#Risk Management
Articles tagged with "Risk Management"
26 articles
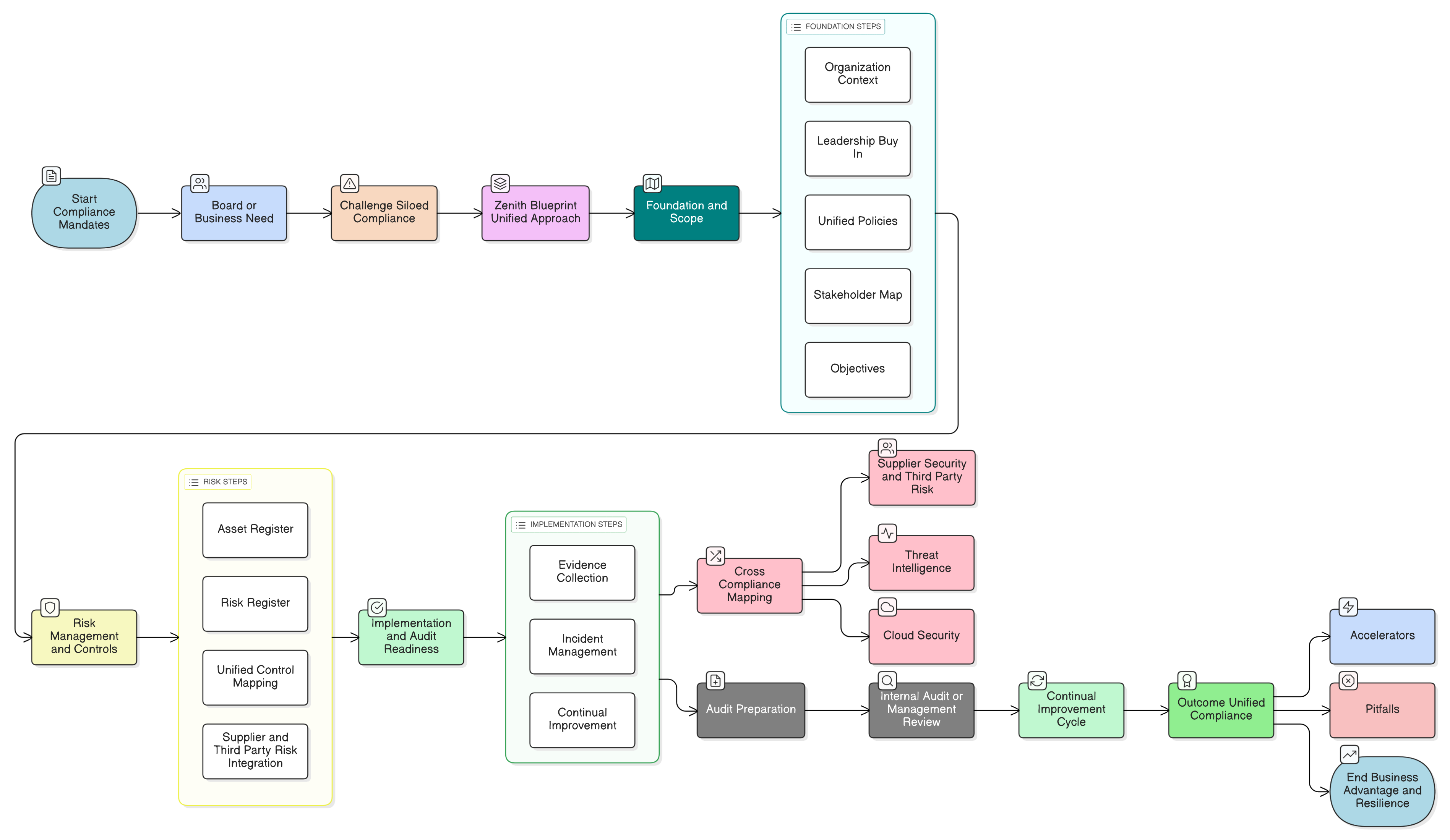
Clarysec’s Zenith Blueprint delivers the fastest and most reliable unified compliance for ISO 27001:2022, NIS2, and DORA. Discover actionable steps, control mappings, and real-world scenarios for CISOs and business leaders to achieve true audit and operational readiness.
