#Risk Management
Articles tagged with "Risk Management"
26 articles
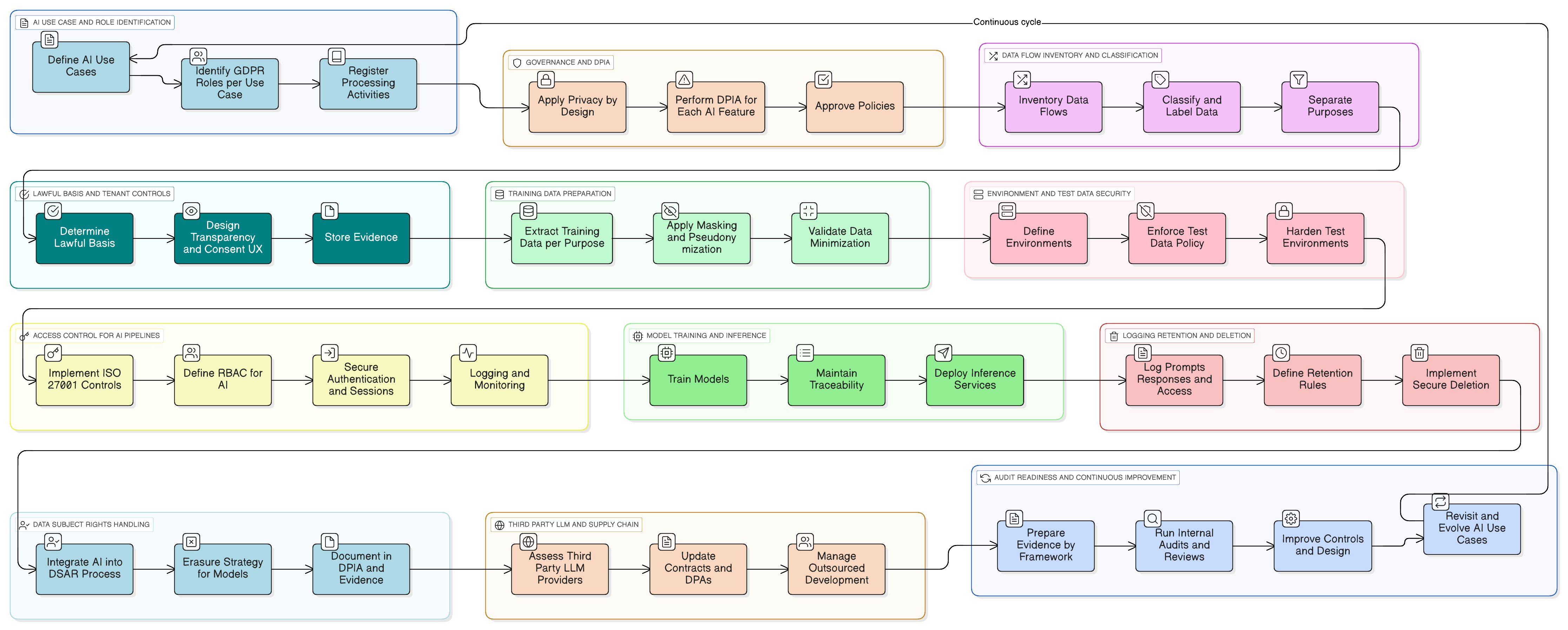
This article provides a practical playbook for CISOs to navigate the complex intersection of GDPR and AI. We offer a scenario-driven walkthrough for making SaaS products with LLMs compliant, focusing on training data, access controls, data subject rights, and multi-framework audit readiness.
