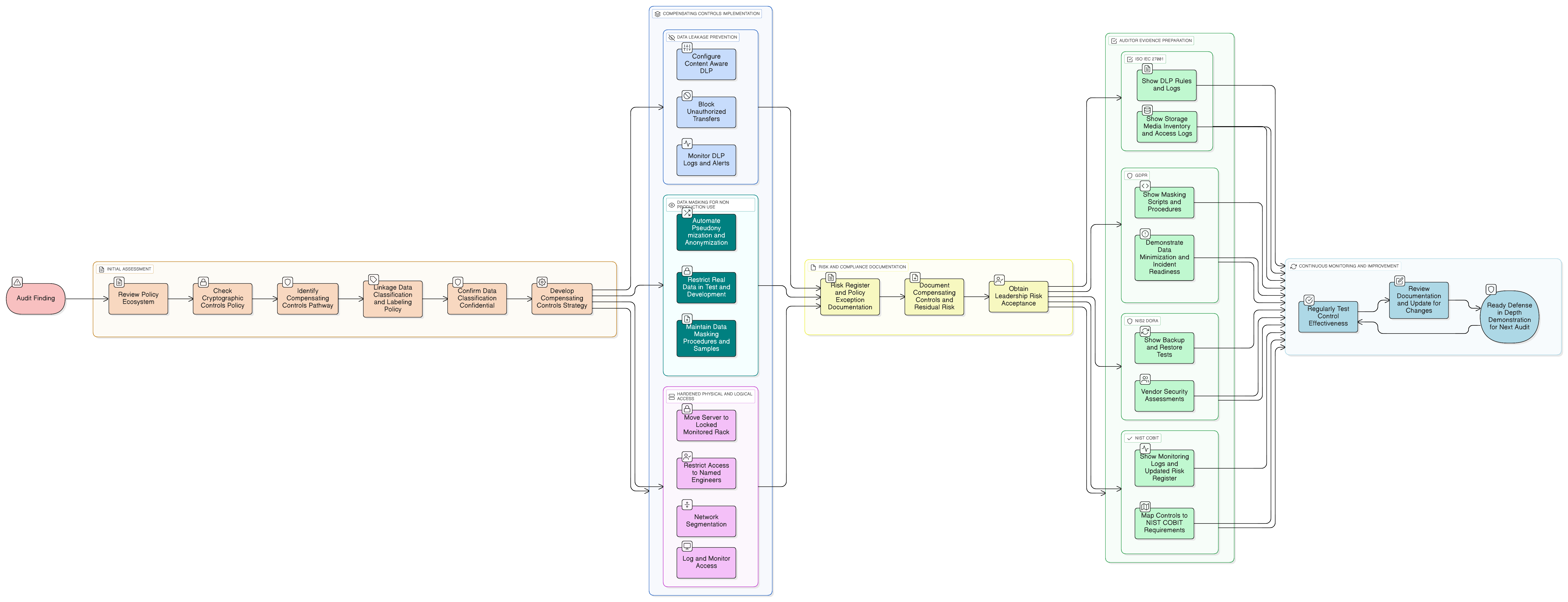
A practical guide for CISOs on implementing and documenting compensating controls for data at rest when encryption isn’t feasible. We walk through a real-world audit scenario, mapping layered defenses to ISO/IEC 27001:2022, GDPR, NIS2, DORA, and NIST frameworks.