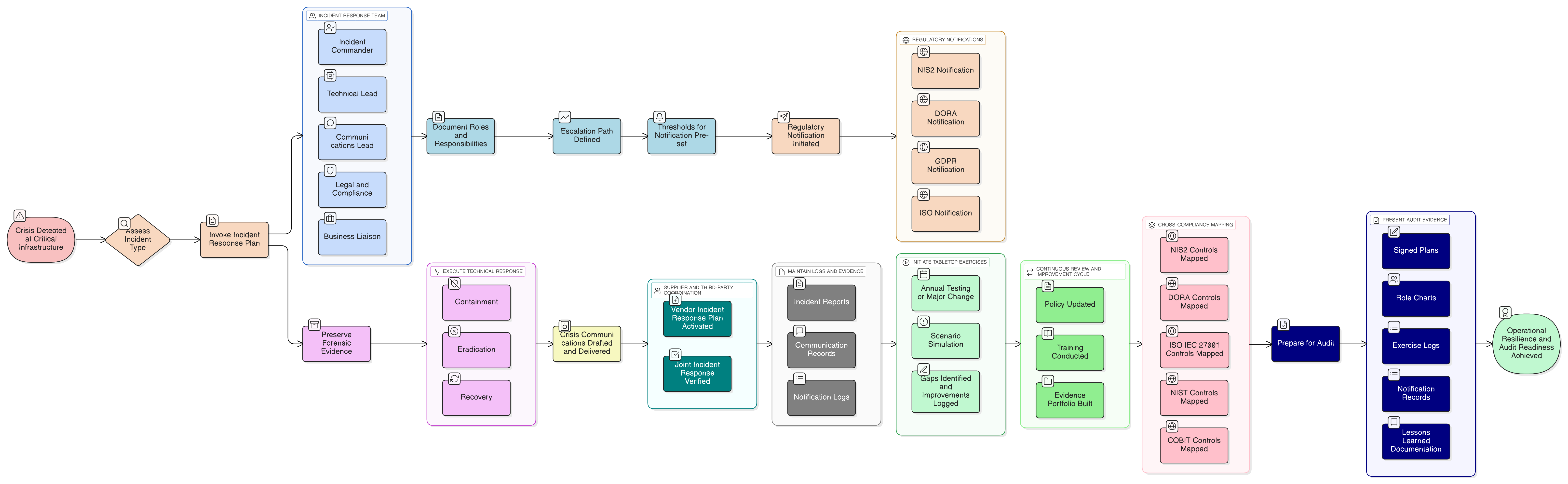
Unify your incident response strategy for NIS2, DORA, and ISO/IEC 27001:2022 compliance with Clarysec’s tested practices, actionable mappings, and robust policies. Includes real-world scenarios, practical checklists, and evidence-generation steps for audit readiness.