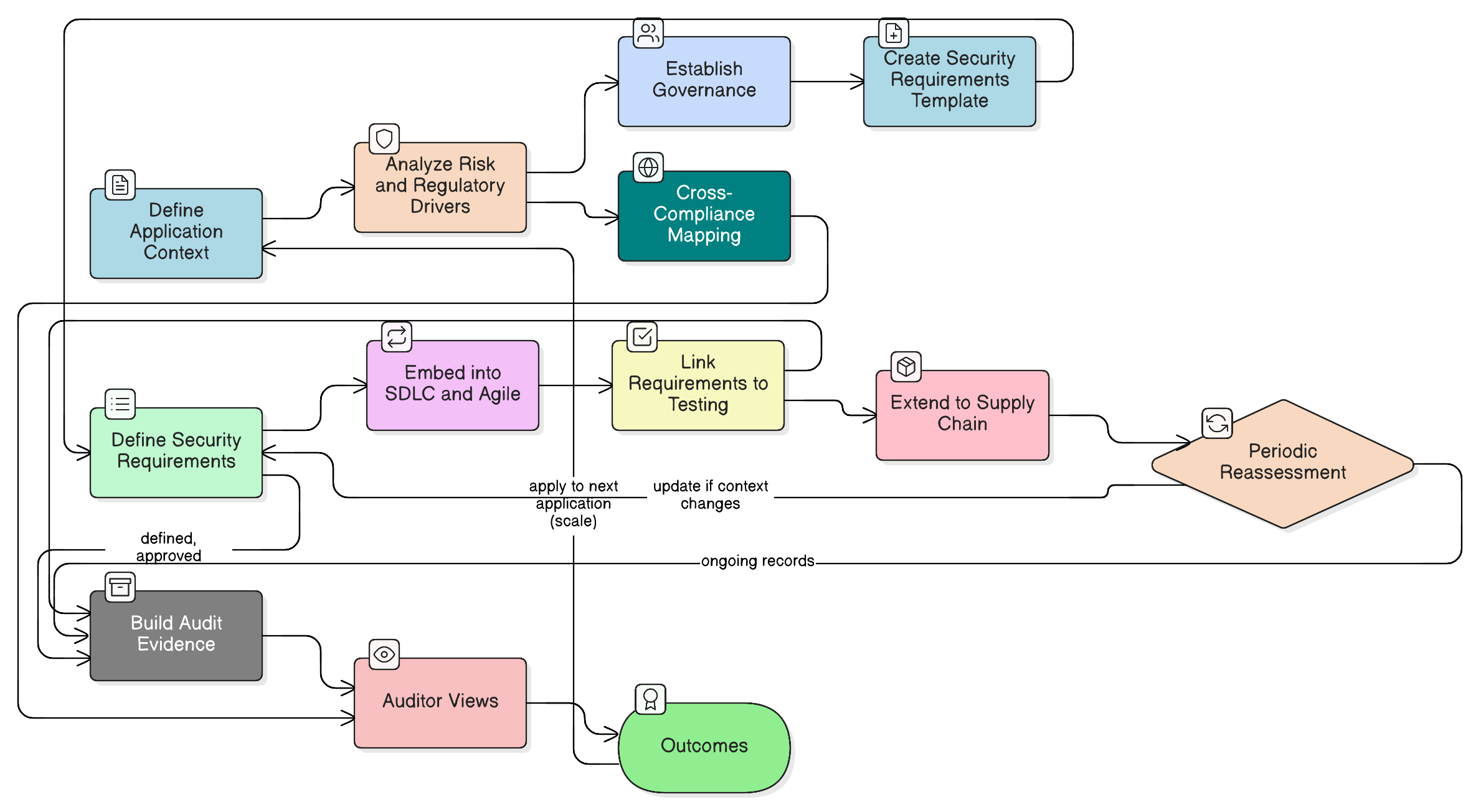
This comprehensive guide walks CISOs and security leaders through a proven methodology for mastering application security requirements. Learn to move from reactive fixes to a proactive, ‘security-by-design’ model that satisfies auditors, protects the business, and aligns with major compliance frameworks using Clarysec’s proven policies and toolkits.