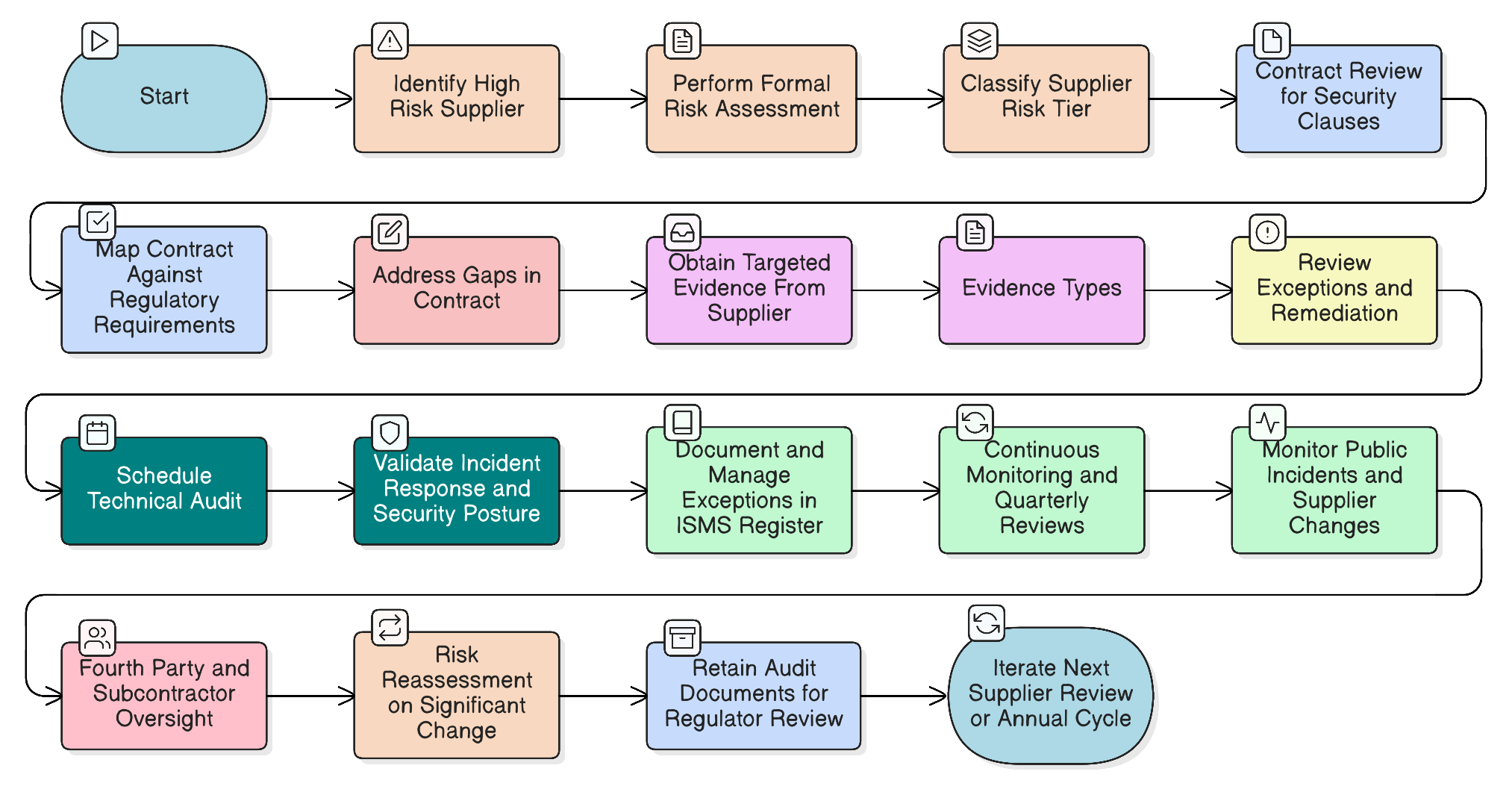
Our flagship article for CISOs on mastering high-risk supplier audits for NIS2 and DORA. Learn how to implement a risk-based, continuous audit strategy leveraging proven frameworks, policy mandates, and actionable checklists to satisfy stringent regulatory demands.
This flagship article walks CISOs and compliance leaders through a real-world approach to building a NIS2-compliant supply chain risk program. It combines regulatory insights, actionable controls, and Clarysec’s expert guidance to turn your supply chain from a critical vulnerability into a resilient, auditable asset.