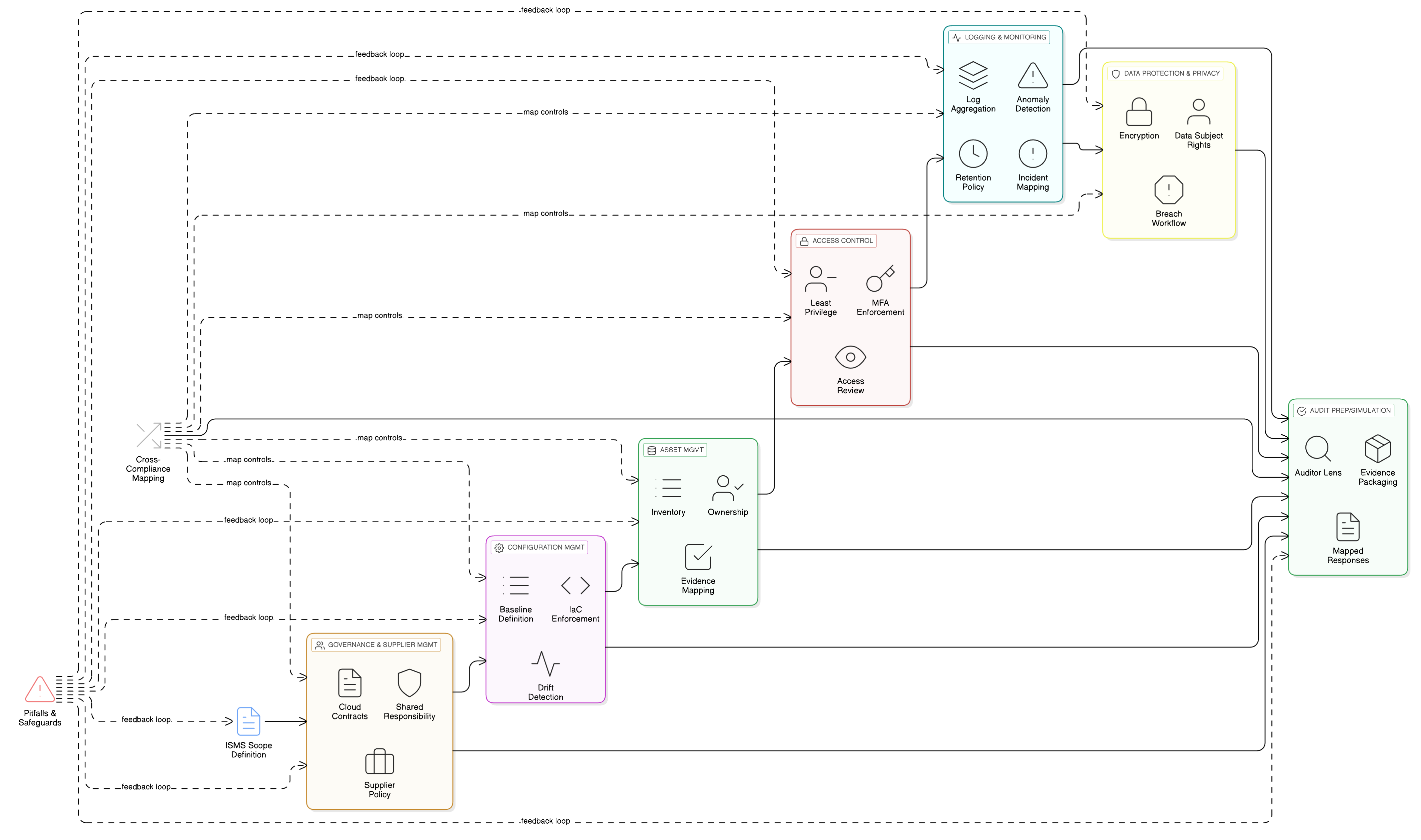
CISOs, compliance managers, and cloud architects: discover how to operationalize ISO 27001:2022 cloud controls for perpetual compliance. Real-world stories, technical mapping tables, and actionable blueprints from Clarysec unite security, governance, and audit-readiness across frameworks.