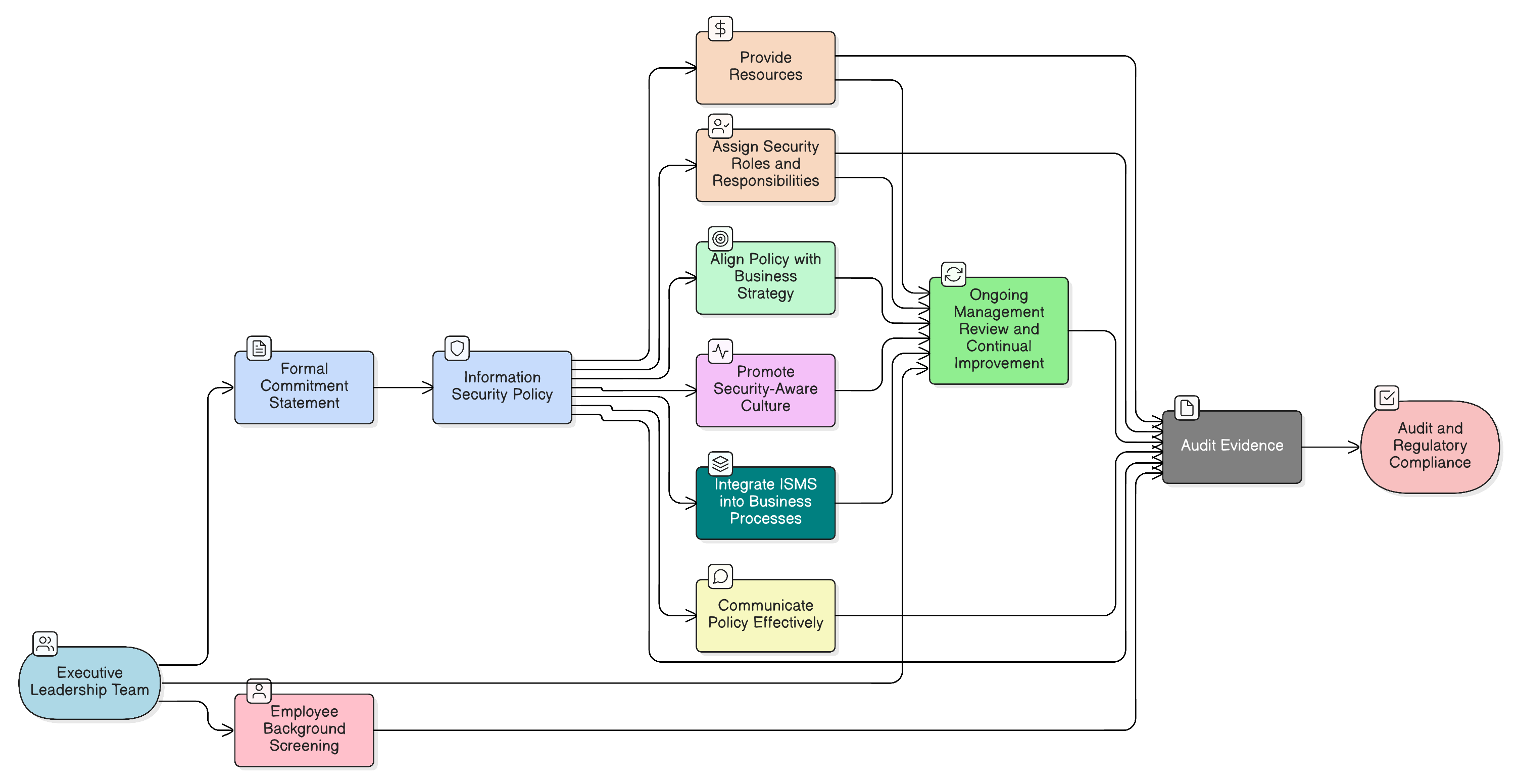
A signature on a policy is not enough. Discover how to transform executive leadership into your most powerful security asset, with actionable steps, policy examples, and cross-compliance mappings for ISO 27001:2022, NIS2, DORA, and more.
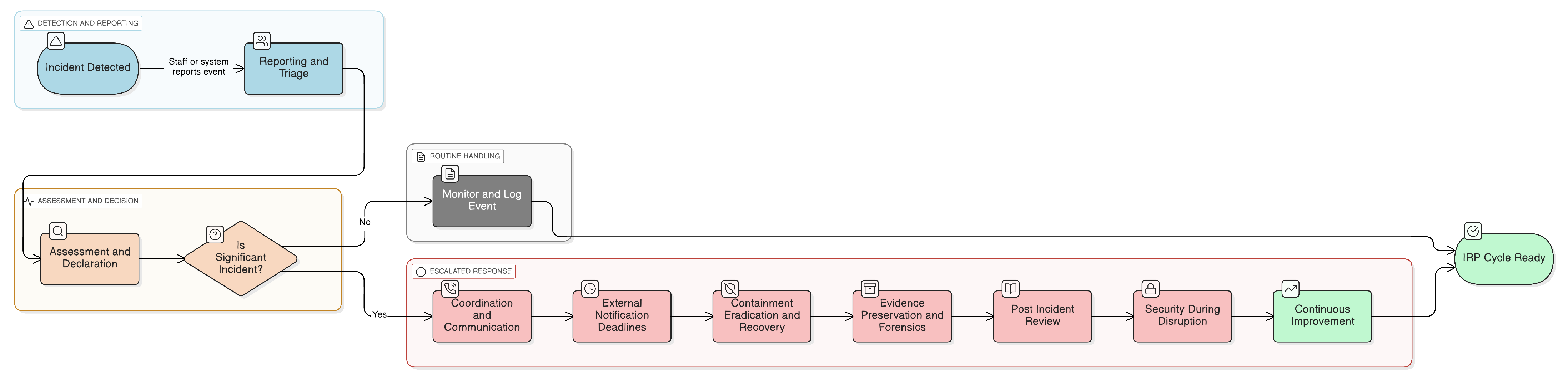
The NIS2 Directive’s 24-hour notification rule is a game-changer. This definitive guide shows CISOs and auditors how to engineer a resilient, compliant incident response plan that stands up to regulatory scrutiny and real-world attacks, using Clarysec’s policies and cross-compliance toolkits.