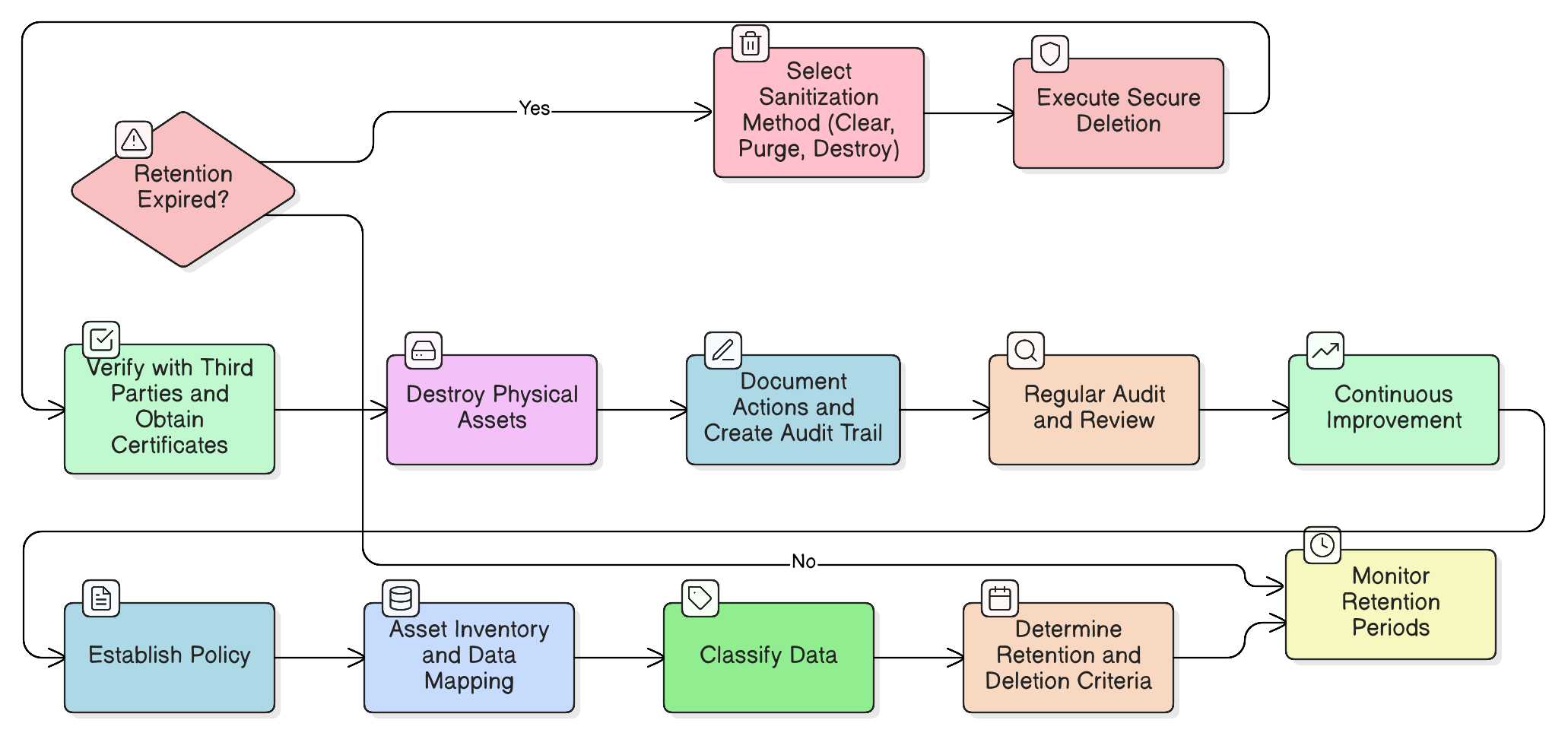
Transform your legacy data risk into a strategic advantage. This in-depth guide covers everything from policy creation and media sanitization to building an audit-proof trail for data disposal, combining Clarysec’s expert roadmaps and policy toolkits.