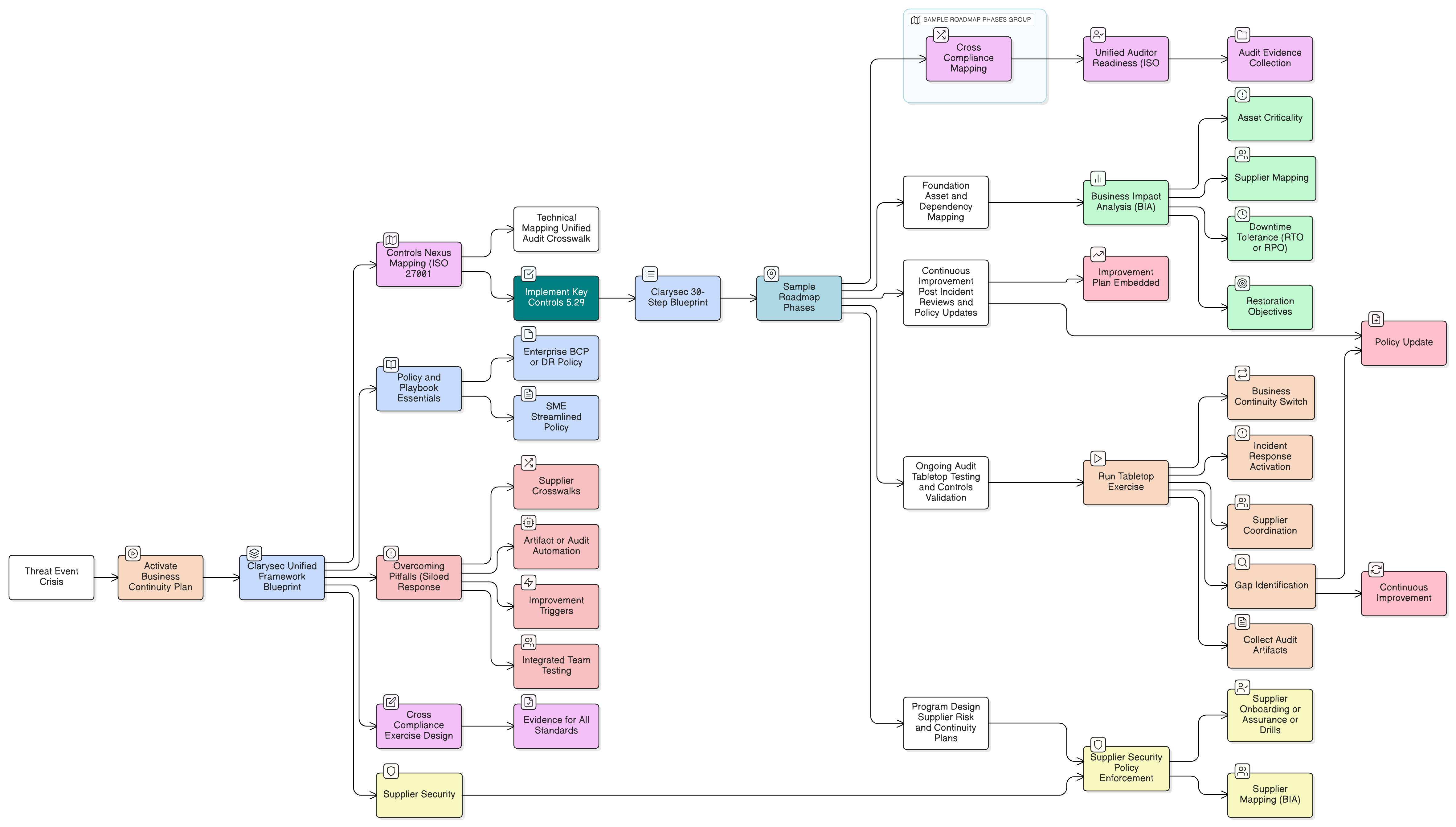
CISOs and compliance leaders face new urgency from DORA and NIS2. This flagship Clarysec guide demonstrates how to build robust operational resilience, across plans, controls, supplier management, and audits, by unifying global standards with tested action steps.