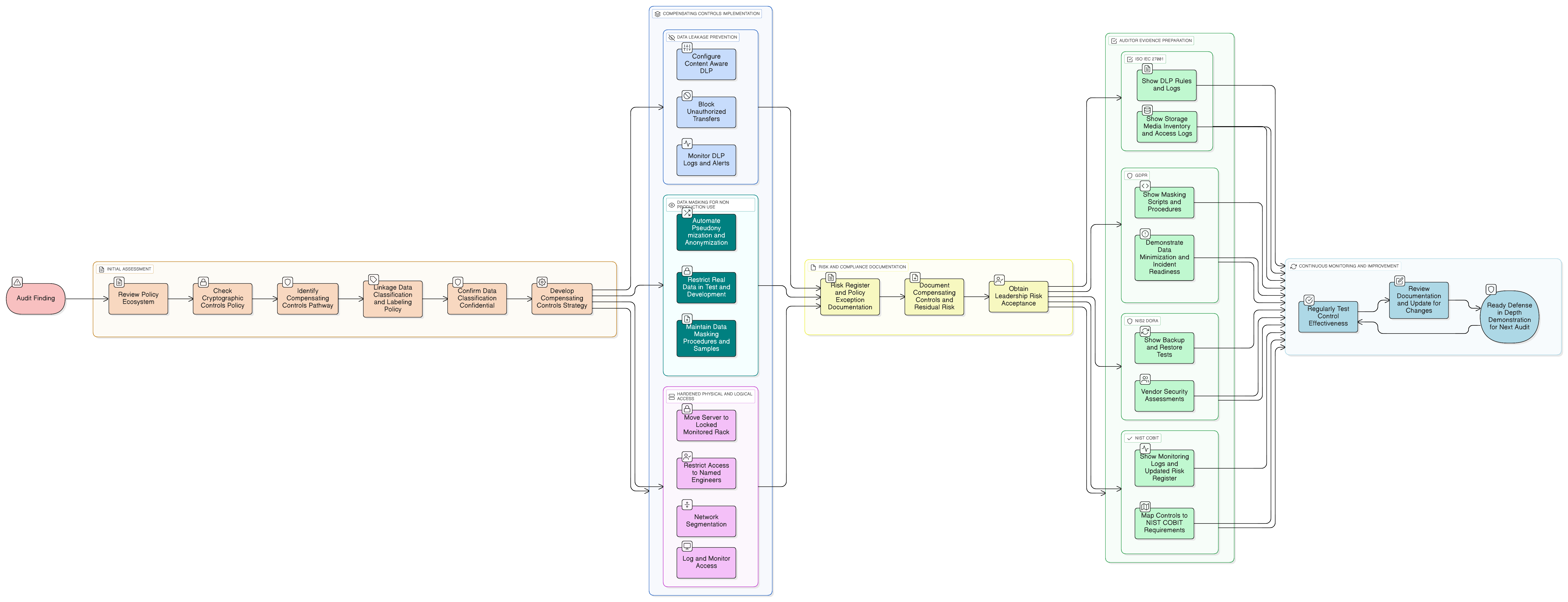
A practical guide for CISOs on implementing and documenting compensating controls for data at rest when encryption isn’t feasible. We walk through a real-world audit scenario, mapping layered defenses to ISO/IEC 27001:2022, GDPR, NIS2, DORA, and NIST frameworks.