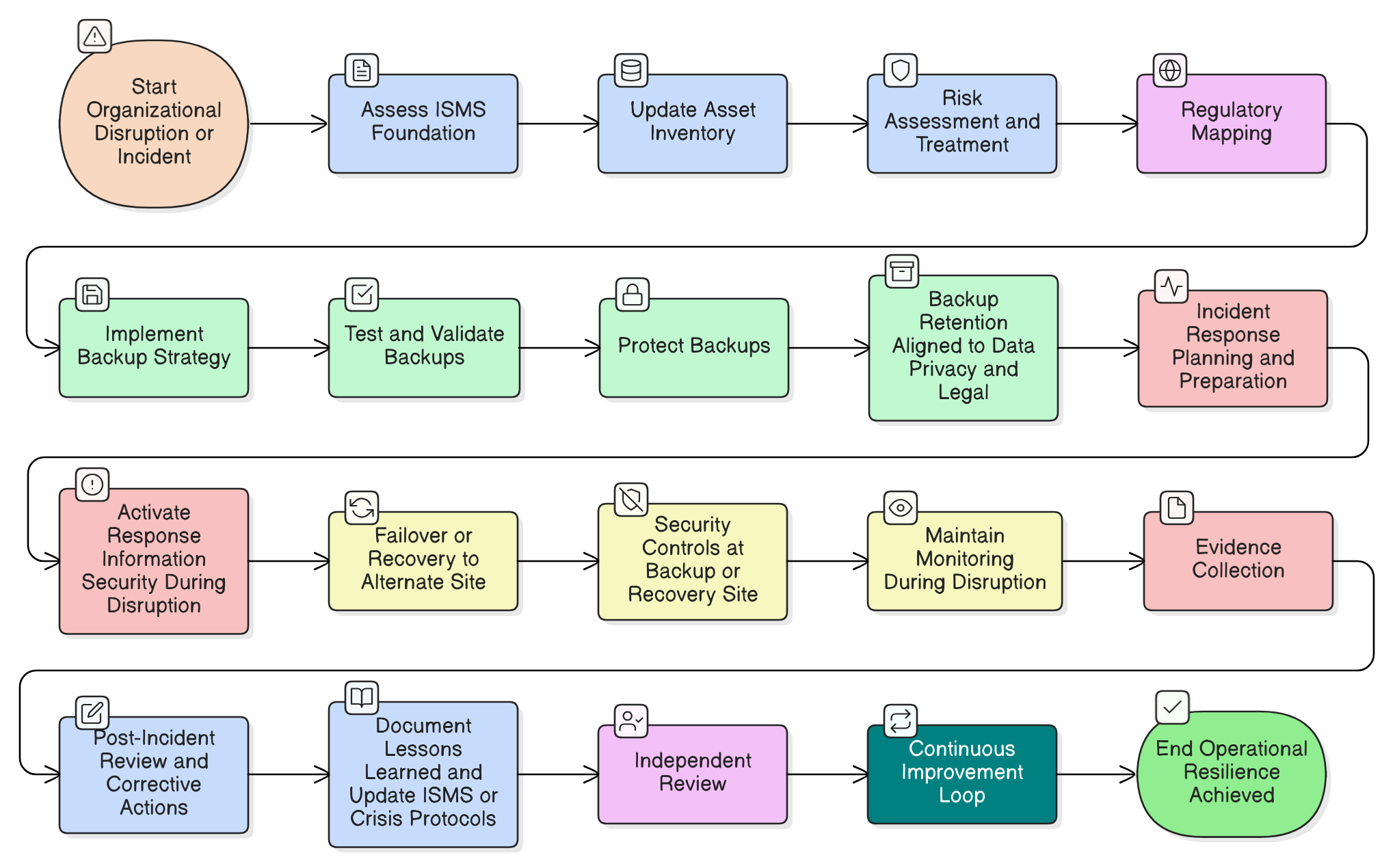
A ransomware attack hits during a board meeting. Your backups are working, but is your security? Discover how to implement ISO/IEC 27001:2022’s resilience controls to maintain security under pressure, satisfy auditors, and meet stringent DORA and NIS2 requirements with Clarysec’s expert roadmap.