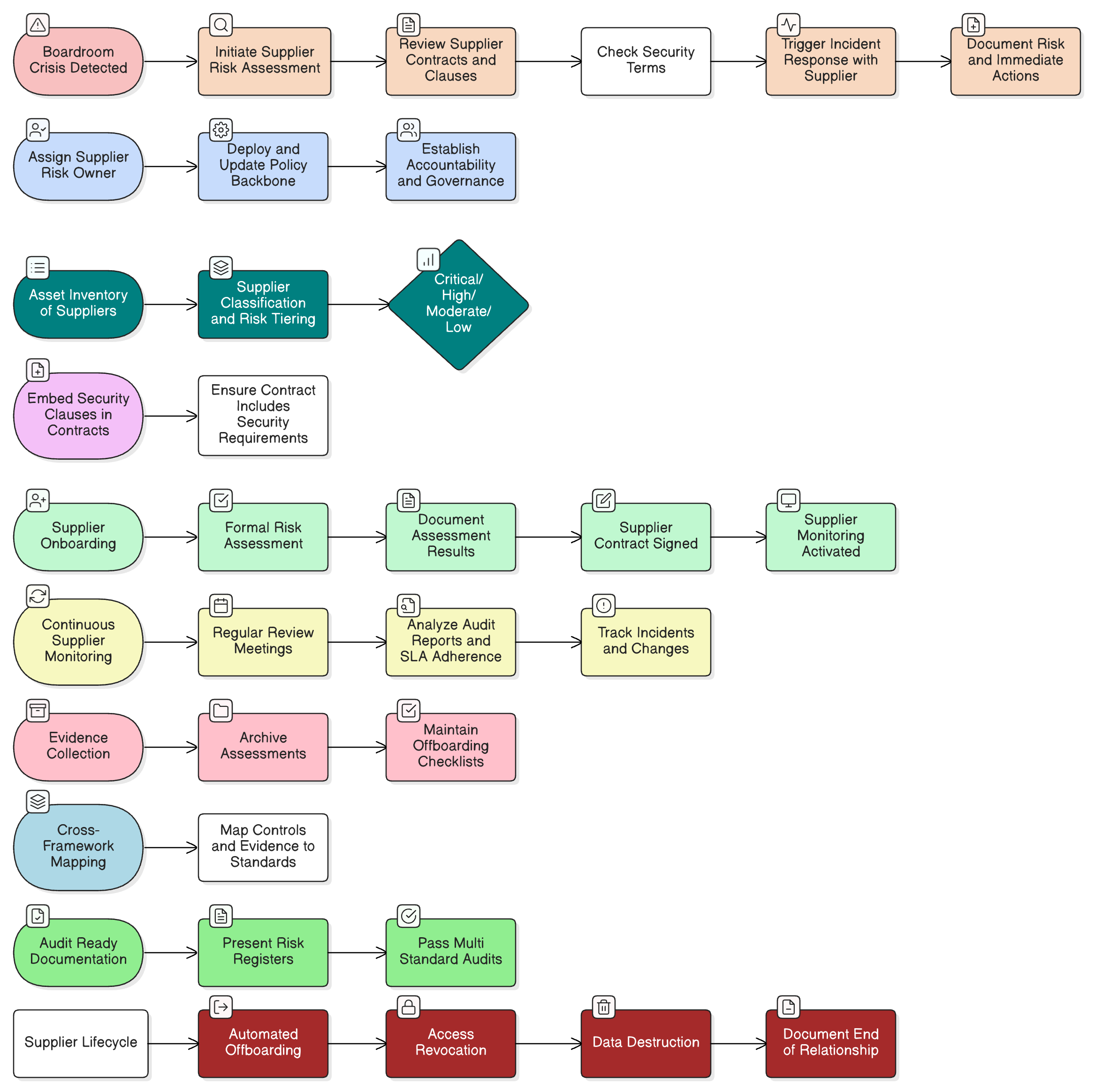
A comprehensive guide to operationalizing supplier risk management, from boardroom crises to cross-framework audit triumphs, using real-world scenarios, Clarysec’s Zenith toolkits, and actionable blueprints that secure the supply chain throughout its entire lifecycle.
Master ISO 27001 incident response with our CISO’s guide. Learn from a real-world manufacturing scenario, from preparation to post-breach analysis and compliance.
A guide for manufacturers on building a robust, ISO 27001-aligned incident response plan to protect operations and ensure compliance.
Uncover the truth behind the top 7 GDPR myths of 2025. Our expert guide debunks common misconceptions about consent, data breaches, and compliance.
The EU’s NIS2 Directive and DORA Regulation are transforming cybersecurity compliance. This guide breaks down their impact and provides a practical path to readiness.