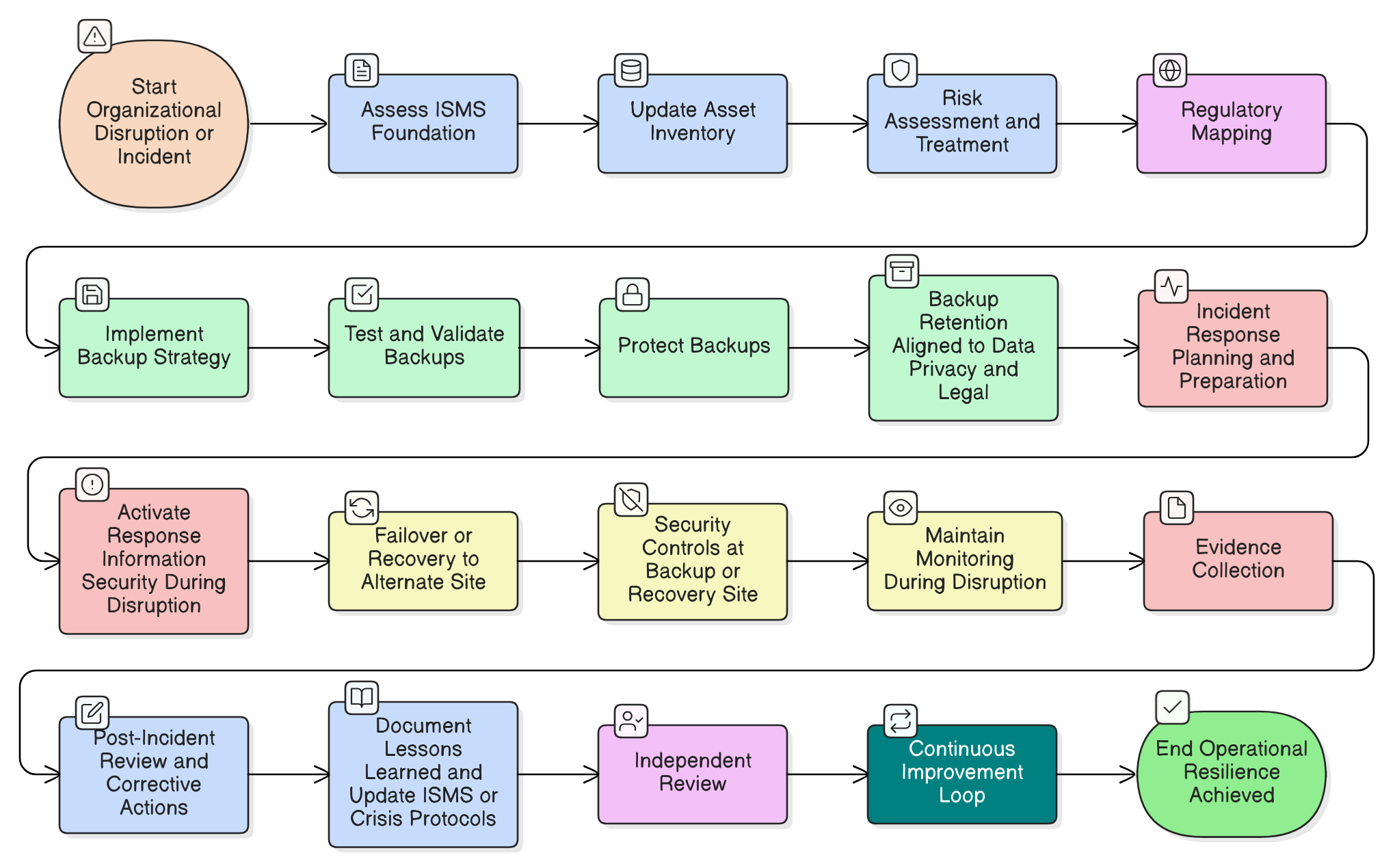
A ransomware attack hits during a board meeting. Your backups are working, but is your security? Discover how to implement ISO/IEC 27001:2022’s resilience controls to maintain security under pressure, satisfy auditors, and meet stringent DORA and NIS2 requirements with Clarysec’s expert roadmap.
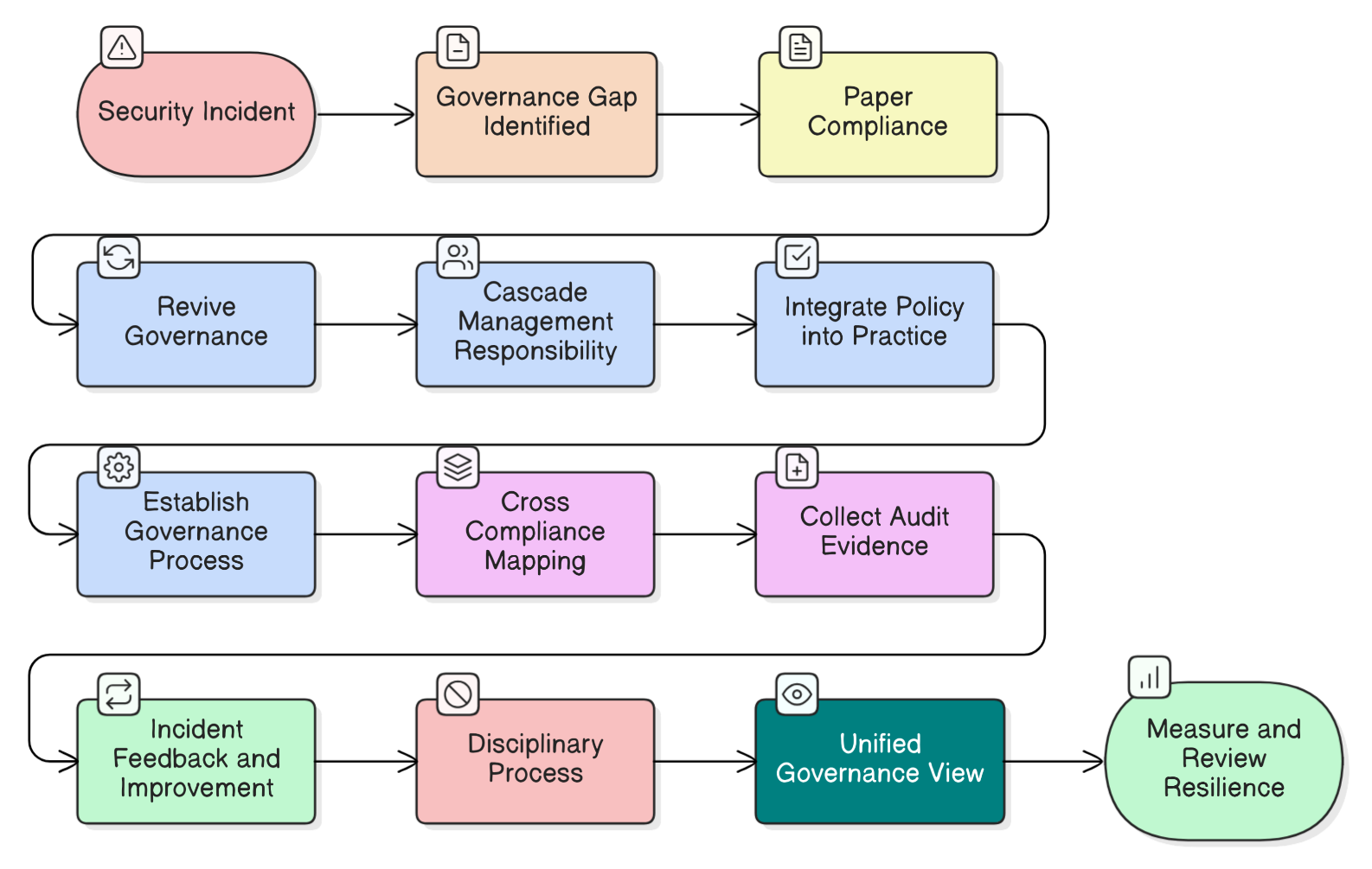
Compliance checklists don’t prevent breaches, active governance does. We break down the CISO’s biggest governance myths using a real-world incident, providing a roadmap to build true enterprise resilience with actionable steps, policy examples, and cross-compliance mappings for ISO 27001:2022, NIS2, DORA, and more.
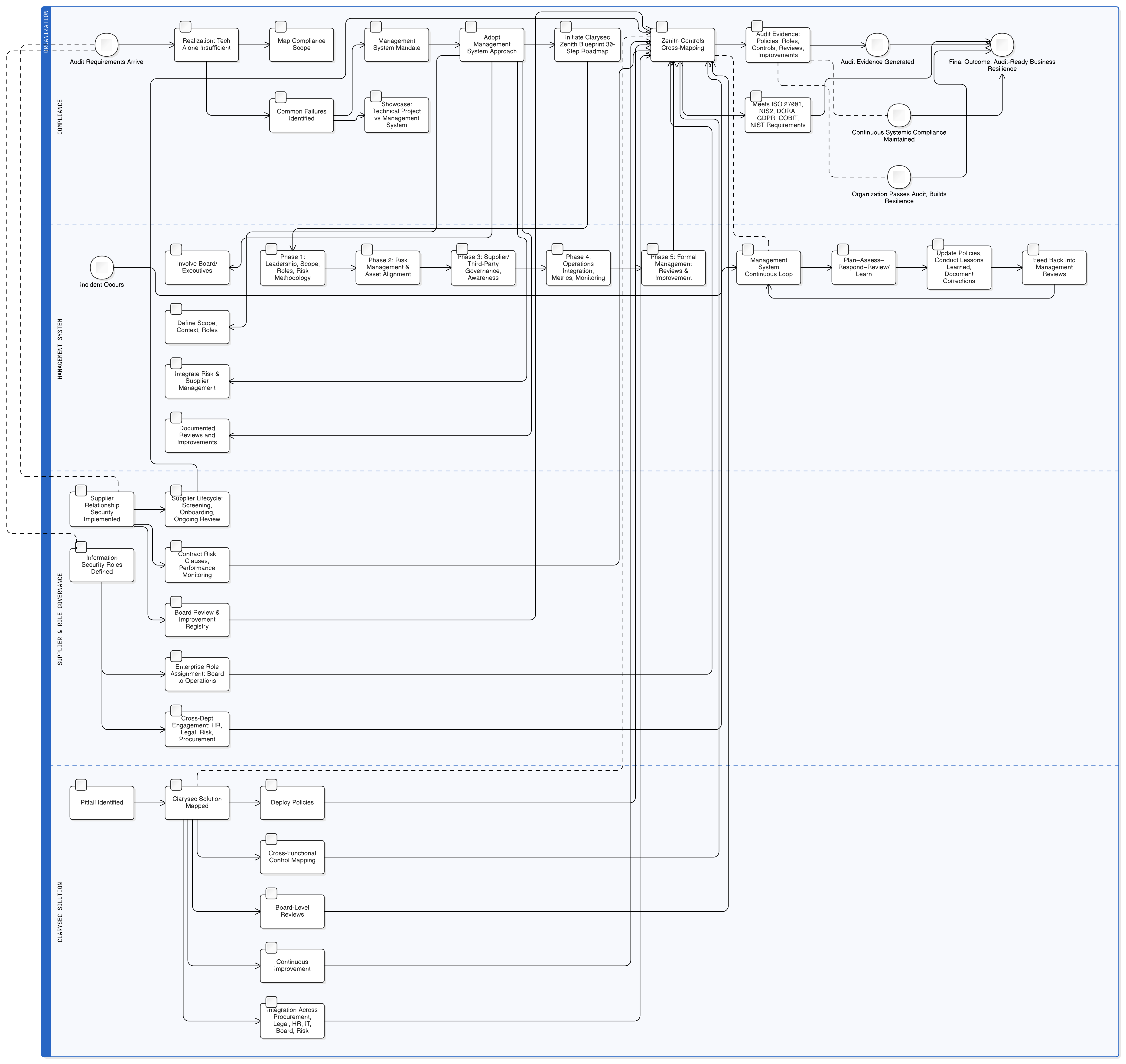
Audit disasters aren’t caused by weak firewalls, they’re the result of treating compliance as a tech checklist. Discover Clarysec’s management system strategies, mapped controls, and practical policies for seamless ISO 27001, NIS2, and DORA compliance.
When Simulation Meets Reality: The Crisis That Exposed Security Blind Spots
It was 2:00 PM on a Tuesday when Alex, the CISO at a fast-growing FinTech firm, was forced to stop their ransomware simulation. Sparks were flying on Slack, the board watched with growing alarm, and the DORA compliance deadline hovered menacingly. The simulation, intended to be routine, had snowballed into a showcase of vulnerabilities: entry points went undetected, critical assets weren’t prioritized, the communication plan failed, and supplier risk was murky at best.